Help trying to get EAP-TLS working (Pfsense / Unifi)
-
@alnico If radsniff doesn't show anything radius requests aren't hitting your router.
[2.4.5-RELEASE][admin@pfsense.xxxxxxx.net]/root: radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 pppoe0 igb1 ovpnc1 igb0.2 ovpnc2 igb0.3 ovpnc3 igb0.4 igb0.5 igb0.6 igb0.7 igb0.9 igb0.11 lo0 pflog0 igb2 igb3 igb4 igb5) 2021-01-27 10:01:22.364260 (1) Access-Request Id 165 igb0:172.16.1.11:56877 -> 172.16.0.1:1812 +0.000 User-Name = "andyk" NAS-IP-Address = 172.16.1.11 Service-Type = Framed-User Framed-MTU = 1400 Called-Station-Id = "A2-2A-A8-98-9D-8C:L-Space RADIUS" Calling-Station-Id = "40-9C-28-A2-E0-7E" NAS-Identifier = "a22aa8989d8c" NAS-Port-Type = Wireless-802.11 Acct-Session-Id = "1144BCBA29D7B258" Acct-Multi-Session-Id = "554A8AF77C09B840" Connect-Info = "CONNECT 0Mbps 802.11b" EAP-Message = 0x029e000a01616e64796b Message-Authenticator = 0xb7eeadb31283e15a427c4d5c75d5b0aa WLAN-Pairwise-Cipher = 1027076 WLAN-Group-Cipher = 1027076 WLAN-AKM-Suite = 1027073 Authenticator-Field = 0x3c008709e2d48bd8beb64afdded32fba 2021-01-27 10:01:22.371210 (2) Access-Challenge Id 165 igb0:172.16.1.11:56877 <- 172.16.0.1:1812 +0.000 +0.000 State = 0x70c07eb4705f677d3e006abac136d6d9 EAP-Message = 0x019f00061920 Message-Authenticator = 0x869a29563272722653e6bfb1aed13cea Authenticator-Field = 0xe633d547195ee13f9163c1684b7fa6a1 2021-01-27 10:01:22.102423 (3) Access-Request Id 166 igb0:172.16.1.11:56877 -> 172.16.0.1:1812 +0.065 User-Name = "andyk" NAS-IP-Address = 172.16.1.11 Service-Type = Framed-User Framed-MTU = 1400 State = 0x70c07eb4705f677d3e006abac136d6d9 Called-Station-Id = "A2-2A-A8-98-9D-8C:L-Space RADIUS" Calling-Station-Id = "40-9C-28-A2-E0-7E" NAS-Identifier = "a22aa8989d8c" NAS-Port-Type = Wireless-802.11 Acct-Session-Id = "1144BCBA29D7B258" Acct-Multi-Session-Id = "554A8AF77C09B840" Connect-Info = "CONNECT 0Mbps 802.11b" EAP-Message = 0x029f00a119800000009716030100920100008e0303601139f2571834ca6ebc5341a674636aa379c3a9370ff71263f82291b053158500002c00ffc02cc02bc024c023c00ac009c008c030c02fc028c027c014c013c012009d009c003d003c0035002f000a01000039000a00080006001700180019000b00020100000d00120010040102010501060104030203050306030005000501000000000012000000170000 Message-Authenticator = 0x8b989303eae341b82a73953e5e15c8be WLAN-Pairwise-Cipher = 1027076 WLAN-Group-Cipher = 1027076 WLAN-AKM-Suite = 1027073 Authenticator-Field = 0xd5b7f3c7255c764eecc669418304edcb 2021-01-27 10:01:22.108220 (4) Access-Challenge Id 166 igb0:172.16.1.11:56877 <- 172.16.0.1:1812 +0.071 +0.005 State = 0x70c07eb47160677d3e006abac136d6d9 EAP-Message = 0x01a003ec19c0000008b11603030039020000350303d180b5cd149369b218ab4d8b7d1c6fa5b7f1569be5b2469af54db92fad99d9d600c03000000dff01000100000b00040300010216030307130b00070f00070c0003d2308203ce308202b6a003020102020101300d06092a864886f70d01010b0500301a311830160603550403130f4e6574776f726b476e6f6d65204341301e170d3230303332373131353531305a170d3231303432383131353531305a30223120301e060355040313174e6574776f726b476e6f6d65204672656552414449555330820122300d06092a864886f70d01010105000382010f003082010a0282010100b29d6caac4fab1822c0bc0546e449293a28475b48fa7576fae0c59f9f8b6319d19582d66841b2d727fd7231420c68d470a0f57b14335efc1ffc54b8cd5fc8a6db56a83e1e533e16fe55e4453703e786d6a0f87bfd4bedfef7c5c15eef935360b04ac675e6becc83056f0604c11f0a9d3ca253335deb31e82f6642ab53e13d8dd483e444365ed852b3508e1c390f212d4b7d7c4efb387dfd32f4bb446c6ad16a92063b46ea3dbf10f19e9b3d20f999390d5c0ad4c439e07f03ff8595053f47b0631b85ccbf9ad0b237c84ed10e865da2a46faea4e3fb4df6198e3a77b160fd1467e05c3dade622a9c50da3ee23c577ec139bc997b1d42185503a71df2b4c0ab5 Message-Authenticator = 0xc1a12306ccc180dfa7d77c416b94ce21 Authenticator-Field = 0xceb2c5b0a11d650b8a51df2b97a6105aAlso try a radtest while running radsniff -x
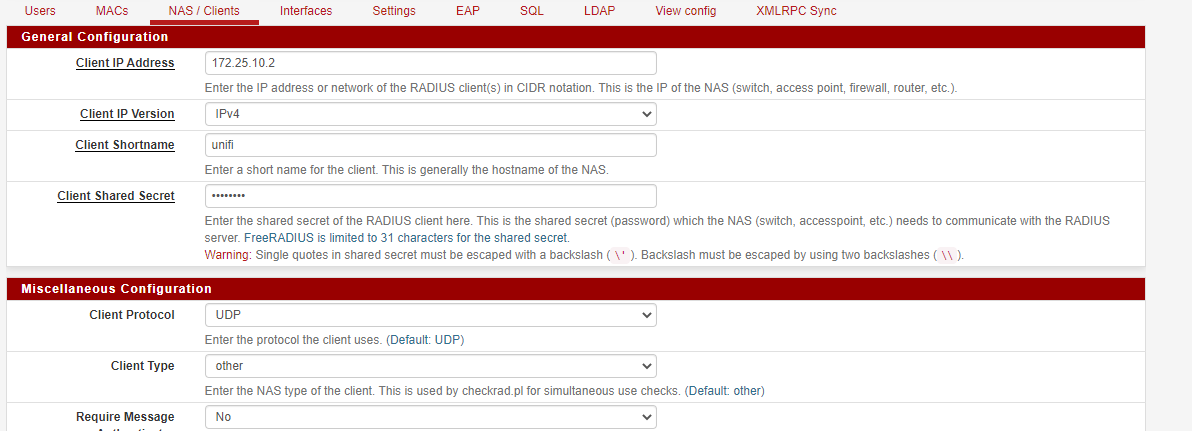
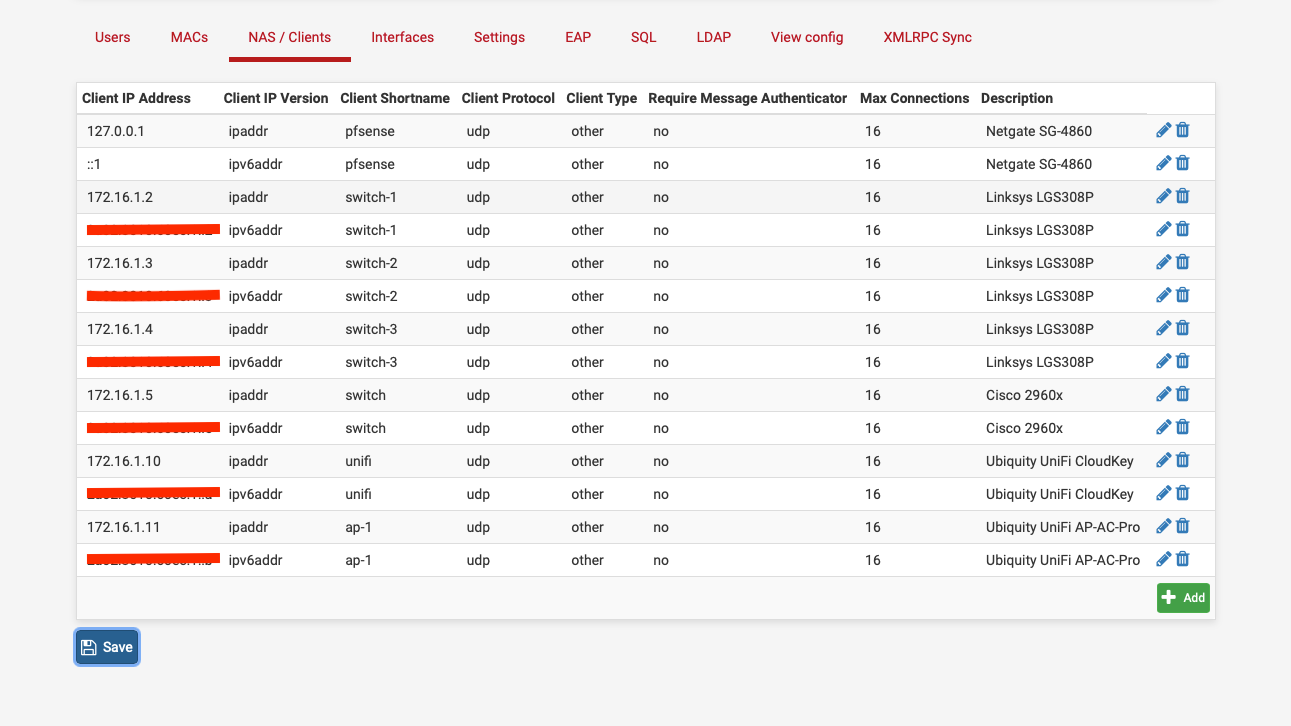
What does your NAS / Client view look like, it should be something like this, radius requests come from the Unifi APs rather than the controller:-
Another reason why Ubiquity will never make it big in the enterprise market.
-
I'd try to get radtest working from the pfSense box first.
-
Thanks @NogBadTheBad
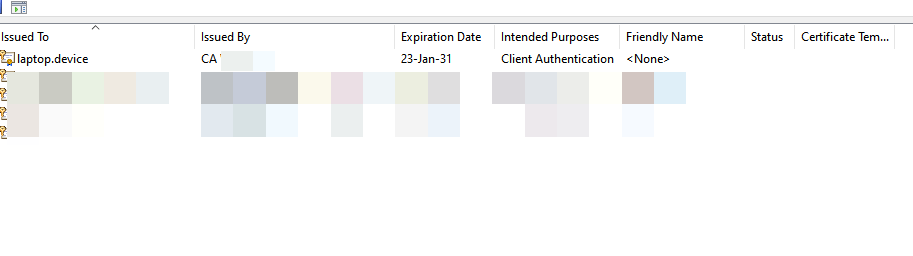
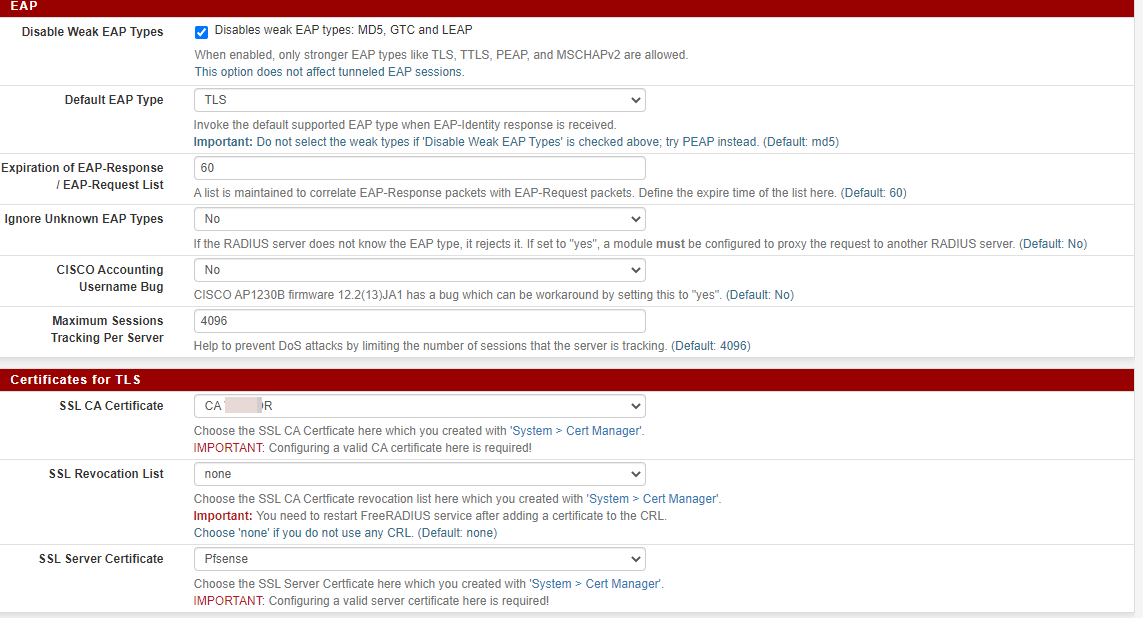
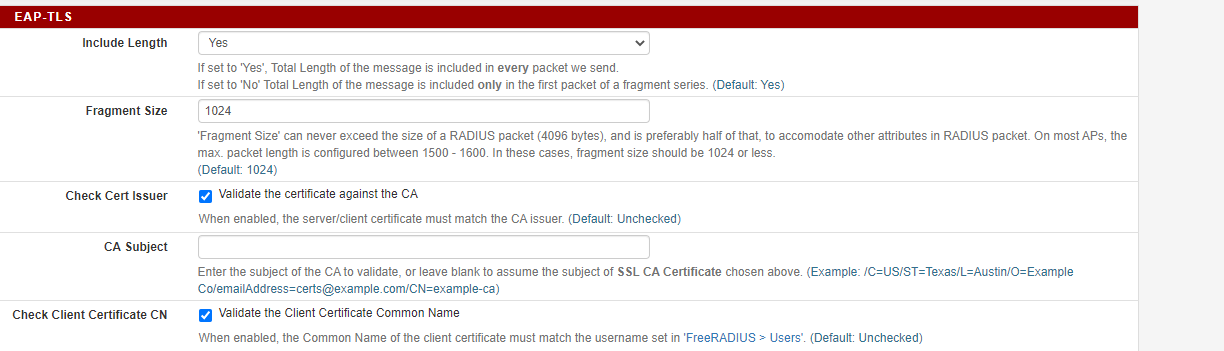
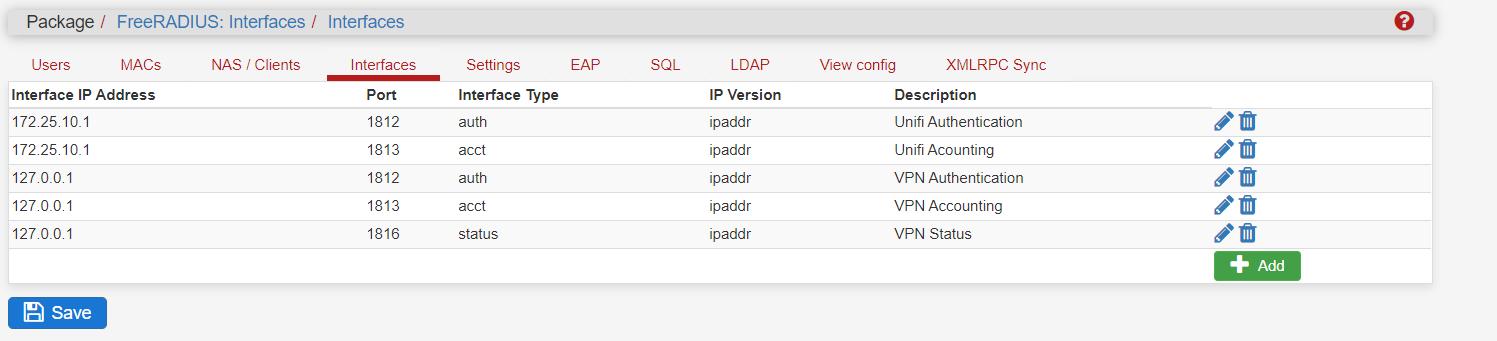
This are the settings:
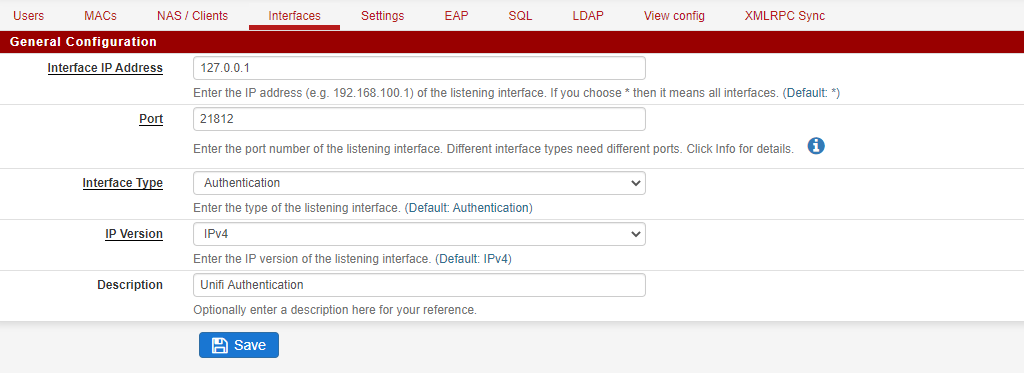
Interfaces:
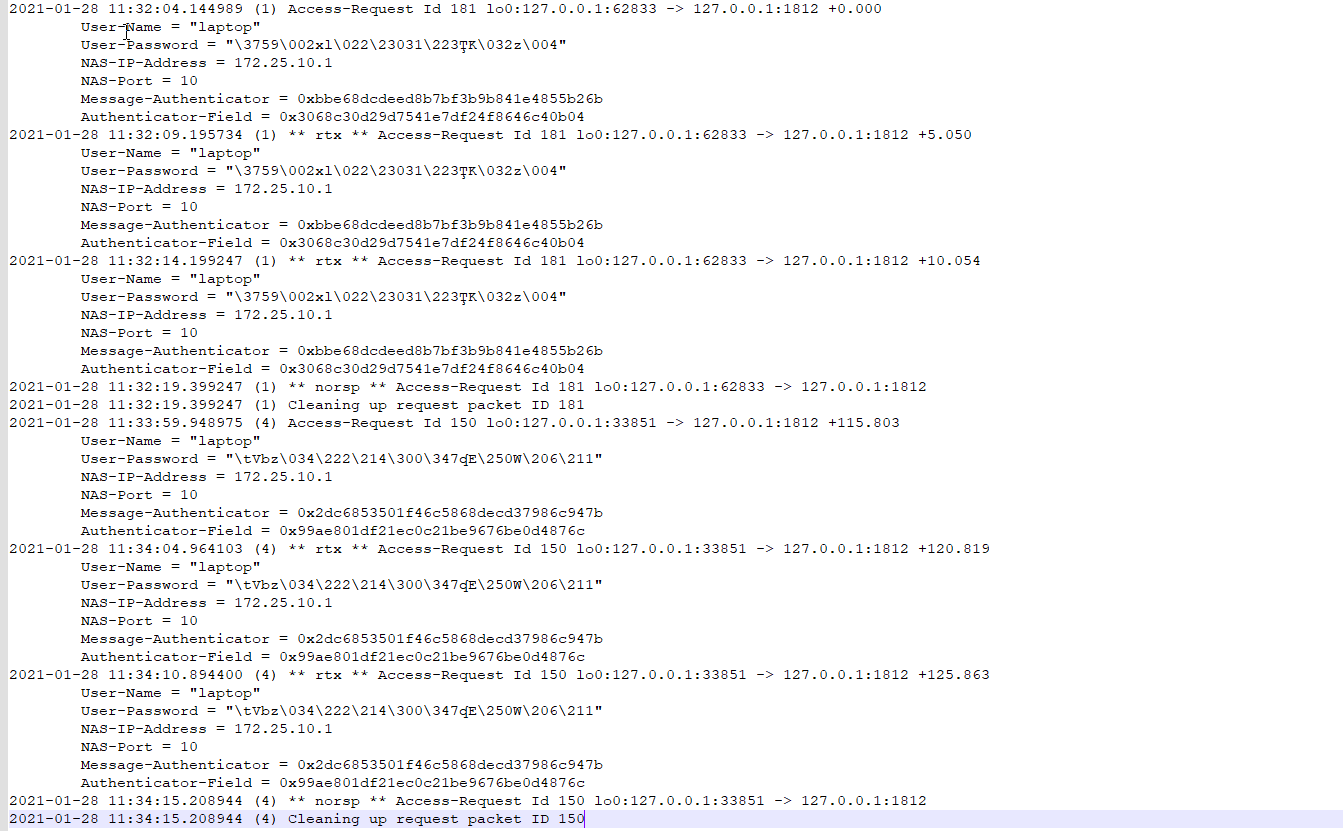
I've created an account 'laptop' with password 'abcd1234' (for testing) and these are the results from inside the SG3100:
[2.4.5-RELEASE][admin@pfsense.home]/root: radtest laptop abcd1234 127.0.0.1 10 abcd1234 Sent Access-Request Id 150 from 0.0.0.0:33851 to 127.0.0.1:1812 length 76 User-Name = "laptop" User-Password = "abcd1234" NAS-IP-Address = 172.25.10.1 NAS-Port = 10 Message-Authenticator = 0x00 Cleartext-Password = "abcd1234" Sent Access-Request Id 150 from 0.0.0.0:33851 to 127.0.0.1:1812 length 76 User-Name = "laptop" User-Password = "abcd1234" NAS-IP-Address = 172.25.10.1 NAS-Port = 10 Message-Authenticator = 0x00 Cleartext-Password = "abcd1234" Sent Access-Request Id 150 from 0.0.0.0:33851 to 127.0.0.1:1812 length 76 User-Name = "laptop" User-Password = "abcd1234" NAS-IP-Address = 172.25.10.1 NAS-Port = 10 Message-Authenticator = 0x00 Cleartext-Password = "abcd1234" (0) No reply from server for ID 150 socket 3 [2.4.5-RELEASE][admin@pfsense.home]/root:This is what shows up on Radsniff on another putty session:
These are the firewall rules on the LAN side:
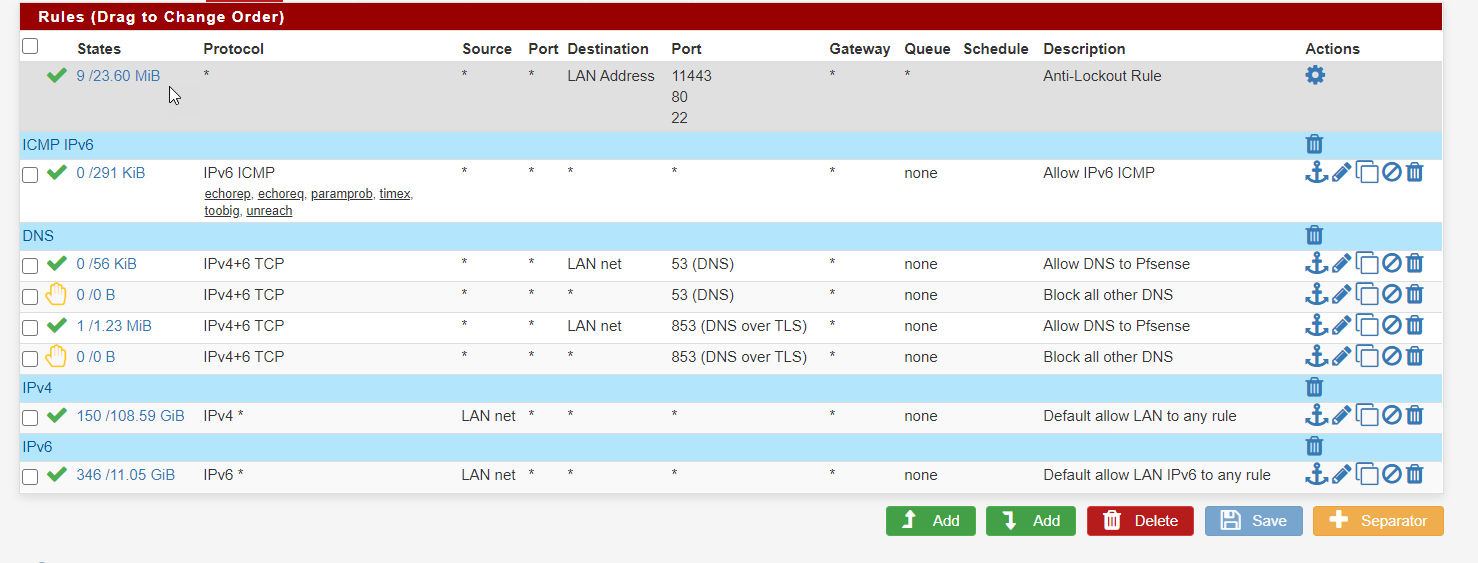
Still no luck "(0) No reply from server for ID 150 socket 3" seems to be the key.
-
Did you follow the instructions given here for testing.
https://pfsense-docs.readthedocs.io/en/latest/usermanager/testing-freeradius.html
I just did and boom - works
[2.4.5-RELEASE][admin@sg4860.local.lan]/root: radtest testuser testpassword 127.0.0.1:1812 0 testing123 Sent Access-Request Id 98 from 0.0.0.0:61162 to 127.0.0.1:1812 length 78 User-Name = "testuser" User-Password = "testpassword" NAS-IP-Address = 192.168.9.253 NAS-Port = 0 Message-Authenticator = 0x00 Cleartext-Password = "testpassword" Received Access-Accept Id 98 from 127.0.0.1:1812 to 127.0.0.1:61162 length 20 [2.4.5-RELEASE][admin@sg4860.local.lan]/root:Make sure you turn on logging in freerad, and if you do something wrong you get a log entry with some clue to why..
Here I changed the secret and it fails
[2.4.5-RELEASE][admin@sg4860.local.lan]/root: radtest testuser testpassword 127.0.0.1:1812 0 badpass Sent Access-Request Id 16 from 0.0.0.0:17422 to 127.0.0.1:1812 length 78 User-Name = "testuser" User-Password = "testpassword" NAS-IP-Address = 192.168.9.253 NAS-Port = 0 Message-Authenticator = 0x00 Cleartext-Password = "testpassword" Sent Access-Request Id 16 from 0.0.0.0:17422 to 127.0.0.1:1812 length 78 User-Name = "testuser" User-Password = "testpassword" NAS-IP-Address = 192.168.9.253 NAS-Port = 0 Message-Authenticator = 0x00 Cleartext-Password = "testpassword" Sent Access-Request Id 16 from 0.0.0.0:17422 to 127.0.0.1:1812 length 78 User-Name = "testuser" User-Password = "testpassword" NAS-IP-Address = 192.168.9.253 NAS-Port = 0 Message-Authenticator = 0x00 Cleartext-Password = "testpassword" (0) No reply from server for ID 16 socket 3 [2.4.5-RELEASE][admin@sg4860.local.lan]/root: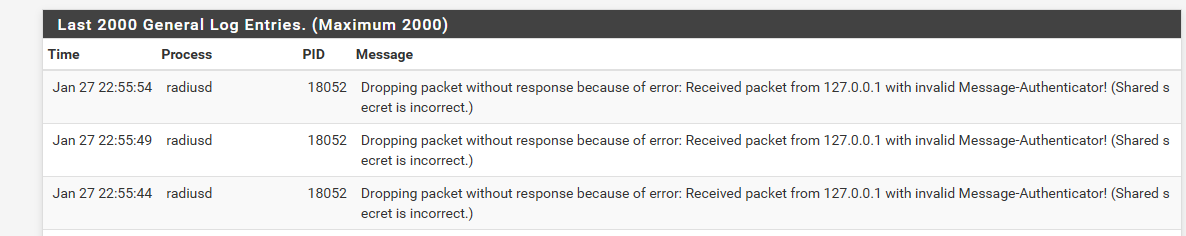
-
The radius requests come from the AP not the Unifi controller, is 172.25.10.1 your ap ?
If it isn’t you need to add the ap.
-
he needs to get the simple local test working first ;)
-
- My pfsense router (SG-3100) IP is 172.25.10.1.
- Unifi AP ip is 172.25.10.2
- Controller version upgraded to 6.0.45
- Radius package version is 0.15.7_21
- Radius logging destination is set to System Logs
I blew away all the prior configs (interface and NAS), rebooted the router, and managed to get an output from inside pfsense using the test case. Output below:
[2.4.5-RELEASE][admin@pfsense.home]/root: radtest testuser testpassword 127.0.0.1:1812 0 testing123 Sent Access-Request Id 195 from 0.0.0.0:57096 to 127.0.0.1:1812 length 78 User-Name = "testuser" User-Password = "testpassword" NAS-IP-Address = 172.25.10.1 NAS-Port = 0 Message-Authenticator = 0x00 Cleartext-Password = "testpassword" Received Access-Accept Id 195 from 127.0.0.1:1812 to 127.0.0.1:57096 length 20I now recreated a new NAS/Client and Interface and changed the Secret in the unifi controller to "testing123". This is what it looks like now:
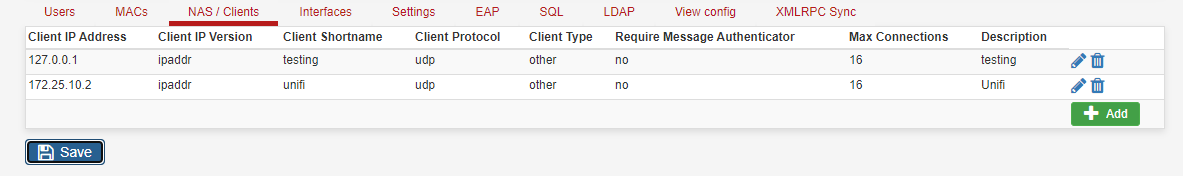
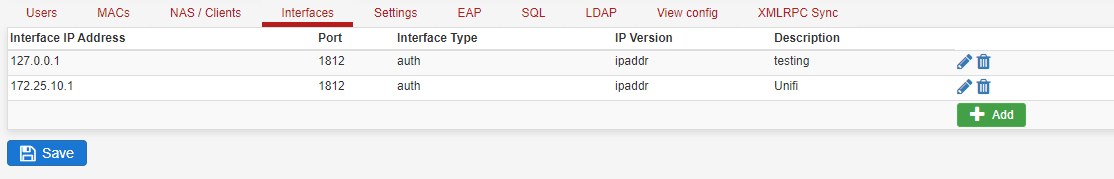
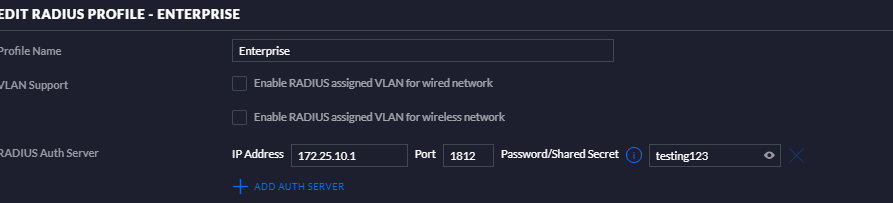
I guess so far so good? Logically the next step is to test Unifi talking to pfsense I suppose - I can SSH into the unifi AP but can't seem to find a command such as Radtest that I can use. Does anyone have the EAP settings in FreeRadius and Unifi that they can share?
If I ever get this to work - I will write a user guide to configure Unifi with Pfsense :)
-
@alnico said in Help trying to get EAP-TLS working (Pfsense / Unifi):
I guess so far so good? Logically the next step is to test Unifi talking to pfsense I suppose - I can SSH into the unifi AP but can't seem to find a command such as Radtest that I can use. Does anyone have the EAP settings in FreeRadius and Unifi that they can share?
If I ever get this to work - I will write a user guide to configure Unifi with Pfsense :)
radtest isn't available on the ap, I just checked.
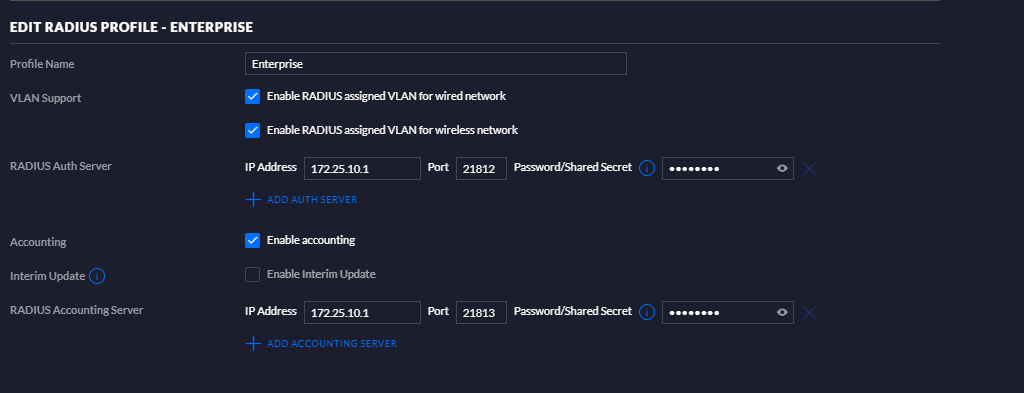
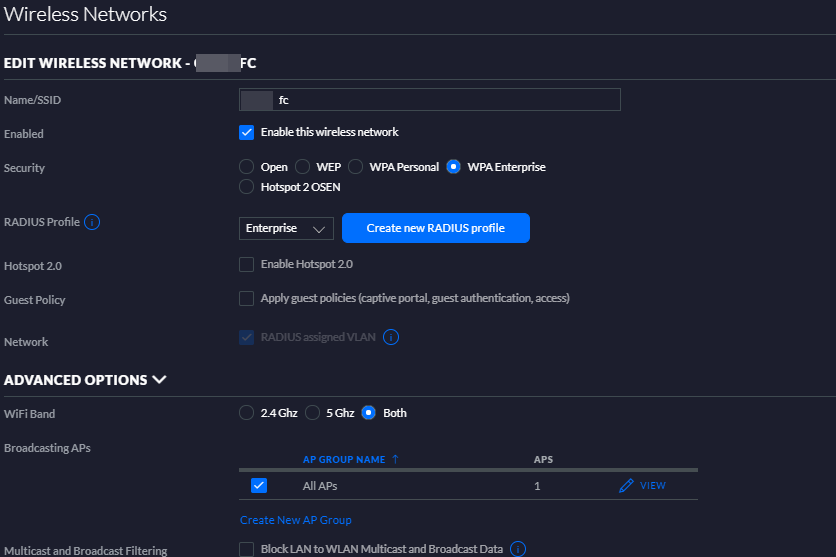
Here's what I have set:-
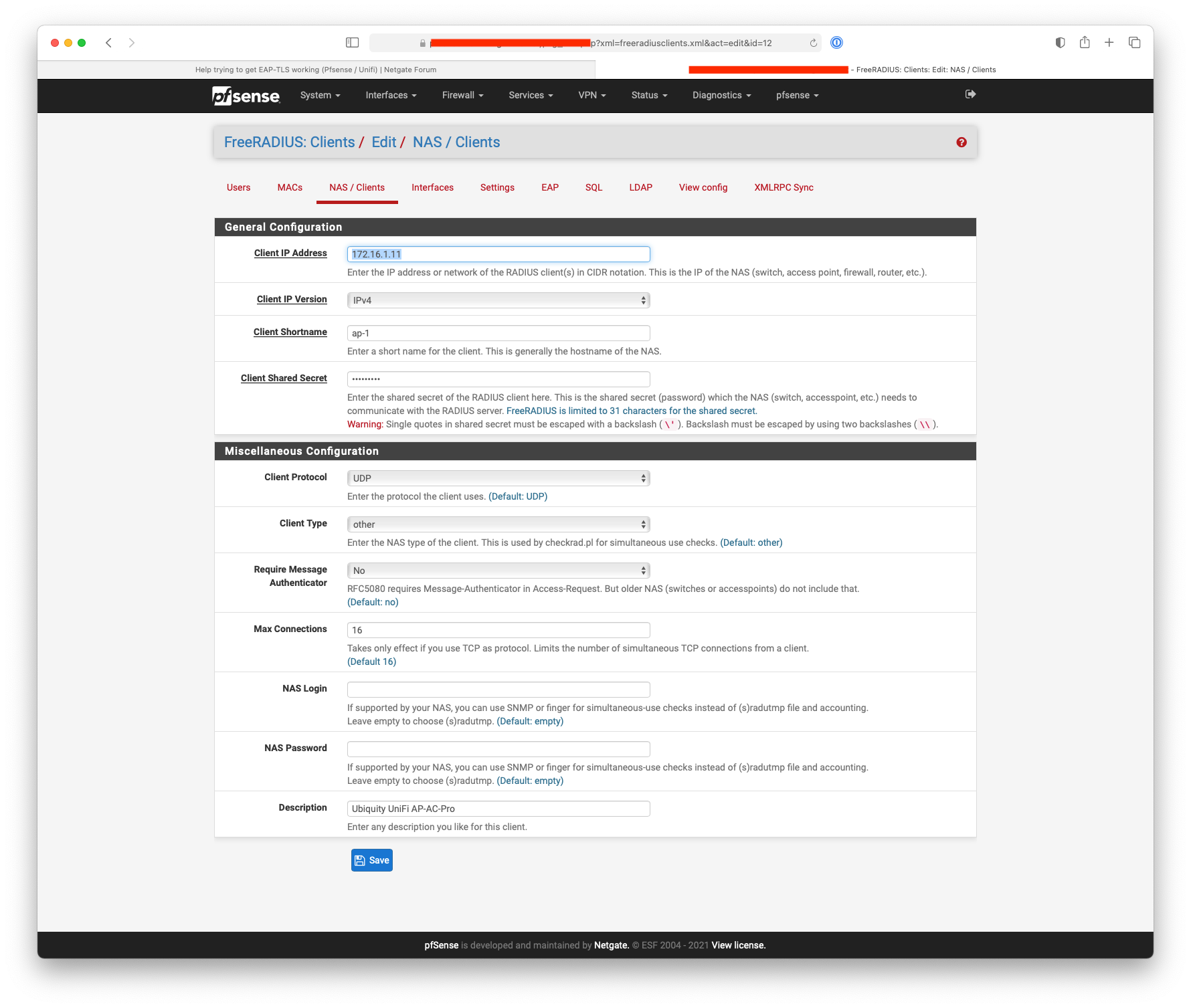
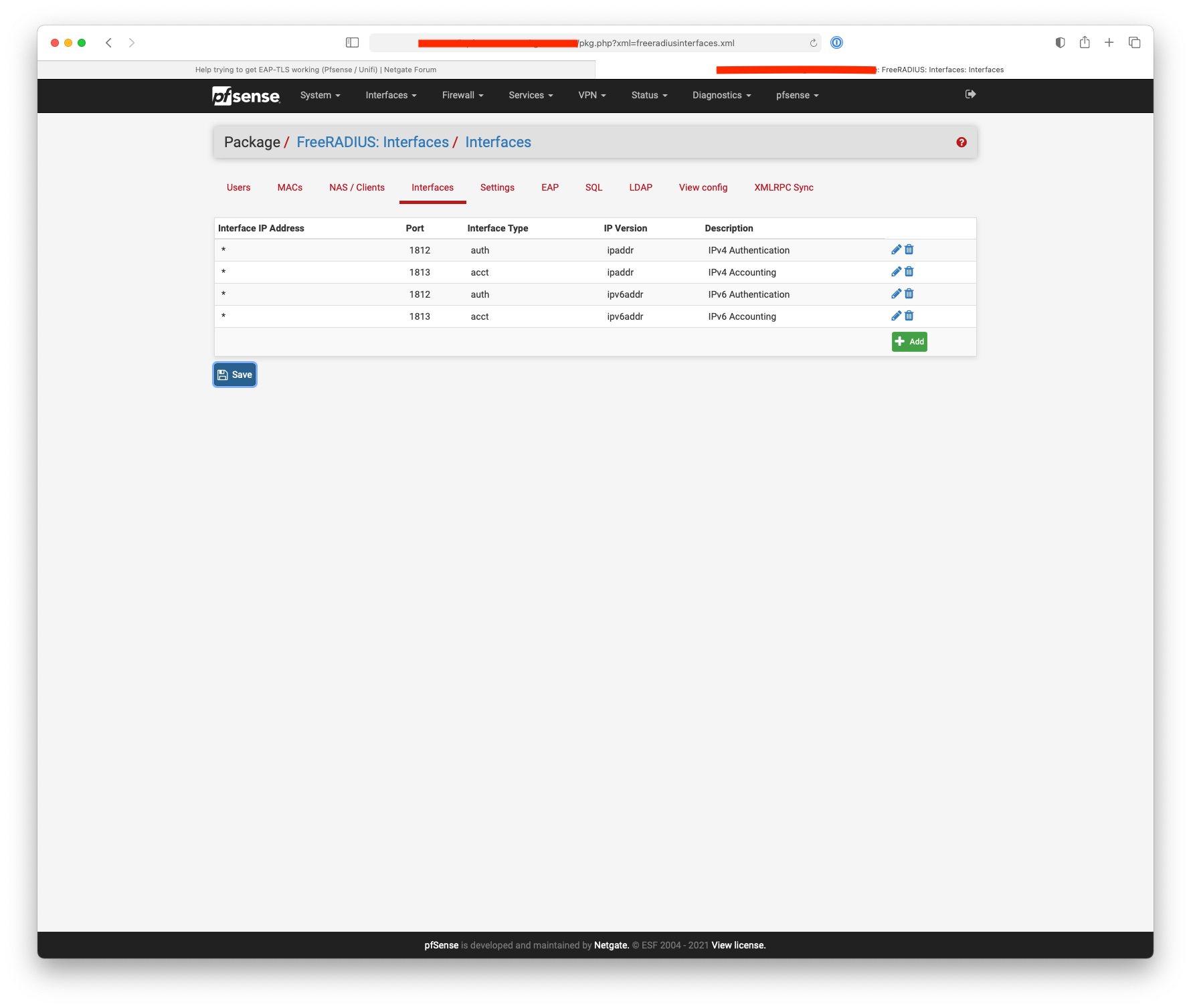
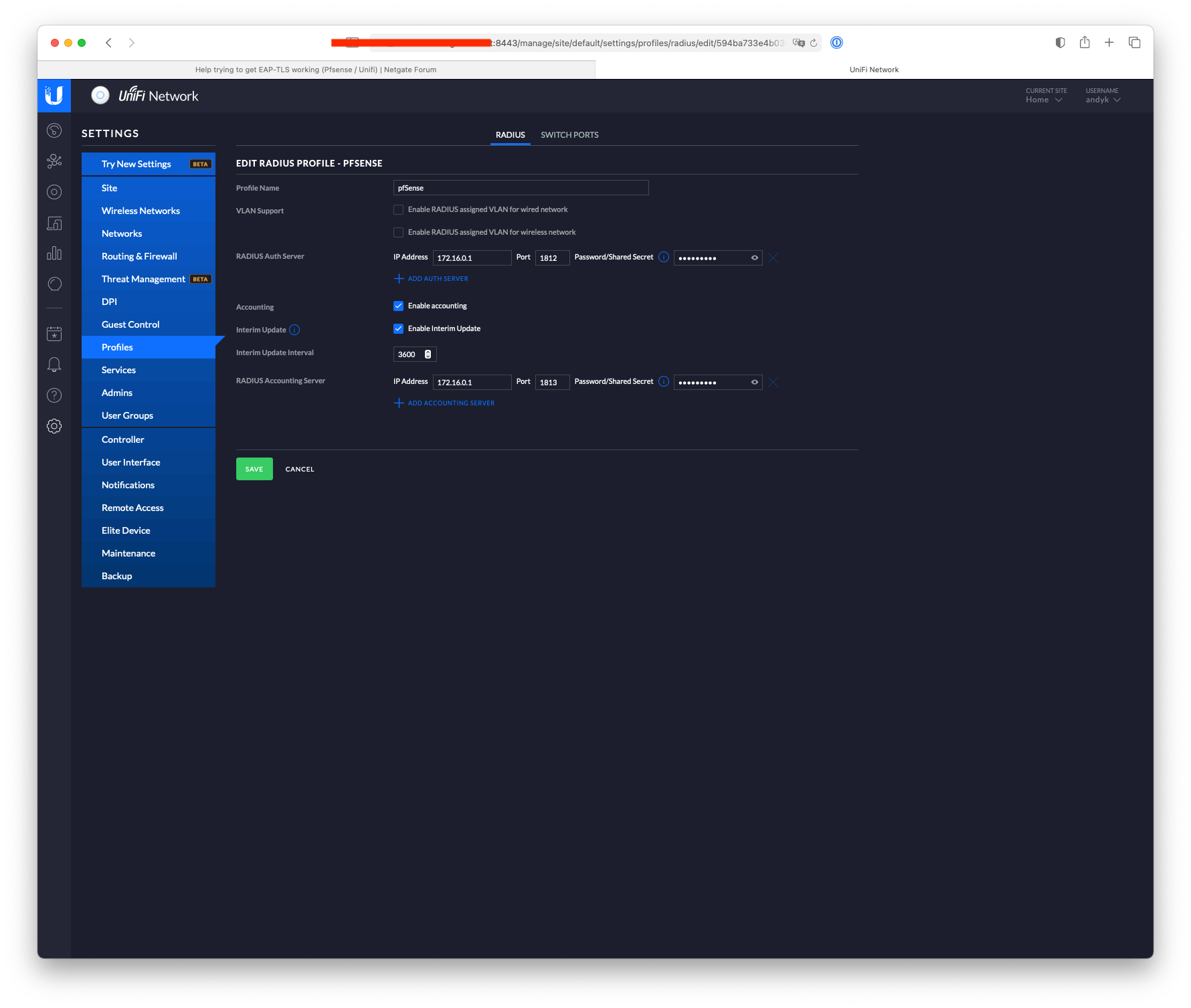
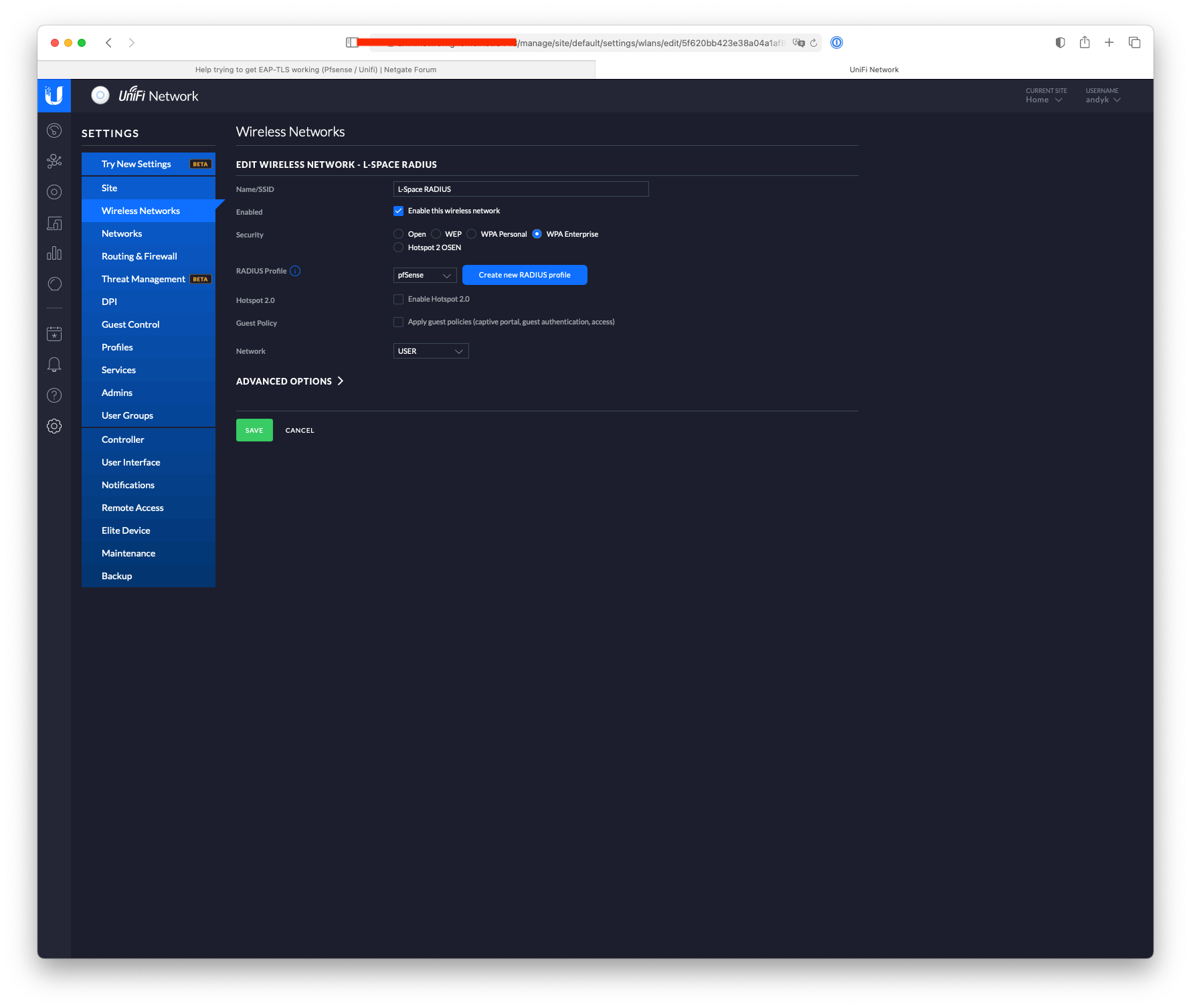
-
@nogbadthebad no still no good. Apologies for the delay in getting back, I had some pressing things I needed to attend to.
I will wait for the new pfsense update (since its due this month) and then see how I go.
-
Not sure what you believe is going to change with how freerad works with 2.5?
Simple way to validate - is look at your log, and just sniff. Do you see traffic hitting pfsense from your AP?