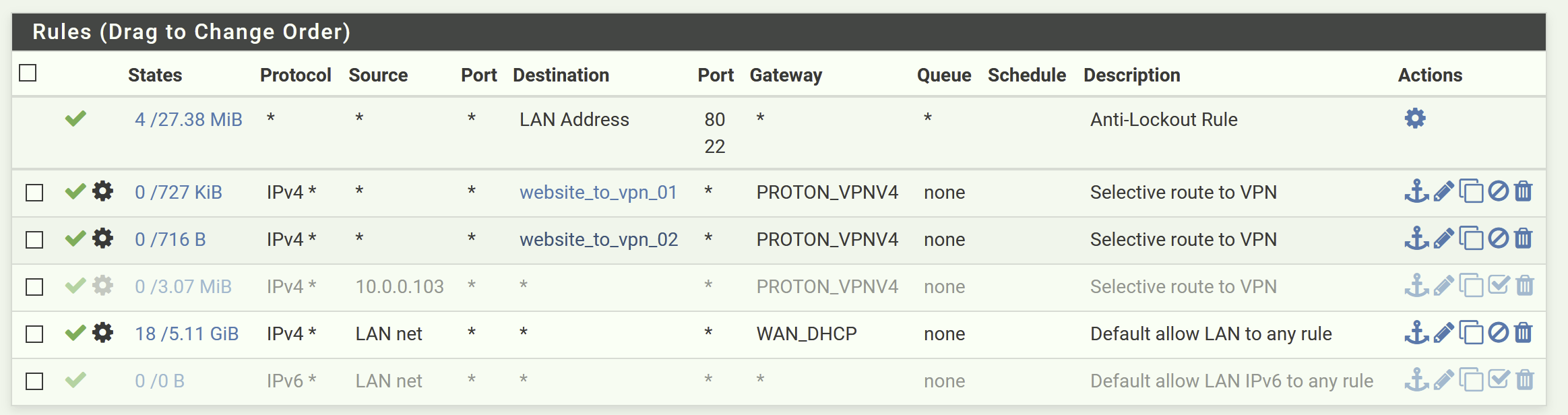
vpn selective routing - tracetcp shows only one hop
-
hello to all
im new to the pfsense system. i have it running with a basic configuration. i have no shaping enable yet.
i have a vpn client running with some selective routing so specific websites go through the vpn and not my isp.
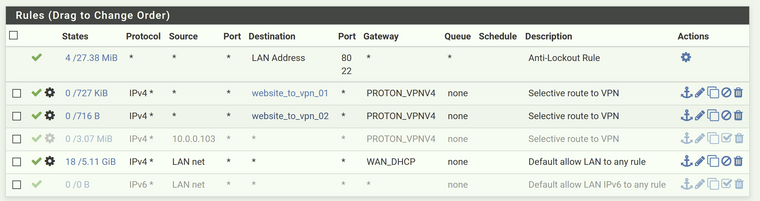
im currently using some aliases for the selective routing so i route specific ip's via the vpn.
my question is related when i perform a tcp traceroute from my windows pc connected to the lan. even though the selective routing works as i get the vpn ip address when i access, a vpn-routed website like ifconfig.io, performing a tcp traceroute will only show one hop. why could that happen?
this also happens when routing all traffic from one specific LAN client via the VPN. the tcp trace will only show one hop.
doing a regular icmp trace will show all hops.tracetcp ifconfig.io -t 200 -n Tracing route to 104.21.65.79 on port 80 Over a maximum of 30 hops. 1 Destination Reached in 65 ms. Connection established to 104.21.65.79 Trace Complete.regular icmp traceroute does show all the hops
tracert -w 200 -d ifconfig.io Tracing route to ifconfig.io [104.21.65.79] over a maximum of 30 hops: 1 121 ms 120 ms 120 ms 10.17.0.1 2 * * * Request timed out. 3 84 ms 103 ms 150 ms 37.120.215.241 4 130 ms * 80 ms 217.138.223.160 5 71 ms 93 ms 94 ms 217.138.223.210 6 * * * Request timed out. 7 64 ms 56 ms 62 ms 104.21.65.79 Trace complete.thanks
-
If you are passing through a VPN, that always counts as only one hop, no matter how many actual hops there are. On the other hand, the packets that carry the VPN will reflect the appropriate hop count. The reason for this is traffic within the VPN can't see the routers along the way, but the transport packets can.
-
@jknott said in vpn selective routing - tracetcp shows only one hop:
on for this is traffic within
thanks. so no matter what, i will always see a single hop on my tcp traces from a pc lan client connected to the pfsense server?
just as a side experiment, if i connect directly to the vpn from my computer, tcp traces will show all the hops and not just one.
-
No matter how you connect, the transport packets, that is UDP port 1194, will see the hops. Anything carried within the VPN will not. Think of mailing an envelope. The envelope may have multiple post marks, as it makes it's trip. An envelope within it will only have a post mark from the point where it was put into the outer envelope.
-
I would still expect to see hops between the VPN provider and the target host though.
The only way I could imagine 1 hop there is some TTL shenanigans going on.
I will also note that the policy routing for imgur is unlikely to work well as those fqdns are almost certainly resolvable to numerous IPs but the alias will only resolve them once when the ruleset is updated. Same as this:
https://docs.netgate.com/pfsense/en/latest/recipes/block-websites.html#using-firewall-rulesSteve
-
@stephenw10
thanksim using specific imgur servers as example and they do look so far. traffic goes through the vpn, but the annoying 1 hop still shows
some examples with selective traffic routed
tracetcp i.imgur.com -t 200 -n Tracing route to 151.101.4.193 on port 80 Over a maximum of 30 hops. 1 Destination Reached in 80 ms. Connection established to 151.101.4.193 Trace Complete.tracetcp www.imgur.com -t 200 -n Tracing route to 151.101.4.193 on port 80 Over a maximum of 30 hops. 1 Destination Reached in 77 ms. Connection established to 151.101.4.193 Trace Complete.tracetcp s.imgur.com -t 200 -n Tracing route to 151.101.4.193 on port 80 Over a maximum of 30 hops. 1 Destination Reached in 92 ms. Connection established to 151.101.4.193 Trace Complete.regular traffic going through ISP. hop #1 is my pfsense firewall
tracetcp google.com -t 200 -n Tracing route to 142.250.64.206 on port 80 Over a maximum of 30 hops. 1 * * * Request timed out. 2 14 ms 14 ms 8 ms 172.21.111.2 3 16 ms 22 ms * 72.14.218.195 4 51 ms 65 ms 25 ms 72.14.218.194 5 34 ms 45 ms 28 ms 108.170.253.198 6 82 ms 50 ms 54 ms 209.85.241.109 7 61 ms 81 ms 68 ms 72.14.233.103 8 71 ms 67 ms 63 ms 142.250.212.251 9 68 ms 72 ms 76 ms 216.239.62.1 10 62 ms 65 ms 64 ms 108.170.249.1 11 Destination Reached in 77 ms. Connection established to 142.250.64.206 Trace Complete. -
They must be doing something with the TTL to make it look like one hop.
Probably something to prevent VPN detection. Guessing though.
I don't see that here using the ProtonVPN free tier and the address dircetly.
Steve
-
thats weird indeed. connecting to the same proton free server straight from my computer will show all hops.
i guess theres not much i can do
thanks!