files.pfsense.org : Lets Encrypt certificate has expired
-
Good Morning,
This morning our Snort Open AppId rules update failed getting updates from
https://files.pfsense.org/openappid/.Snort AppID Open Text Rules md5 download failed. Server returned error code 0. Server error message was: SSL certificate problem: certificate has expired Snort AppID Open Text Rules will not be updatedThis is the current certificate served by
files.pfsense.org. I note that it SANed forpfsense.orgwhich is serving up a non-expired certificate, albeit with differrent public key.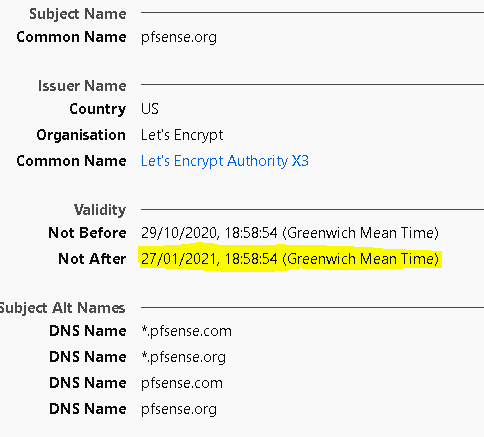
I believe we have had this problem before; Is there any monitoring on certificate validity for
files.pfsense.org?Thank you.
-
edit : Oops.
Re read the question - and found out I was reading something else.
I pulled the same cert :
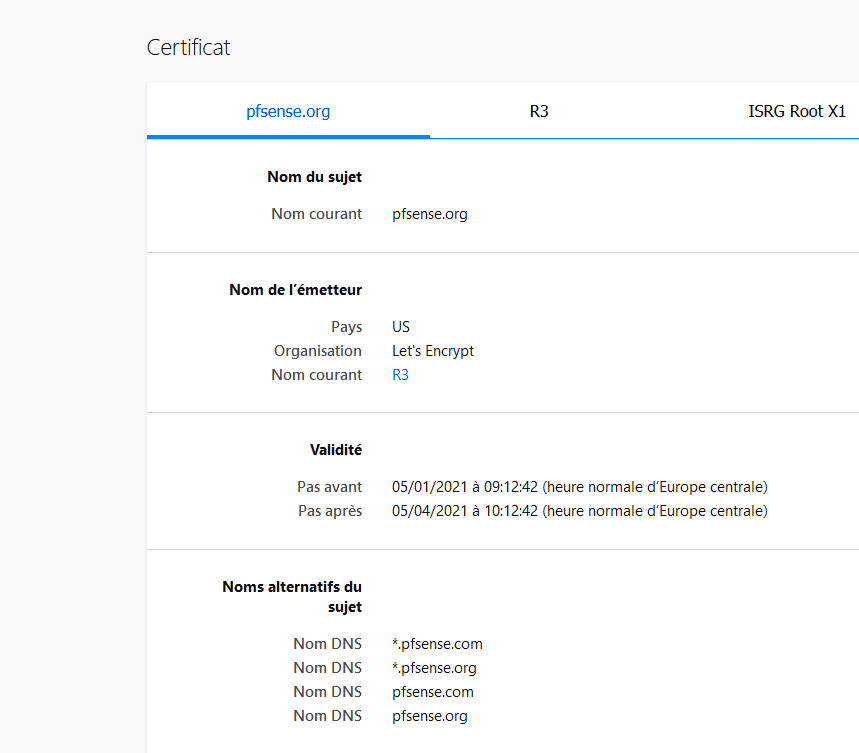
are we not looking at the same site, for example : https://www.pfsense.org ?
-
@gertjan said in files.pfsense.org : Lets Encrypt certificate has expired:
are we not looking at the same site, for example : https://www.pfsense.org ?
Check site https://files.pfsense.org/
-
Is also *.pfsense.org is ok for me.
-
I don't know the details of how they have this setup.. But I would guess some servers got the new cert on on 1/5 and others have not.. Which is why only specific urls showing the old cert.
I sent a PM to Steve - sure they will get it fixed up soon enough..
One of the flaws in having to update every 90 days, and automation - sometimes it doesn't always work as planned/desgined.
-
@johnpoz said in files.pfsense.org : Lets Encrypt certificate has expired:
flawed ..... update every 90 days automation
90 ....
More often will create the same problems .... more often ;)
Less often and people forget how to debug, draw conclusions and repair fast. Also : Letsenscypt also has to deal with the ones that want to 'burn' (revocate) their certs ... at least now they can keep a 90 days max list instead of a classic two years list, reducing browser cert validity checking. Knowing how many certs they have outstanding these days and you'll get the picture.
And "automation " shouldn't be related to "forgetting about it".I've got several 'original' acme script running (several devices) , and two with pfSense using the pfSense package.
And the unbeatable combination : no DNS registrar on the other side that changes the 'something' some times. The DNS name server of my domains is me using RFC2136.
It's rock solid. I don't make calendar entries any more (on phone) to check things every 60 days. I just get a mail with "acme => done = > my domain". -
@gertjan said in files.pfsense.org : Lets Encrypt certificate has expired:
I just get a mail with "acme => done = > my domain".
Well clearly they do not have that setup, or they are not looking at the error emails :)
This has happened before - same sort of issue..
-
Looks good now. Anyone still seeing this?
-
Looks good here.
-
It didn't get better for me (was already good).
@johnpoz said in files.pfsense.org : Lets Encrypt certificate has expired:
do not have that setup
The pfSense acme package has the "action" list, where you can set up .... actions.
Like send a mail when it's done. But, it strikes me now, it does so when thing went well.
I should have something to show up start to go wrong.
( some one behinds me propose me : "use two tv sets and dial into CNN and Fox news", this is french humor as best as it gets).
I should be cooking a script that runs one a week that 'reads' a cert, extracts its end date/time, minus the actual date/time and if less then 2 weeks or so : sends a mail./root: openssl x509 -enddate -noout -in /tmp/acme/my-domain/my-domain/my-domain.cer notAfter=Apr 13 21:55:05 2021 GMTplus some other shell whatever script and done.
Anyway, @stephenw10 , @ monotypeTattoo I'll drop a copy here when I get it done.
-
Keep in mind that cert might of updated just fine, but the service using the cert maybe just didn't update.. Your using some httpd to serve up file, even if you update the cert on the machine - you have prob have to tell whatever httpd your using to reload the new cert..
-
echo | openssl s_client -servername domain.tld -connect domain.tld:443 | openssl x509 -noout -enddate | grep 'notAfter' > date.txtThe file date.txt should contain a date and time in the future :
notAfter=Apr 3 01:17:16 2021 GMT