routed IPSEC (vti) tunnel established but no communication after a time
-
Hi guys,
I'm trying the new VTI routed IPSec.
I've two PFSense's in two different locations. Previously connected via traditional IPSec phase1/phase2 without problems. Now I've configured routed IPSec, and when configured it works!
(I've followed this documentation: https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/routed-vti.html)
The issue appears several minutes after testing, when no traffic is generated. Then I have apparently tunnel UP, but not working.
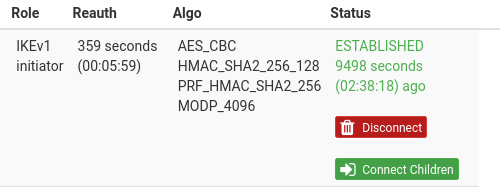
Showing in "Status > IPSec" tunnel is ESTABLISHED, but it appears a green button indicating "connect children". After pushing this button, communication starts working again.
What can I do to automatically have my routed IPSec (vti) allways up and running without any manual action?
Thanks and regards!
-
@pfsensista
screenshot of "connect children" button that should be clicked in order to bring back communications:
-
The VTI config is quite fragile. I saw the same recently and spent much tinkering on what I think is a working combination of settings now. The problems alternated between this and the known issue of phase 2 entries piling up.
These settings have been stable for a week now, with simultaneous ISP disconnects every 24 hours on both ends:
Phase 1:- Key timings are the same on both end, in case you read the discussions about the perceived advantage of asymmetric configurations
- Also, no responder-only setting is used
- NAT Traversal is forced on the side where it is required
- Child SA Close Action: Close & Reconnect
- DPD is enabled
IPsec advanced:
- Make-before-break enabled
Routing/Gateway:
- Gateway monitoring disabled
- Gateway monitoring action disabled
-
Hi @morlock , many many thanks for your answer.
I already had configured your Phase1 parameters, but I've tried IPSec advanced and gateway ones and It works properly!
I've tested different lifetime values, 1hour, 8hours, 24hours... and it seems it works fine!
Now I'm going to test if it only depends on IPSec advanced "make-before-break" parameter, just to understand what was going on.
I'll provide feedback again.
Many thanks mate!