More details than bandwidthd?
-
I'm using bandwidthd to get some idea of what is using in terms of data on the network but bandwidthd is pretty simplistic. I use vnstat on servers to know what each is doing but is there something for pfsense that can give me a much more details account of resource usage.
I'd like to know how much bandwidth, data, per date ranges servers are using. This is important in terms of knowing when to add more bandwidth or servers etc.
Does anyone know what might be available for pfsense that could give me such details?
-
https://docs.netgate.com/pfsense/en/latest/monitoring/graphs/bandwidth-usage.html
-
Those appear to be command line tools which we use all the time. I'm asking for something built into pfsense that will gather this information similarly to what bandwithd does but more detailed
breakdowns.I'll take a look in case I didn't notice something. Thank you.
-
You tried ntop-ng?
https://docs.netgate.com/pfsense/en/latest/monitoring/graphs/bandwidth-usage.html#ntopngSteve
-
I'll take a look thanks.
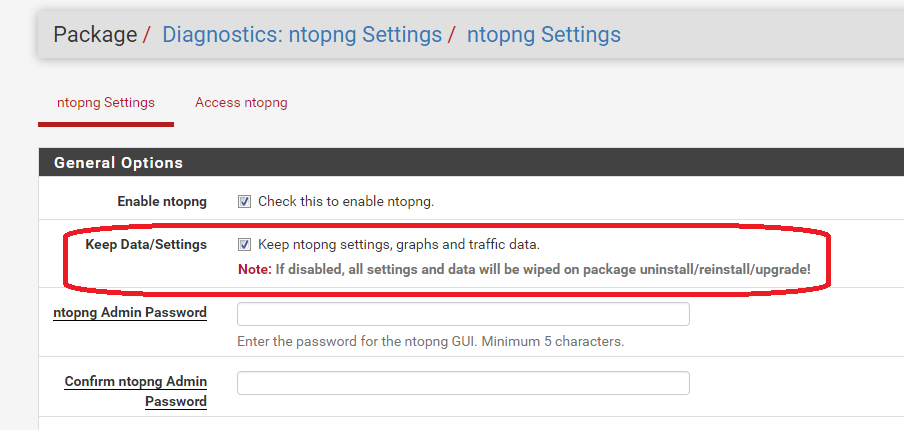
Do you know if adding/removing packages to try out leaves all kinds of mess behind or not a big issue?
-
It shouldn't....
-
This post is deleted! -
Thanks, I'm checking out ntopng.
The only odd thing is that the package installer installed a certain version but the ntop page keeps telling me there is an update but I don't see any way to update. -
@lewis I am now reading that ntpng has serious security issues? Is this true and if so, why is it available as a package on pfsense without such a warning?
- net-analyzer/ntopng-4.0::gentoo (masked by: package.mask, ~amd64 keyword) /usr/portage/profiles/package.mask: # Sam James <sam@gentoo.org> (2020-07-20) # Serious security vulnerabilities, including # remote code execution. Upstream have not yet # made a stable release in response to numerous # CVEs. Applying patches is not a workable # solution for now because of the fragility # of reverse dependencies. # Indefinitely masking until we have a solution # for this. # bug #719084 # Furthermore, ntopng ebuilds depending directly on dev-lang/lua{,jit} # must be migrated to lua eclasses before unmasking (bug #752777). -
@lewis pfSense isn't even using ntopng4.0, its 3.8.
-
Not to make light of issues, especially remote code execution.. but If running this correctly on your network.
How would anyone other than admin, your management vlan have any possible way to talk to the service to do a remote code anything.
Now if your saying someone on a network that is being monitored.. Could send some traffic that would exploit ntop in such a way to do something.. Then yeah that would be a serious concern.
But sometimes you need to look into how such issues can actually be exploited.. If you have to have admin rights already, or be on the management vlan to exploit it.. While sure they need to be taken into account, and should be fixed. On a properly ran network, they should not be of such a concern that you don't run the application - when it provides you something you want/need to be able to do.
-
@nogbadthebad said in More details than bandwidthd?:
@lewis pfSense isn't even using ntopng4.0, its 3.8.
Yes, I do see an update in the packages installed now. I've used that but it is still showing 3.8 in the dashboard of ntopng.
Is the new version more secure based on what I posted?
In terms of access, I have to remotely access the firewall so using it is not from the LAN side.
-
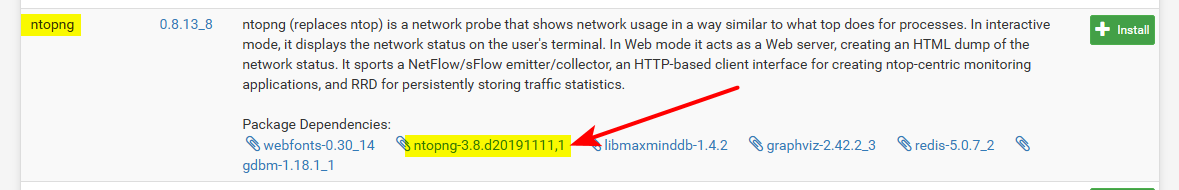
After the update, the package manager now shows 0.8.13_8. Totally confused.
-
Those are the version numbers of the "packages" for pfsense - not the version of the software being used in the package.
-
@johnpoz
Yes, I noticed that after I posted. It seems there is no way to get to 4.x so the question is, based on what I posted, is this package safe? -
That call is yours.. There are thousands of thousands of install running it of that I am sure..
If it was of serious concern, I would assume it would be patched, or pulled or atleast a serious warning, etc.
Again see my above posts about who can access what when it comes to exploitable things.. Are you worried about some issue with exploit if the person has to be at the console logged in as root to exploit it ;)
Same goes with any other exploitable issue - what is the complexity of actually pulling off the exploit.. Example - lets say that there is some serious exploit to ssh.. And anyone that can ssh to X, can get root access.. While this is a concern sure if you have ssh open to the internet. Is it a concern if the only one that can talk to ssh is IP abc, who is the root admin of the box in the first place.. And that IP is local, and the PC is in a locked room ;)
-
I have no lack of understanding what the issues could be but that wasn't the question :). Either way, I appreciate all that input and I'm sure it will help the next person that finds this.
In the meantime, I'm going to use it.
Thanks.