Port Forward SSH from private IP to VM host
-
Hi Everyone.
I have a DELL R710 with Proxmox installed as the bare metal hypervisor, I have pfSense as a VM in between my Domain lab environment and my home LAN.
I have recently installed a RHEL 8 VM without the GUI and I'm trying to SSH into it from my desktop that sits on the home LAN.
I have disabled the firewall rule that blocks private IP addresses inbound on the WAN port, I've configured a port forward rule and associated firewall rule as per the below pictures.
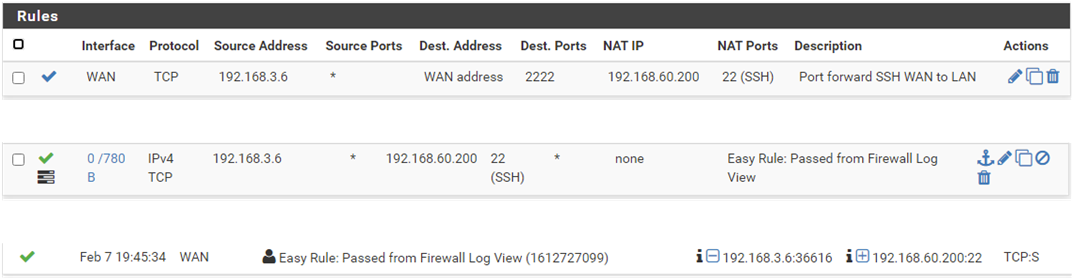
My desktop PC is 192.168.3.6 (VLAN3), pfSense WAN port is 192.168.6.2 (VLAN6), the RHEL8 server is 192.168.60.200. I'm initiating the SSH connection to 192.168.6.2 on port 2222 but the connection attempt times out.
I've checked the firewall logs and can see that the firewall rule is being triggered but no connection onward to 192.168.60.200.
I can SSH to 192.168.60.200 from another W10 VM on 192.168.60.2 so I know everything is set up fine on the RHEL8 server.
Can anyone give me any clues as to where I am going wrong please?
Network diagram as below.
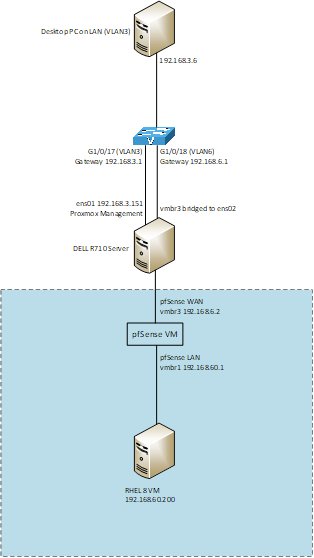
Thanks for any advise that can be offered.
Phill
-
@ta2oo said in Port Forward SSH from private IP to VM host:
I can SSH to 192.168.60.200 from another W10 VM on 192.168.60.2 so I know everything is set up fine on the RHEL8 server.
No, now you only know that the server accepts SSH connections from within its own subnet. Maybe it blocks the access if it comes from outside.
Do a packet capture on the LAN to see if the packets are passed.Another possible issue could be enabled hardware checksum offloading. Did you disable it?
-
@viragomann Thank you for replying.
I have actually loaded a new Ubuntu 20.04 VM as the RHEL trial license had expired, same IP address though.
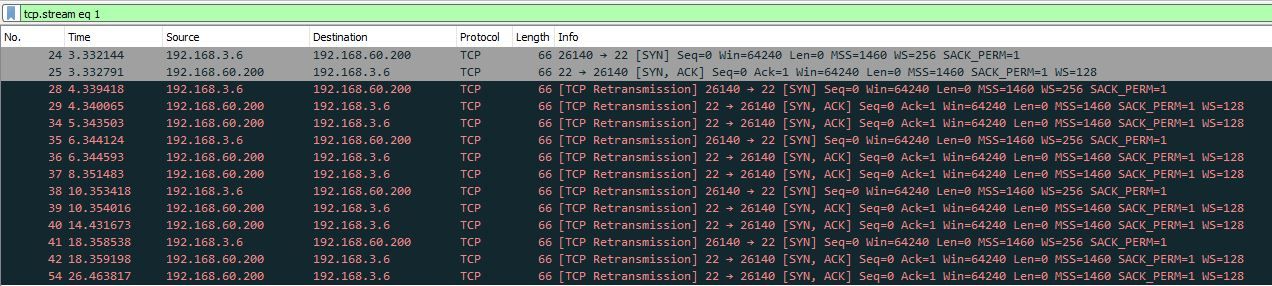
Yes, hardware checksum offloading is disabled on pfSense and for testing I disabled the Ubuntu firewall. I have attached the packet capture for the pfSense LAN port.
There is definitely communication with the server as I am seeing the initial SYN and SYN,ACK response from 192.168.60.200, but that is where it stops. it doesn't look like 192.168.3.6 is receiving the SYN, ACK response from 192.168.60.200, then it's just re transmissions of the same sequence.
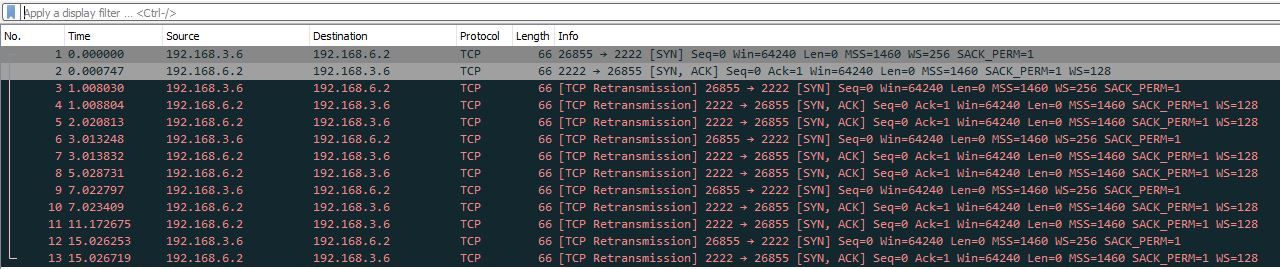
I am seeing the same pattern on the WAN port packet caputure, also attached.
Thanks
Phill -
@ta2oo
The packets shown in these captures are all marked as retransmissions. That is a typical indication for enabled checksum offloading on Proxmox / KVM. But maybe there is another basically wrong configuration network in your virtual network.
Are there also issues with other network protocols?