Site-to-site IPsec VPN with pfSense CE (floating IP, transfer network, app on firewall)?
-
Hi all,
we need to setup a VPN between an institution and our data center to receive messages with an application on a specific port. For most readers here this probably sounds easy, but I am a web developer with IT but little IP and VPN background. pfSense was recommended for it's ease of use, but I am still missing some pieces for the whole thing to work.
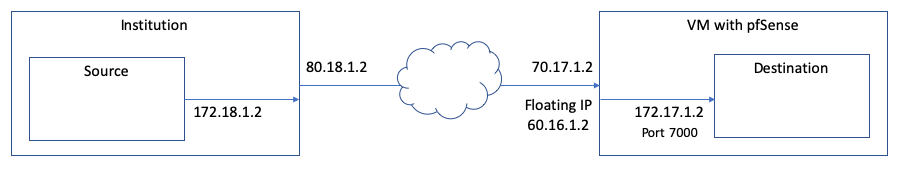
The source app within the institution (172.18.1.2) send messages through the VPN to our destination app (172.17.1.2, port 7000). The institution has an external VPN IP (80.18.1.2), we have an external VPN IP (70.17.1.2) and an external floating IP (60.16.1.2) which we would like to use for communication. The floating IP is for fail-over, it can be easily redirected to a different VM.The pfSense VM is up and running with pfSense CE 2.4.5, firewall rules are set to accept the incoming and outgoing traffic.
My 3 challenges:
-
The pfSense VM has an official external IP (as WAN via DHCP) and a floating IP (currently as virtual IP) for failover. The institution accepts the floating IP with their firewall. How do I setup pfSense so it uses the floating IP for outgoing messages? Just adding it as virtual IP seems not enough, I still see the WAN IP in the IPsec logs. Should it be the main WAN IP with a gateway? Do I need to configure a static route or something else?
-
With the internal IPs being on the same private network (by looking at the addresses), should I just set this up in IPsec Phase 2 as same local and remote network (172.16.0.0/12)? Do I need to do more than just enter this in Phase 2? Will pfSense automatically route packets?
(Does this make sense if I just want to receive messages with a single app on a single IP with a specific port within pfSense? Should I use "Local network: address" instead?) -
The destination is a small script on the pfSense VM that converts and forwards the messages. The internal destination IP is given by the institution, the app has a fixed port. How can I make the app accessible with this private IP within the VPN? Should I just add the destination IP in pfSense as virtual IP (which is then assigned to the host) and let the app just listen on that specific IP?
(Or should I rather do NAT? How would that be set up?)
Thanks a lot
bluepuma -
-
1. Floating IPSolution: add the floating IP as virtual IP and then it can be chosen in IPsec Phase 1 "Interface" dropdown.