Suricata Info
-
I would like to know how to whitelist some ip addresses.
I have inserted in pass list the aliases but it doesn't work very well -
Are the aliases for static IP addresses? The Pass List function in Suricata currently only works for static IP addresses. If the value in the alias is update after Suricata starts, the new IP value will not be seen by Suricata. It only reads a Pass List once, at startup, and stores the IP values in RAM. To reload the list, you need to stop and restart Suricata.
Also, a common mistake for new Suricata users is forgetting to assign a Pass List on the INTERFACE SETTINGS tab for the interface. Simply creating a list on the PASS LISTS tab is not all that is required. You then have to edit the Suricata interface and choose the name of the new Pass List in the Pass List drop-down, save that change, and restart Suricata on the interface.
-
@bmeeks yes, all only static aliases.
if my aliases it's a private ip, suricata permit all traffic from and to ip? -
@foolish86 said in Suricata Info:
@bmeeks yes, all only static aliases.
if my aliases it's a private ip, suricata permit all traffic from and to ip?Not sure I understand your question there. Might be a translation to English issue ??
A Pass List prevents an IP address from getting added to the snort2c blocking table maintained by the
pffirewall engine in pfSense. Suricata (and Snort) both do Legacy Mode Blocking by adding IP addresses from alerting packets to thatpftable. The contents of that table are displayed when you view the BLOCKS tab. You can also view its contents under DIAGNOSTICS > TABLES and choosing snort2c from the drop-down there.Suricata will not block an IP that is on a Pass List, BUT it still might be blocking the other IP in a conversation. How this works is determined by the Which IP to Block setting on the INTERFACE SETTINGS tab. For example, assume your Private IP is the source in a conversation that triggers an alert. Suricata will attempt to block either the source IP (SRC), destination IP (DST) or both IP addresses (BOTH) according to the Which IP to Block setting. However, if one of the IP addresses in the alert is in a Pass List, that particular IP won't be blocked. But any other IP address in the packet will get blocked depending on the setting. So if the setting is BOTH, then in my example your Private IP is the source, but it won't get blocked because it's on a Pass List. The destination IP is not covered by the Pass List, so it will get blocked. But if you had the setting on SRC, then nothing would get blocked in my example because your Private IP is the source but on the Pass List. Conversely, if the setting was DST, then the destination IP would get blocked because it is not on the Pass List.
-
@bmeeks suricata doesn't work correctly i have in pass list a ip, but suricata block
-
@bmeeks said in Suricata Info:
a estiver em uma Lista de passes, esse IP específico não será bloqueado. Mas qualquer outro endereço IP no pacote será bloqueado dependendo da configuração. Portanto, se a configuração for AMBOS, no meu exemplo seu IP privado é a fonte, mas não ser
I'm using SG-3100 in version 21.05 and snort doesn't start, I tried to apply the patches but it didn't work.
I migrated to SURICATA, but I don't find the PASS LIST in Suricata, I put the IP List in EXTERNAL NET, would that be the option? someone know how to inform me
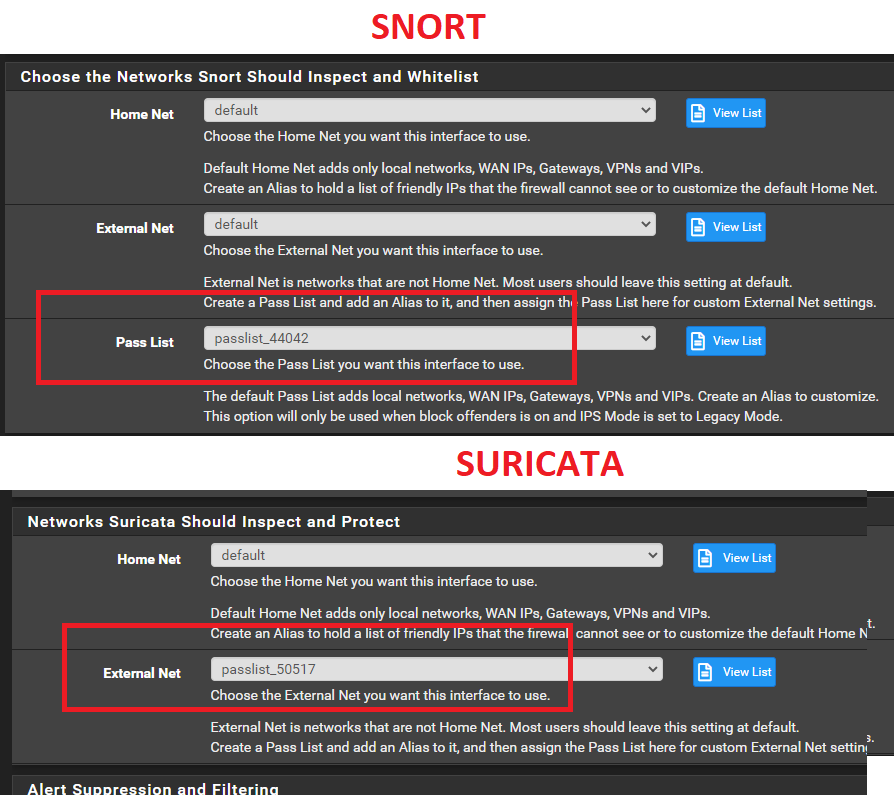
-
@luketa said in Suricata Info:
don't find the PASS LIST in Suricata
If you have Inline mode enabled then the pass list option is hidden. If you want a pass list use the default Legacy mode.
-
@luketa said in Suricata Info:
@bmeeks said in Suricata Info:
a estiver em uma Lista de passes, esse IP específico não será bloqueado. Mas qualquer outro endereço IP no pacote será bloqueado dependendo da configuração. Portanto, se a configuração for AMBOS, no meu exemplo seu IP privado é a fonte, mas não ser
I'm using SG-3100 in version 21.05 and snort doesn't start, I tried to apply the patches but it didn't work.
I migrated to SURICATA, but I don't find the PASS LIST in Suricata, I put the IP List in EXTERNAL NET, would that be the option? someone know how to inform me

Pass Lists are unnecessary when using Inline IPS Mode, because there are no permanent blocks of a host. Instead, individual packets are dropped on their way from the NIC to the kernel (or from the kernel to the NIC) as they traverse the netmap pipe. Pass Lists only exist, because in Legacy Mode, the IP address of a host is added to a firewall rule, and ALL traffic to/from that host is blocked. That is not the case with Inline IPS Mode. Because Pass Lists are not required, the option is hidden when using Inline IPS Mode.
If, for some reason, you want a given host to never have any packets dropped when using Inline IPS Mode, then create a custom PASS rule using the selection for Custom Rules on the RULES tab. PASS rules are evaluated first, and any traffic matching a PASS rule is immediately allowed and is not inspected by any other rules. So use PASS rules with care less you inadvertently completely neuter your IDS/IPS.
-