Root SSH login?
-
In the Linux world, root ssh login is generally not allowed and I believe the same is true with FreeBSD. Why is that allowed with pfsense? On Linux, I'd connect as a user and then use su to make myself root.
-
@jknott
perhaps otherwise you'd need to generate an additional user through console or gui before you could use ssh ?it doesn't matter much anyhow
-
I have created another user and was able to login. However, I'm unable to use su. Is that available in FreeBSD? The reason for this is additional security.
-
I have added myself to wheel group. Now, how do I make that menu I get with root login available when I connect as a mere mortal and then use su - to become root?
-
@jknott
seems like a pointless menu as a non-root user ... almost everything needs root in itedit /root/.profile
you'll notice the call to /etc/rc.initial <-- thats the menu afaik -
The point is you don't allow root login. You log in as user and then use su to become root. It makes it a bit more secure. Every *nix system has a root user, which makes it a target. Not so with ordinary users.
-
@jknott said in Root SSH login?:
In the Linux world, root ssh login is generally not allowed
and
@jknott said in Root SSH login?:
The point is you don't allow root login.
Several years ago, 'root' what the user the hosting company gave you, and a password.
We were advised to change that root password asap with the password command after a first login.
These days, a new 'Debain' system (that's the OS I know), you get an 'debian' user account, and a password.
'root' can't login over SSH by default. You have tosu -So far, all ok. Time learns us to do the same differently.
But there is an extra step that should be done and very few do it :
Shut down password logins altogether over SSH/SFTP.A ssh-rsa 'thing' should be created with our favorite Putty ssh-gen program.
Two files are created.
The public one ( ?) has to be inserted into the admin account :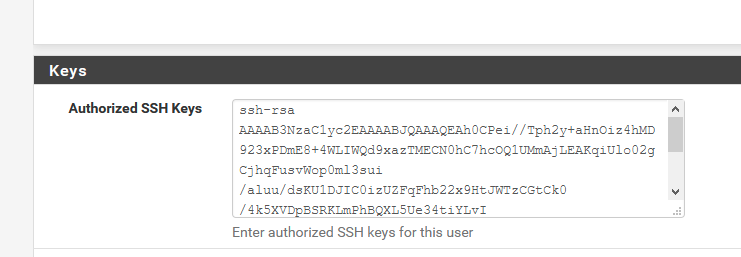
The private one should stay on your PC, or better, USB key. Or learn it out of your head. This cert can also be generated with a password - called a pass phrase.
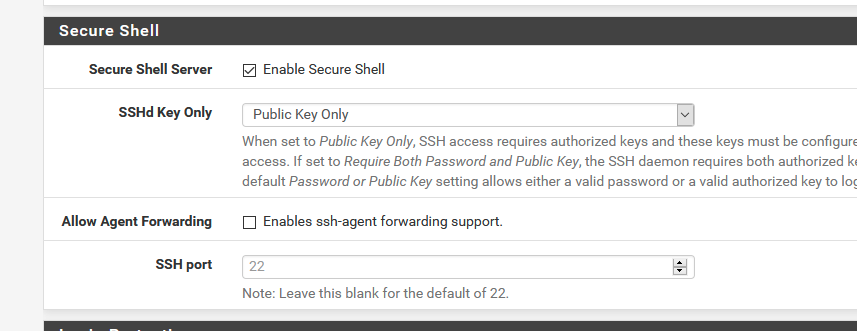
Now, password login is done.
You need the key file (the private thing).
Putty will throw out the login user 'root' for you - set it up to do so.
It won't ask for keyboard alike passwords anymore.It will ask the pass hrase of the cert :
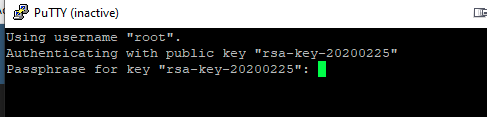
Enter the phrase and then your are logged in.
Now, all this doesn't change anything for the GUI login.
The good new is that pfSense isn't just some obscure device, it's your firewall and we, as admins, control and secure the firewall. Right ?!! That's why we use pfSense in the first place.
Real nerds do it like this :
The pfSense 'box' is locked up.
The LAN interface - as the console interface, are NOT connected.
All the other interfaces are used for hostile WAN and LAN clients. And now the fun part : all these clients can not use ports 80 and 443 and 22 of our firewall pfSense. You just have to create a block rule that does this. Easy !
Problem solved. No more 'root' issue.Variant : on your LAN, only accepts traffic to port 22 - 80 - 443 TCP from your IPv4 and or IPv6 (the device you use to admin pfSense).
Or, another variant : use VPN also from LAN to login.
Or : shut down SSH access (not my advise - SSH is gold, as it also gives you SFTP which enables the real power. Still protected by a cert).
IMHO : Just to say : all this 'su' or 'sudo' is discussion is not really needed in this case.
The major week point is the GUI now - hide it as explained above.
And direct hardware (console port) access or screw driver access. -
You should made a tutorial how to hardening pfsense here or on Youtube.
One thing, just remember your pfsense can be compromised without you knowing it (no logs). Especially attack on cloud with ssh. For example,
service syslogd stop
adduser -D
Username. johndoe.
login group: wheel
pkg install sudo
vi /usr/local/etc/sudoers
root ALL=(ALL) ALL
johndoe ALL=(ALL) ALLVoila!