IPSec VTI Tunnel to Unifi USG
-
Solved: We have hit a bug (https://forum.netgate.com/topic/161833/issue-with-21-02-and-not-with-2-5-0) and therefor things didn't work as expected.
Hi everyone,
I am pretty new to the pfsense community and in the process of evaluating if we switch from Cisco appliances to netgate.
We have a couple of XG-7100-1U devices for testing running pfsense 21.02-RELEASE-p1.In some locations we have Unifi USG-4-Pro devices running which we connect with a ipsec site2site vti based tunnels to our cisco appliances. Unfortunately I am struggling a bit to connect one of the USGs via vti to pfsense. Both appliances are directly connected to the internet with static ips.
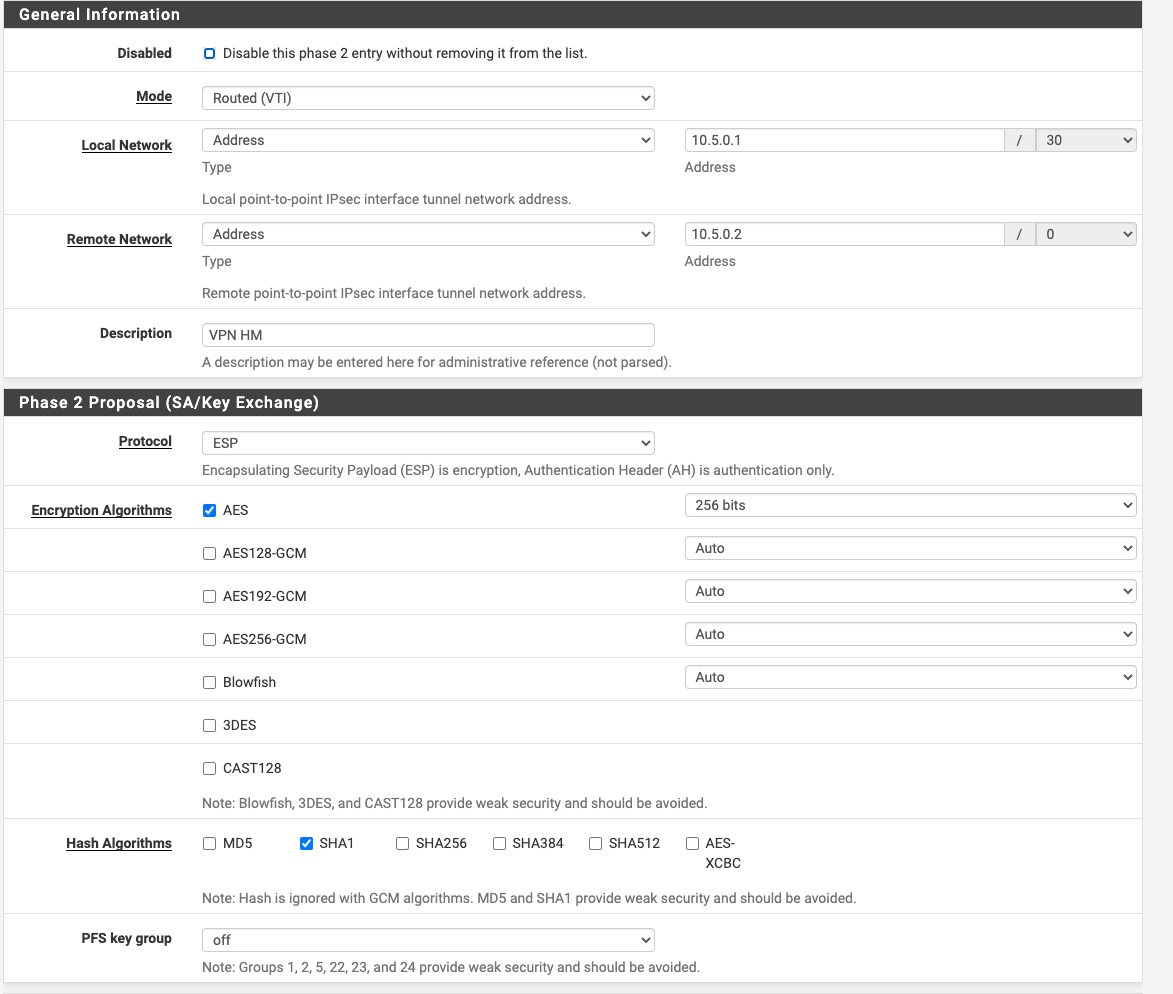
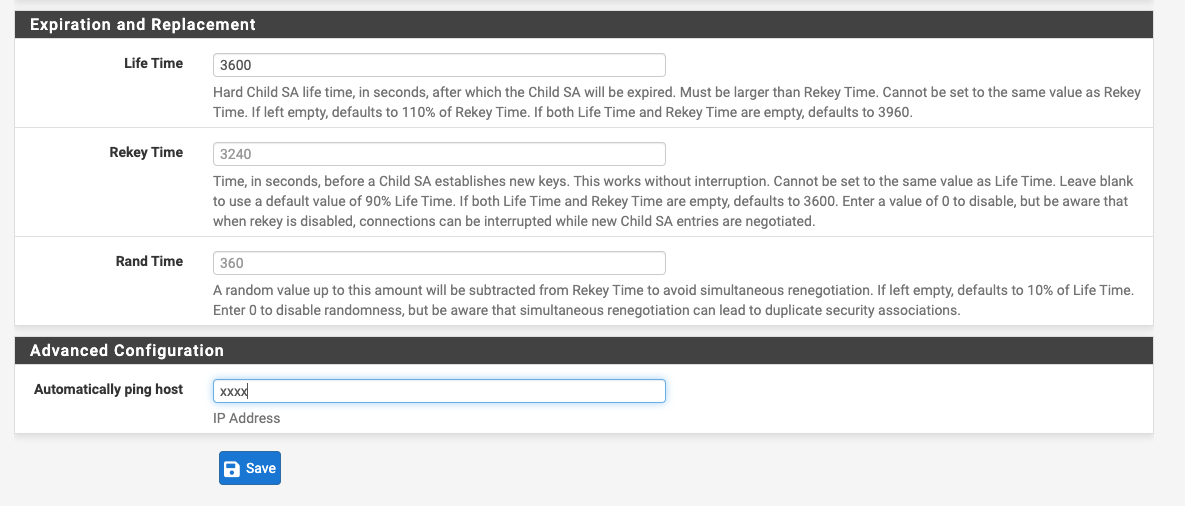
First the link comes up and is routed perfectly. ICMP traffic passes through but as soon as we put some traffic on it, the tunnel collapses.Here is our config on the pfsense appliance:
Phase1:
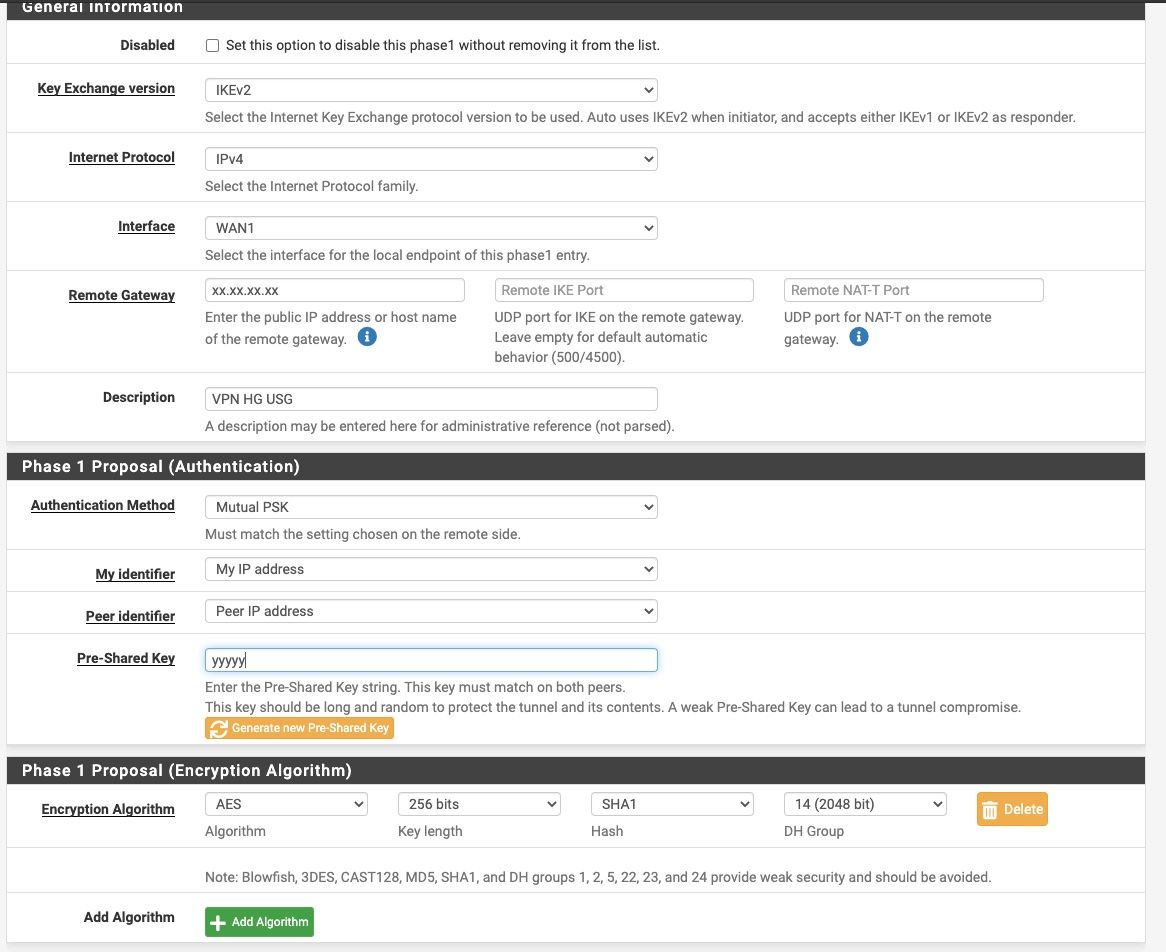
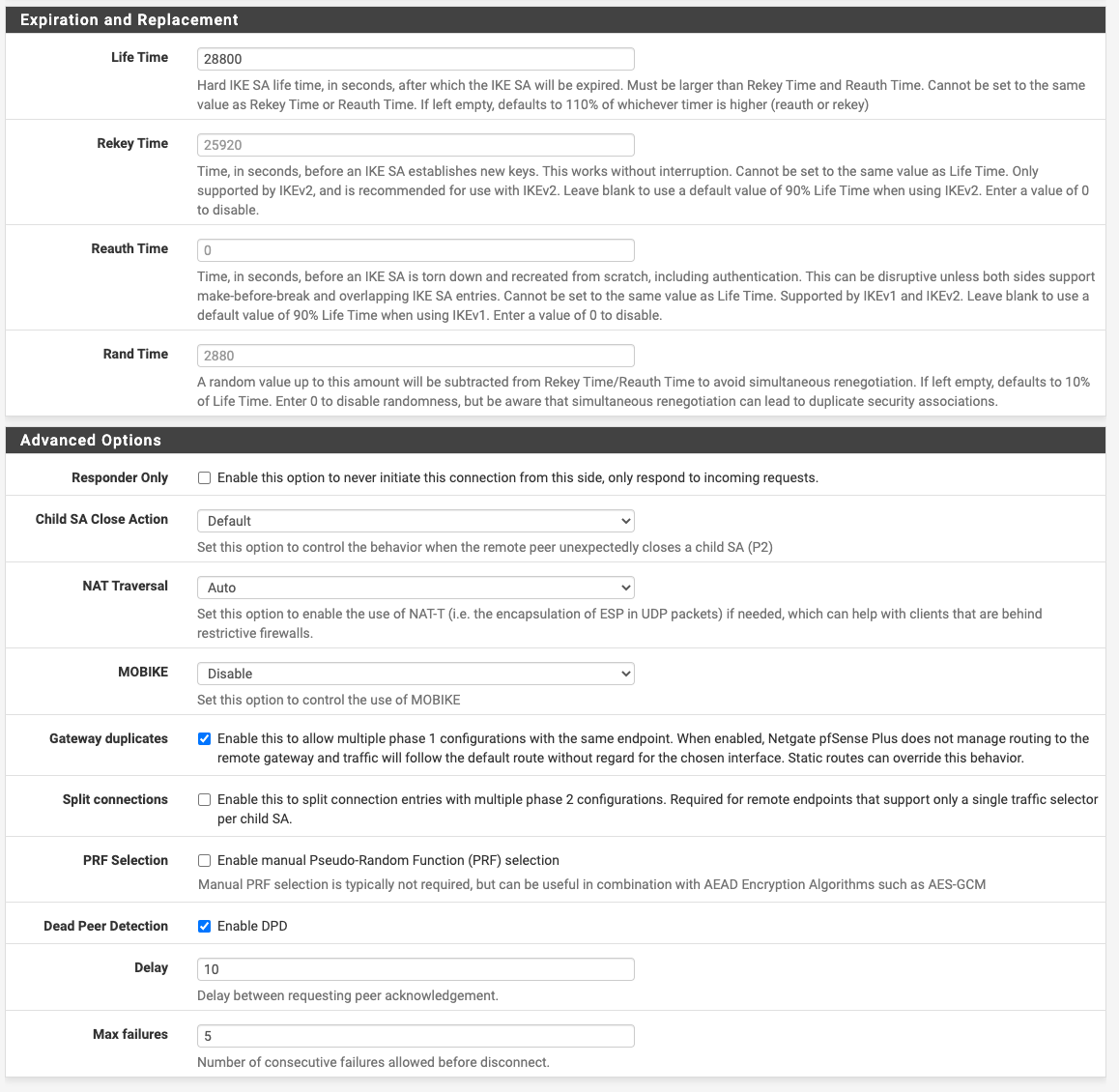
Phase 2:
USG (I am saving you basic info such as ip etc., they are triple checked and perfectly inline though ;-) ):
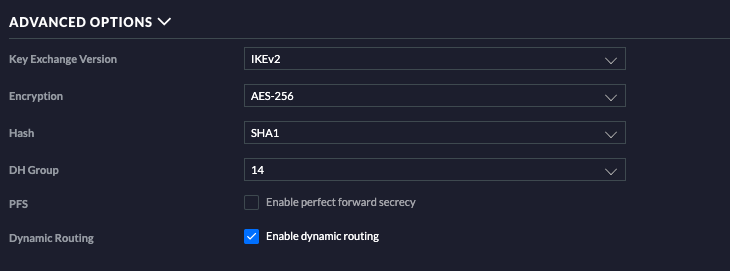
I have already played with the MTUs and the MSS clamping features. Nothing so far. There is not option in the USG to define a transport network ip set such as in the pfsense. We managed with other ipsec systems though to get it to work anyway. I have tried setting something like 0.0.0.0/0 in the pfsense as well and some other combinations. No luck so far.
The firewalls are both wide open and the routes are set (ICMP traffic is flowing both directions till the collapse). When the tunnel collapses the phase 1 and 2 both show as up and connected.
Interesting is that the automatically by pfsense created gateway is always offline. This might be due to the above describe transport net issue.
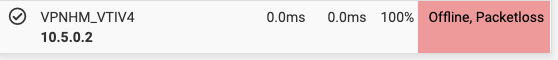
Since both pfsense and the usg are based on strongswan I figure there must be a way to get it work ;-) Maybe someone here has a good hint for me? I have been putting quite some hours into it so far.
Thanks,
Hannes