IPv6 Firewall Rules
-
Hi All,
Hopefully a simple one. Just getting my setup fully IPv6 enabled, now that I finally have my head around it + subnetting etc.
So I have around 40x VLANS on pfSense.
For each interface, I used to do the following
RULE 1 - Allow X Traffic to other VLANS where required
RULE 2 - BLOCK ALL Traffic to Private IPv4 Address Range
RULE 3 - Allow ANY Outbound (Limited to certain ports if required)This works perfectly. Simple, secure, and stopped VLANS being able to talk to other VLANS unless required.
With IPv6 though, how can I achieve the same result? As there is no longer a Private IPv6 Range / Subnet, as they are all publicly routable IPv6 Addresses.
Thanks, Scott
-
@smaxwell2 said in IPv6 Firewall Rules:
As there is no longer a Private IPv6 Range / Subnet, as they are all publicly routable IPv6 Addresses.
That's why you shouldn't assume that IPv6 is like IPv4.
Check your own device, as it has parable a 'public IPv6'.
But it also a non-public address like :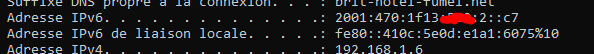
( the "liaison locale" )
It's probably time to do what you did when you mastered IPv4.
-
@gertjan Thanks.
Bit more clarification
Still if I allow INTERFACE1 to ALL IPv6 HTTP for example. That will allow Any Device on INTERFACE1 to talk to ANY VLAN on HTTP
How does your suggestion prevent that, but still allow IPv6 HTTP Internet Access for example ?
-
@smaxwell2 said in IPv6 Firewall Rules:
How does your suggestion ....
The suggestion I made that this :
@smaxwell2 said in IPv6 Firewall Rules:
As there is no longer a Private IPv6 Range / Subnet, as they are all publicly routable IPv6 Addresses.
isn't true.
See my image.
It's very common that devices have multiple IPv6 addresses.Rules :
Something like this :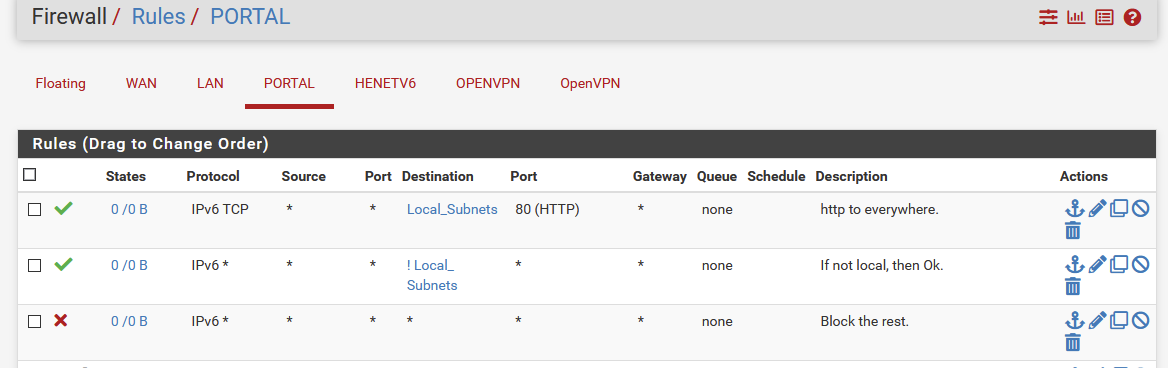
I list only IPv6 here.
The final, third rule, "block all" isn't really needed. -
Just like you have rule #2 preventing access to the private IPv4 range, create a rule that prevents access to your IPv6 prefix range. I'm assuming that your IPv6 prefix is static (I certainly hope it is if you have 40 VLANs).
For example, if your prefix is 2001:aaaa:bbbb:cd00::/56, create a rule that prevents access to that entire address range. Now your various VLANs won't be able to communicate with each other via IPv4 or IPv6. Of course, if you use pfSense for DNS, NTP, etc., I hope you've allowed those through other rules, because that block would also prevent communication with pfSense.
If you want to allow communication between two VLANs, create a single rule for both IPv4/v6, and use the "[interface] Network" selection for the destination... that will include both the IPv4 and IPv6 subnets for the VLAN that you select.