Configuration Help
-
I am switching from an Edge Router X to using pfSense on an old PC with 1 NIC and a 4 NIC card. I was originally going to configure pfSense pretty much the way the ERX was configured, which used 1 port for the WAN and the other 4 ports were configured as a switch and went to other switches in various rooms in the house. But after reading many posts that say not to configure pfSense as a bridge/switch due to performance penalties I am looking for suggestions.
All switches are 1G managed and support VLANs and cabled to the basement of a 2-story house.
I tried to provide the location of all the switches and what is connected to them, but it keeps telling me the post is flagged as spam.
I have 2 Unifi APs, on located in the basement and one located on the first floor. So they are on different switches. They will have 3 SSIDs, House LAN, Quest and Camera.
Should I add another 4 Port NIC to pfSense and cable each of the Switches through out the house directly to pfSense?
I like being able to see the Traffic Graphs is why I think this may be a good idea.
I assume this would mean each pfSense NIC would be a different sub-net?
Can each NIC/sub-net DHCP use the same pfSense domain name and the devices and use the name to connect to other devices on a different sub-net, like PC to TrueNAS?
How would this handle the current Unifi APs being on different NICs, but need to have the same sub-net address range and VLAN sub-net address range?
-
@jca001 said in Configuration Help:
How would this handle
I would get another smart switch that can do vlans. Then from that switch connect all your downstream switches or AP.
Make sure you get switch with enough ports to handle all your downstream switches/devices and leaves a few ports for growth, and has enough ports to leverage ports on pfsense for uplinks of different vlans, or just as a lagg and to provide more bandwidth.
This allows you to put any device anywhere on any vlans, and also allows for more physical bandwidth between your vlans to not be limited by all things connected to 1 physical interface on pfsense with vlans.
So for example you have 4 connections from pfsense to your 1st switch. That you can either lagg and just hope for no physical hairpins of intervlan traffic. Or you can manual pick what vlan(s) are on each uplink.. If you only have 4 vlans total... Then you can have a 1 gig uplink for each vlan to pfsense. If you have 8 then you could have 2 vlans on each uplink, if you have 12 then 3, etc..
Or any combo of that you want.. Trying to make sure that vlans that do a lot of traffic between them don't share the same physical uplink from your switch..
Can draw you a picture if you want..
edit
Here you go - something like this... Where you have 8 vlans A,B,C,D,E,F,G and H.. so you put 2 vlans on each uplink to pfsense. And then maybe your wifi ssid vlans are only a subset of your total.. This allows you to put any device anywhere on any vlan. And leverages multiple physical interfaces into pfsense for routing at wire speed.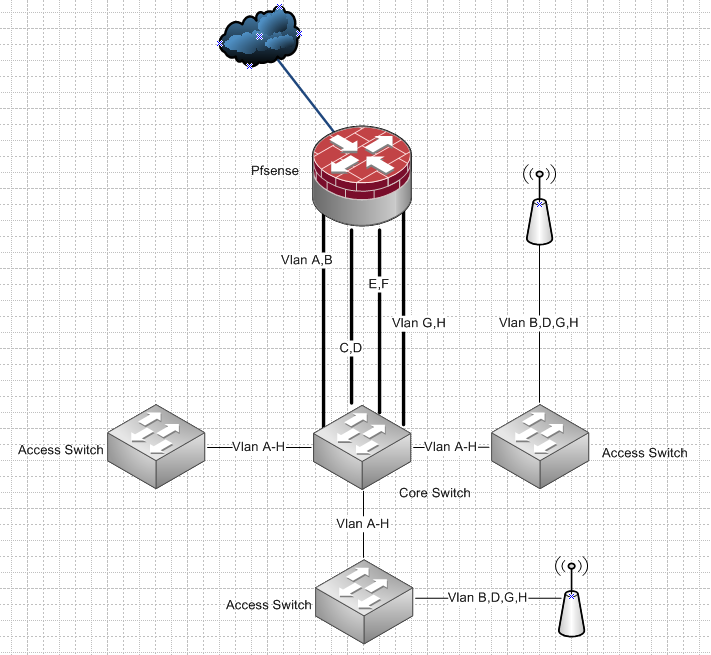
A 8 port gig switch that can do vlans can be had for like $40.. So its not a huge cost, but allows for full flexibility to really do anything you want putting any device anywhere on any vlan. And you don't have to do any software bridging on pfsense, and still get to leverage all of its physical ports. How you distribute the vlans across your uplinks from your switch is up to you. Maybe 3 uplinks only have 1 vlan each, and the 4th has 5 vlans on it that don't talk to each other or are wireless only vlans, etc etc..
Or just create a lagg from pfsense to your switch and throw all the vlans on the lagg. But that doesn't allow you fine control over what vlans are on what physical path, and you could have some intervlan traffic that hairpins that you don't want to hairpin due to bandwidth needs, etc.
Such a setup also allows you to add AP anywhere, be it your core switch or a downstream access switch and use whatever vlans you want.. Just make sure you get a switch that allows for growth at your core.. if understanding correctly the hardware you currently have a 8 port should be enough.. So maybe get a 16 port to allow for growth..
On the switch ports connected to your AP, I would prob just trunk all your vlans.. This would allow you to fire up a new SSID and put it on any vlan you want without having to touch the switch port configuration.
If really on a budget.. You could move 1 of your access switches to be core (connected to pfsense).. And then just get a dumb switch for one of your locations - if all the devices that will be connected to that switch are just going to be in the same vlan. But cost savings there is only a few dollars really.. Since an entry level smart switch is like 5 to 10$ more than its dumb switch sister model..
The above model is pretty much what I have setup - but my uplinks from my core switch only have 1 vlan on them. Other than the uplink that handles wifi vlans.. The wifi vlans don't talk to each other anyway.. And have no wifi device that ever goes over about 400mbps anyway via wifi.. So makes sense to let those devices share the same physical path..
-
Thanks for the quick reply.
As I stated in my original post I tried to list the switch locations and the devices connected to them but kept getting an error about spam. I will try again doing it a little differently.
The cable modem, router, 24 port switch, server running proxmox with several VM including truenas are all located in the basement. The new pfsense will be physical there too. One of the APs is also locate in the basement.
On the first floor there is a 8 port switch in the kitchen with a PC, TiVo and TV.
Also on the first floor there is a 5 port switch in the family room with TiVo and TV.
Also on the first floor there are 2 8 port switches in the office with 2 PCs, couple RPis, home automation controller, TiVo, TV, physical NVR (test cameras are directly connected) with 1 on main LAN, one of the APs.
Future plans are to install several cameras fed from the attic to a 8 port POE switch in a closet on the second floor cabled to the basement. The physical NVR is being scarped and a VM will be doing NVR. The 2 APs will be mounted at each end of the house on the second floor connected to a 5 port switch cabled to the basement.
Does this change your suggested configuration?
-
Some additional information and questions.
Most traffic is from the PCs, TiVo and TVs to the internet. Once a week the PC will do backups to the truenas VM and as I stated in my last post the camera will be going to a VM NVR.
Should all the switches be on the main/base LAN 192.168.1.N default VLAN 1 untagged for administration?
Then use say 192.168.10.N VLAN 10 for most devices, PCs, TV, etc?
Then 192.168.20.N VLAN 20 for Guest LAN?
Then 192.168.30.N VLAN 30 for Camera LAN?
-
Your switches IP would all be in your infrastructure vlan.. be that your lan or some other vlan doesn't matter. But no I wouldn't put the management IP of your switches in different vlans.
Doesn't really matter where your switches are - but it you have 2,3 or 103.. If you have a 24 port switch next to pfsense makes it easy.. Just use as many uplinks that you want from the switch to provide the bandwidth you need want, and how many interfaces your pfsense box has.
This allows you to put any device anywhere, be it a downstream switch your core switch or an AP on any vlan you want. And lets you leverage your physical interfaces in pfsense for bandwidth - and not doing some stupid bridge in pfsense.. When you have a switch right there that can do that for you..