NAT Port Forward Trouble with 21.02
-
Hello,
I am having difficulty with inbound NAT port forward rules. I am aware of this thread and this issue, but I think this is a different problem, since I do not have an exotic WAN setup and some additional troubleshooting has also not worked.
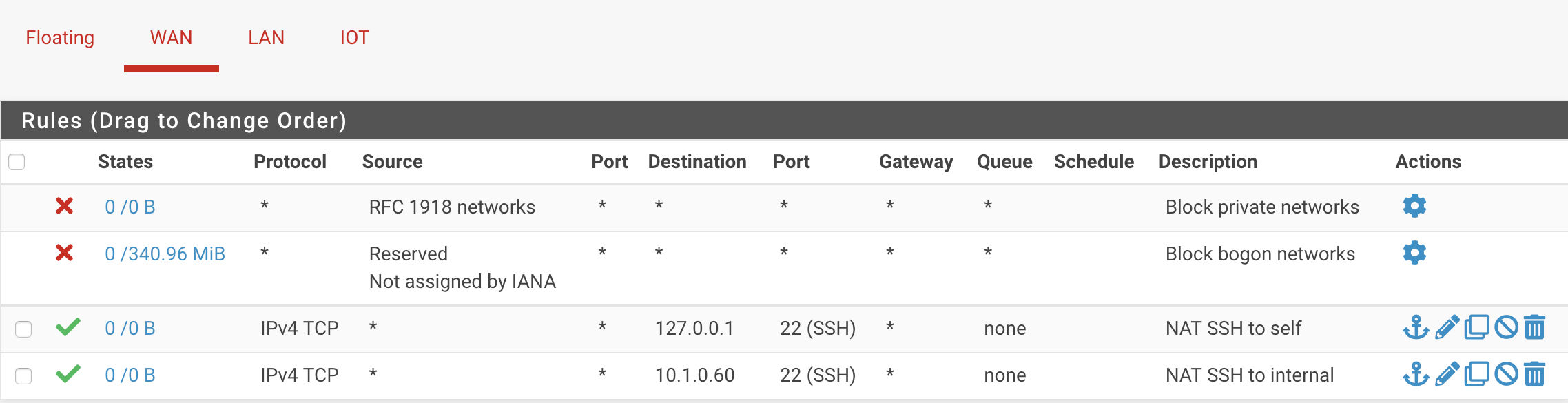
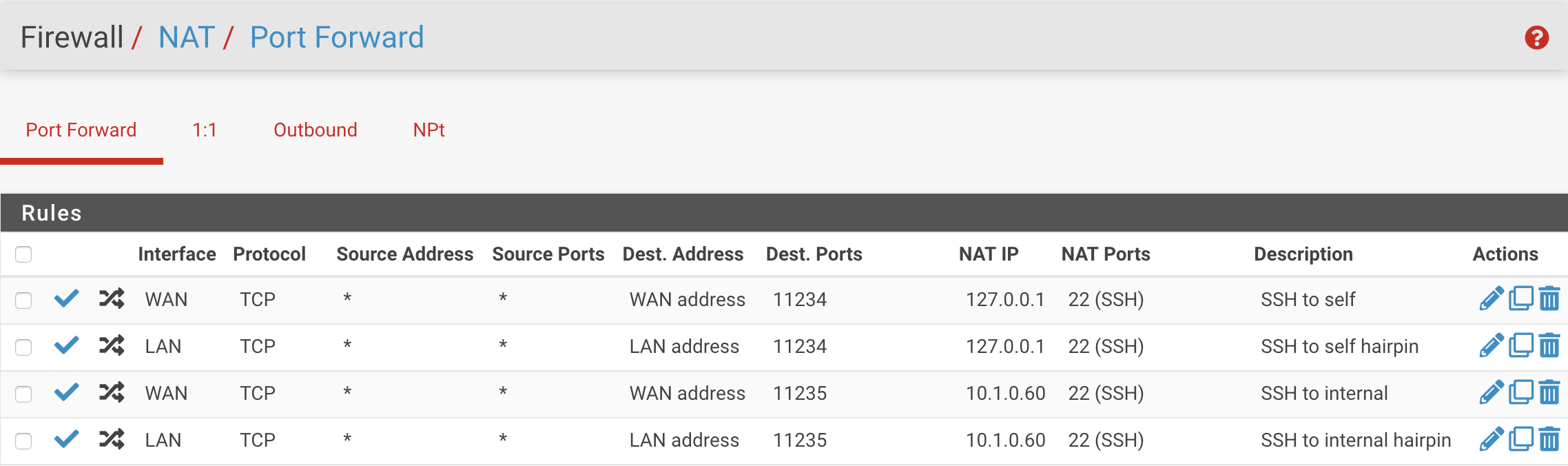
I have the following rules to allow SSH to the router and to an internal server from outside:
When I check the PF rule set, I see a few rules that confuse me:
$ pfctl -sn | egrep '22|ssh' no nat on mvneta0.4091 inet proto tcp from (mvneta0.4091) to 10.1.0.1 port = ssh nat on mvneta0.4091 inet proto tcp from 10.1.0.0/24 to 10.1.0.1 port = ssh -> 10.1.0.1 port 1024:65535 no nat on mvneta0.4091 inet proto tcp from (mvneta0.4091) to 10.1.0.60 port = ssh nat on mvneta0.4091 inet proto tcp from 10.1.0.0/24 to 10.1.0.60 port = ssh -> 10.1.0.1 port 1024:65535 rdr on mvneta0.4091 inet proto tcp from any to 10.1.0.1 port = 11234 -> 10.1.0.1 port 22 rdr on mvneta0.4091 inet proto tcp from any to 10.1.0.1 port = 11235 -> 10.1.0.60 port 22 rdr on mvneta0.1102 inet proto tcp from any to 10.1.0.1 port = 11235 -> 10.1.0.60 port 22Why are there
nat,no natandrdrrules? The last rule is also concerning:rdr on mvneta0.1102refers to a different VLAN, not the LAN interface, which ismvneta0.4091.I tried all the troubleshooting steps from the documentation:
- recreating the rules didn't change anything
- the firewall rules exist and are properly linked:
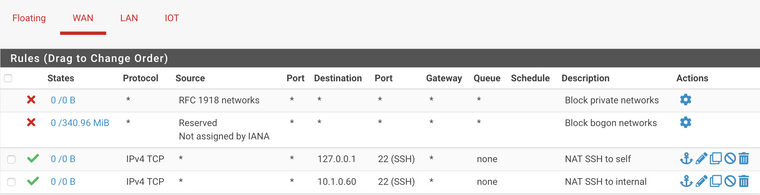
- tcpdumps show the packets arriving at the WAN interface and do not see them exiting the LAN interface, indicating a problem within the router or firewall
- firewall logs show the incoming packets being blocked by the default deny all rule
I also tried adding a pass rule on the WAN interface for source *, sport *, destination self, dport 22, but external traffic to port 22 was still shown as dropped in the firewall logs by the default deny all rule. I really can't believe that this just didn't work.
Additionally, the hairpin NAT rules appear to work fine: both
ssh -p 11234 10.1.0.1andssh -p 11235 10.1.0.1work and connect to the expected SSH servers.What's going on here?