Switching from Sonicwall NSA 4600 to a pfsense box
-
Hello, we will be switching from a SonicWALL NSA 4600 to a pfsense box, we don't have much NAT policies and access rules, but trying to figure out how to apply what I have from the SonicWALL to the PFSense is more complicated than I thought, is there a table or config tool somewhere or even someone on here that has experience in doing this ? there's about 30 NAT policies and 30 access rules on my existing SonicWALL that needs converting
-
@pjaneiro said in Switching from Sonicwall NSA 4600 to a pfsense box:
we will be switching from a SonicWALL NSA 4600 to a pfsense box
Hi,
Nope,

if you are looking for a migration tool such does not exist.
NAT rules mean the same thing everywhere, you only configure them in a different interface, hardware, SW, etc., but they have the same meaning...+++edit:
I would read this:
https://github.com/jaredhendrickson13/pfsense-api -
this is how sonicwall sets up their NAT policies
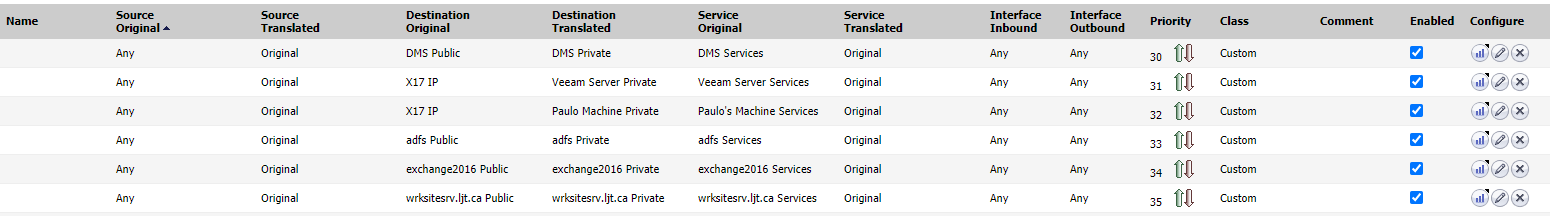
as you can see the NAT policies portion on PFSense is a lot more simpler and easier to use
So yeah, when I'm trying to decipher what from sonicwall goes where on the pfsense, it gets garbled in my head
-
@pjaneiro said in Switching from Sonicwall NSA 4600 to a pfsense box:
as you can see the NAT policies portion on PFSense is a lot more simpler and easier to use
You evoked memories in me (with the picture)

Yup, that's why I forgot the Sonicwall, a long time ago.
this is similar to configuring Cisco SMB fool FW and NATI can say that this will be manual work...
but I say the good news too, is pfSense is a very friendly "animal"Once you are done with the config you will enjoy it..
Forget the APIs, this is not a walkable path, I can already see.
-
@daddygo Hmm, not sure if I understand your post here, My post is about needing help trying to decipher what portions of the sonicwall nat rules are relevant to PFSense
-
@pjaneiro said in Switching from Sonicwall NSA 4600 to a pfsense box:
what portions of the sonicwall nat rules are relevant to PFSense
Okay, ALL because NAT rules don’t depend on what device you're applying to
if you need them you need to set them up
-
Bump Bump, just checking to see if anyone here has experience in this and has actual insight
-
@pjaneiro said in Switching from Sonicwall NSA 4600 to a pfsense box:
anyone here has experience in this and has actual insight
nothing serious happened
Everyone wants to get the job done easily, okay.

In this case, you need to do it manually, sorry.NAT is NAT, wherever it is set up...
(so anyone who deals with firewalls or routing must have an insight into this)I would do, -examine and collect the predefined NAT rules of the stupid Sonicwall one by one.
I would then create it in "edible" form in pfSense.There is no better way and I know there will be a lot of work.
I am with you in spirit, if you need help when you activate them (NAT rules) with pfSense, you can find us here.
-
Not wanting to get the job done for me or easily, I'm asking for help in transcoding what means what
like you wrote -
I would do, -examine and collect the predefined NAT rules of the stupid Sonicwall one by one.
I would then create it in "edible" form in pfSense.This is what I am trying to do, but on the pfsense half the crap on the sonicwall is not there
source original - source translated / destination original - destination translatedIf i look on the pfsense, if i try to match those rules, nothing works, so if there is a table somewhere where there are comparable rules that have been translated from a sonicwall to a pfsense that would be awesome and i'll be able to do the rest
-
Here's an example for HTTPS:
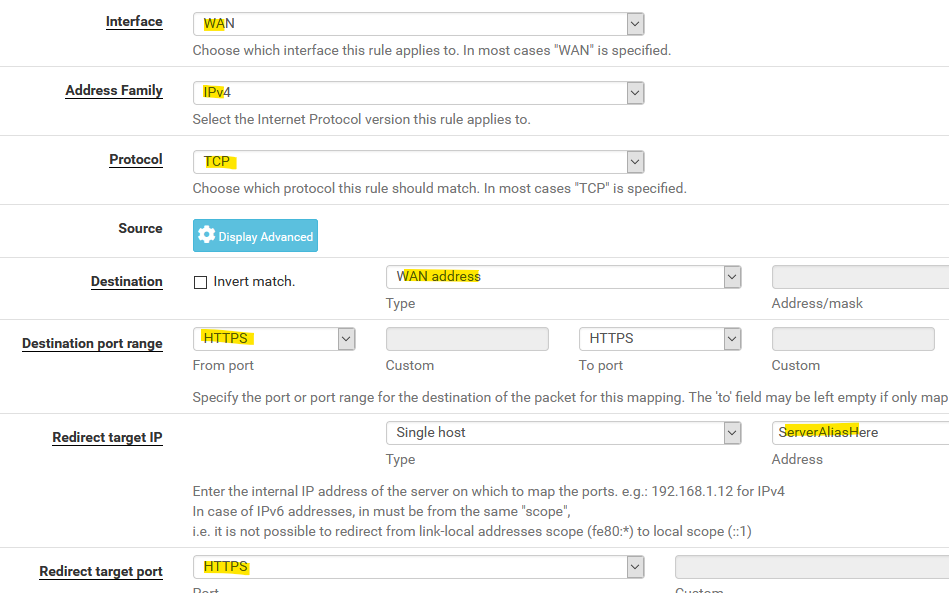
By default pfSense creates a firewall rule allowing the traffic ("Filter rule association" at the bottom of the page). -
@pjaneiro said in Switching from Sonicwall NSA 4600 to a pfsense box:
nothing works, so if there is a table somewhere where there are comparable rules that have been translated
Hi,
No one can do more for you than that, everyone learned pfSense from this book

https://docs.netgate.com/pfsense/en/latest/nat/index.htmlOf the Youtube stuff, I only recommend him:
https://www.youtube.com/watch?v=eb1pTs7XamAof course:
https://www.youtube.com/channel/UC3Cq2kjCWM8odzoIzftS04A/videosThere are no explicit migration tool or instructions from Sonicwall to pfSense, or I have never met one...
-
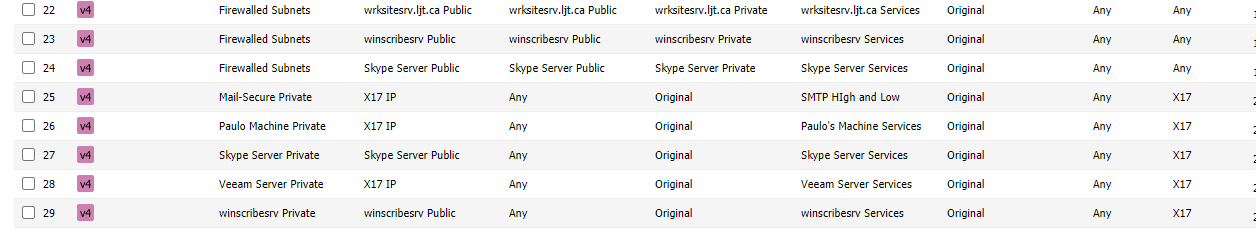
@steveits I'm looking at what you highlighted
And this is where I get really confused, All my rules and port forwarding are done
so my issue is what goes where here when I look at one set of my sonicwall rules for one of my services

this is where I do not quite grasp where what goes where
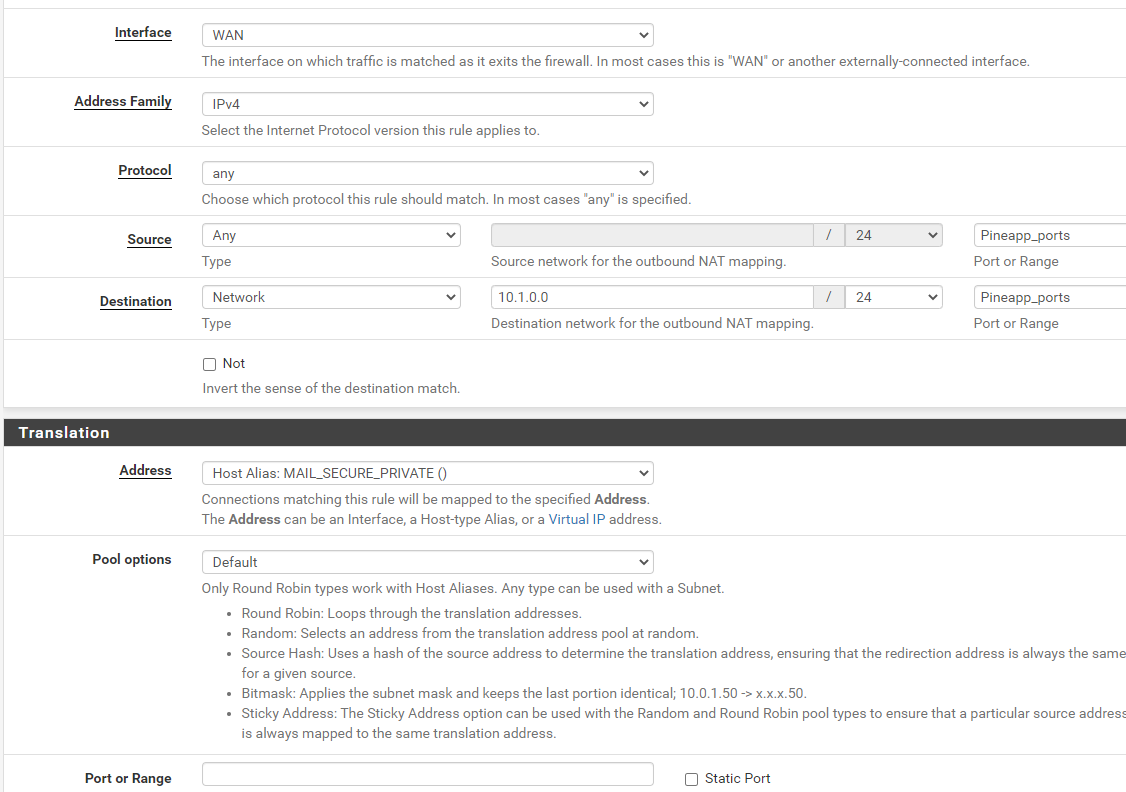
Since I do not transform my services (ports) I don't need worry about that
And I also know that rule that starts with firewalled subnets is the loopback rule, but that also confused the heck outta me, Is a loopback rule necessary for pfsense ?
-
Are you trying for inbound NAT redirection (RouterWAN:443 -> WebServerLAN:443) or outbound NAT? Those are very different and your screen cap is for outbound. Outbound makes the outgoing packet use a different IP address, useful for instance if one has 1:1 NAT mapping and the outbound connection should use that IP not the default IP.
-
Basically I have about 40 ip wan adresses, let's say someone from the outside is hitting one of my public servers at 2.2.2.2, pfsense should know that when wan IP 2.2.2.2 receives a packet it should be redirected to internal private ip 10.1.1.1 and when private ip 10.1.1.1 answer back the outside world should see that 2.2.2.2 is answering and not my firewall that has an ip of 2.2.2.7
Am i writing this ok or did i screw the pooch i my explanation ?
-
You're OK. So inbound would likely be 1:1 NAT then.
Our setup is old, but for Outbound probably either Hybrid or Manual with a manual entry for each server:
Source: 10.1.1.1/32
Destination: any (the Internet)
NAT Address: 2.2.2.2