Freeradius authentication - multiple instances (OVPN & wifi)
-
Good afternoon,
I am exploring the possibilities for FreeRADIUS implementation to authenticate OVPN users as well as wifi devices.
Currently I use the FreeRADIUS for OVPN authentication and the interface is set on 127.0.0.1. Everything works fine.
Additionally I am planning to implement the the FreeRADIUS authentication for my wifi APs. I suppose in that case the interface IP address cannot be 127.0.0.1 as this cannot be reached by the APs, right?
I imagine I could run 2 FreeRADIUS servers on the same pfsense instance. One of them would authenticate the OVPN access, as done until now. The other one would authenticate devices connected to internal wifi via EAP-TLS.
However when browsing the pfsense interface, I am finding just one general settings (e.g. FreeRADIUS -> EAP -> Certificates for TLS
Not sure if my conclusions are right, but does that mean I can run just one FreeRADIUS server on one pfsense machine? I can't combine google OTP (OVPN) and EAP-TLS (wifi)?
Is there any way how I could achieve running this concurrently, please?
Thanks a lot. -
Hi All,
anyone any good advice that could point me to the right direction?
Thanks a lot!
-
Hi there,
does anyone have any other suggestion how could I solve this? Namely if I am using FreeRADIUS as OVPN authentication, what other solution could I use to solve the wifi authentication?
Thanks. -
You can use the same instance for both, I bind to * in the Freeradius setup.
I auth my IPsec VPN users with an additional check-item of the NAS-Identifier, that way people with a Freeradius IPsec login can't use it for the WiFi.
NAS-Identifier == strongSwan
Do a radsniff -x and see if you can see two distinct items to check against.
Wi-Fi:- 2021-05-03 21:02:26.157681 (23) Accounting-Request Id 75 igb0:172.16.1.11:43489 -> 172.16.0.1:1813 +9.665 User-Name = "andyk" NAS-IP-Address = 172.16.1.11 Service-Type = Framed-User Framed-IP-Address = 172.16.2.40 Class = 0x61646d696e73 Called-Station-Id = "92-2A-A8-98-9D-8C:L-Space RADIUS" Calling-Station-Id = "40-9C-28-A2-E0-7E" NAS-Identifier = "922aa8989d8c" NAS-Port-Type = Wireless-802.11 Acct-Status-Type = Start Acct-Delay-Time = 0 Acct-Session-Id = "703ABEA9DEAE0FE5" Acct-Authentic = RADIUS Acct-Multi-Session-Id = "C87635AFF234D368" Event-Timestamp = "May 3 2021 21:02:26 BST" Connect-Info = "CONNECT 0Mbps 802.11b" WLAN-Pairwise-Cipher = 1027076 WLAN-Group-Cipher = 1027076 WLAN-AKM-Suite = 1027073 Authenticator-Field = 0xe586aa1ee22ca628977a554028cac278 VPN:- 2021-05-03 21:05:29.503569 (11) Accounting-Request Id 2 lo0:127.0.0.1:38961 -> 127.0.0.1:1813 +2.353 User-Name = "andyk-iphone" NAS-IP-Address = xx.xx.xx.xx NAS-Port = 23 Service-Type = Framed-User Framed-IP-Address = 172.16.8.1 Called-Station-Id = "xx.xx.xx.xx [4500]" Calling-Station-Id = "82.132.185.76[24639]" NAS-Identifier = "strongSwan" NAS-Port-Type = Virtual Acct-Status-Type = Stop Acct-Input-Octets = 500 Acct-Output-Octets = 1368 Acct-Session-Id = "1619107685-23" Acct-Session-Time = 3 Acct-Input-Packets = 7 Acct-Output-Packets = 7 Acct-Terminate-Cause = User-Request NAS-Port-Id = "con-mobile" Authenticator-Field = 0x2018ca67b8e56b3c97ae382c43ac3275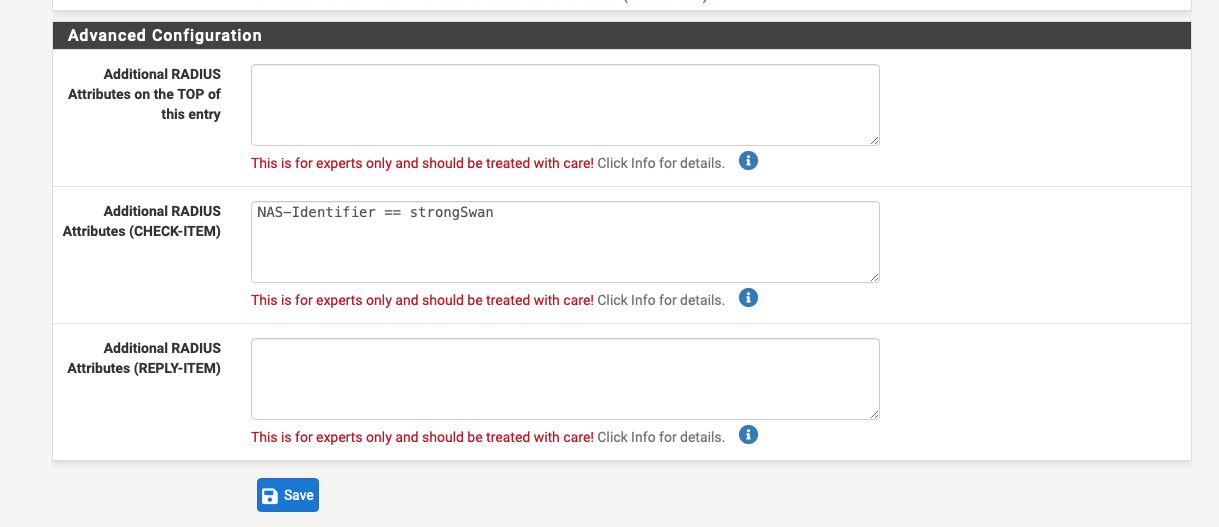
-
@nogbadthebad
May I ask you to elaborate on this a bit more, please? Is there any "howto" that could help me to set this up?
If I get it right this part "I bind to * in the Freeradius setup" means, you have in Freeradius->NAS/Clients in the part Client IP Address and asterisk instead an IP address, am I right?
How then I further setup the authentication? Just entering NAS-Identifier == strongSwan into "Additional RADIUS Attributes (CHECK-ITEM)? Or do I have to setup something else/additional as well?
Does this work together with google one time password?
Btw. if I do radsniff -x now, it says:radsniff: Failed opening pcap handle (stdin): truncated dump file; tried to read 4 file header bytes, only got 0 Logging all eventsThank you.
-
@marianhlusek said in Freeradius authentication - multiple instances (OVPN & wifi):
radsniff: Failed opening pcap handle (stdin): truncated dump file
Are you running radsniff from the pfsense web page or after a ssh to your router, it needs to be done via ssh and then try and connect via OVPN.
The users with andyk-device have NAS-Identifier == strongSwan as a check item, andyk doesn't, this means if they tried to connect via WiFI using andyk-device it would fail.
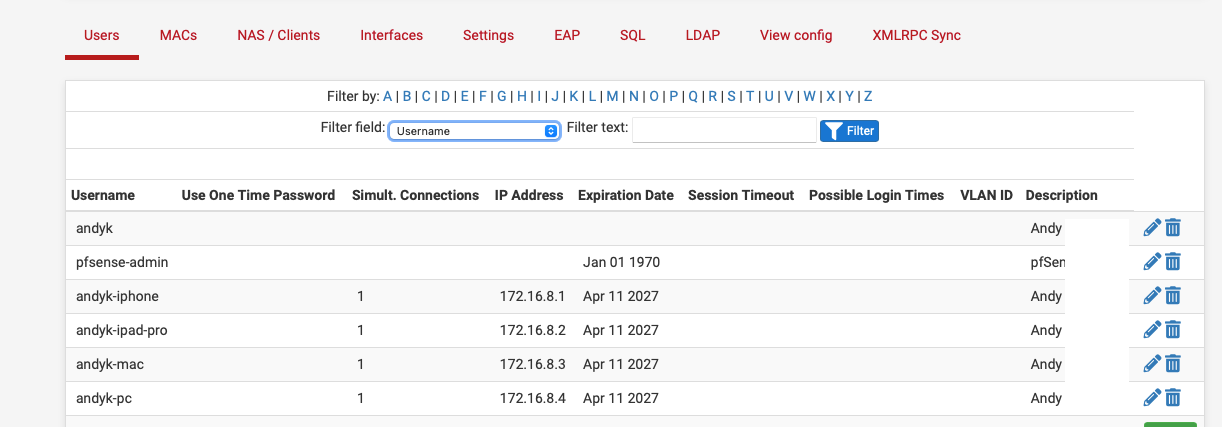
The NAS-Identifier is the application or device thats doing the radius request, in my case its the IPsec VPN server or the the MAC address of my Ubiquity access point.
Your best bet would to be have a look here:-
https://freeradius.org/
https://freeradius.org/rfc/attributes.html/
https://wiki.freeradius.org/config/Operators
Not sure about OTP as I don't use it, but isn't the OTP setting per user, maybe create two accounts per user, one for wifi and the other for VPN.
-
@nogbadthebad
Cool, looks interesting. Thank you. I'll try.
Yes, the Google OTP is per user, so it looks like I'll have to create every user twice (not huge effort).