Split DNS zone
-
I use DNS Resolver (unbound) to split zones between local and public records.
So for example: greentree.systems resolves to 192.168.110.20 when someone queries it from the LAN.
If the query where to be run from the internet, the answer would be: 192.64.119.41This is fine for A records.
However, sendmail also queries the DNS and although there is no override record of the MX type (I don't see that's possible), the service returns the A record 192.168.110.20.
Is ti possible to configure the Resolver in pfSense to only return what was overridden and queriy the rest from the internet public DNS servers. This works for different zones, but is it possible in the same zone/domain?
-
I've read a lot about this issue and it seems that dnsmasq (the forwarder) may have some config options to do this. Is that so or am I mistaken?
-
@lifeboy Are you saying that when you specifically ask DNS Resolver for an MX record you are getting an A record instead?
Are you positive it's not your resolver client failing to receive an MX record and subsequently asking for an A record?
The default DNS resolver configuration asks the authoritative servers for a domain for anything it doesn't have a local override for (transparent mode).
You can make DNS Resolver (unbound) return pretty much any kind of record even though there are no GUI knobs for it.
https://www.nlnetlabs.nl/documentation/unbound/unbound.conf/
(Look at
local-datathere and putunbound mx recordinto your favorite search engine)Pretty sure I am not understanding exactly what you are saying though.
-
@derelict, not that's not quite what I'm asking.
If I add a host override for a domain (e.g. greentree.systems), then it doesn't return an MX record at all, even though the actual domain out on the public internet does have an MX record.
So if I ask for the A record I get the override record. If I ask for MX I would like to get the non-override record, but I don't.
-
@lifeboy Do you know how to use dig? Show the dig output.
-
@derelict, of course...
My default DNS is pfsense.
~# dig greentree.systems
; <<>> DiG 9.11.3-1ubuntu1.11-Ubuntu <<>> greentree.systems ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19746 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;greentree.systems. IN A ;; ANSWER SECTION: greentree.systems. 3600 IN A 192.168.131.188 ;; Query time: 0 msec ;; SERVER: 192.168.131.254#53(192.168.131.254) ;; WHEN: Mon Mar 29 11:34:18 SAST 2021 ;; MSG SIZE rcvd: 62The host override record is returned
~# dig greentree.systems MX
; <<>> DiG 9.11.3-1ubuntu1.11-Ubuntu <<>> greentree.systems MX ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26959 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;greentree.systems. IN MX ;; Query time: 0 msec ;; SERVER: 192.168.131.254#53(192.168.131.254) ;; WHEN: Mon Mar 29 11:34:25 SAST 2021 ;; MSG SIZE rcvd: 46but, no mx record returned
~# dig @8.8.8.8 greentree.systems MX
; <<>> DiG 9.11.3-1ubuntu1.11-Ubuntu <<>> @8.8.8.8 greentree.systems MX ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 61736 ;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;greentree.systems. IN MX ;; ANSWER SECTION: greentree.systems. 59 IN MX 10 aspmx2.googlemail.com. greentree.systems. 59 IN MX 10 aspmx3.googlemail.com. greentree.systems. 59 IN MX 5 alt1.aspmx.l.google.com. greentree.systems. 59 IN MX 5 alt2.aspmx.l.google.com. greentree.systems. 299 IN MX 1 aspmx.l.google.com. ;; Query time: 190 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Mon Mar 29 11:34:33 SAST 2021 ;; MSG SIZE rcvd: 179Public DNS record has mx
~# dig @8.8.8.8 greentree.systems
; <<>> DiG 9.11.3-1ubuntu1.11-Ubuntu <<>> @8.8.8.8 greentree.systems ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 3063 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;greentree.systems. IN A ;; ANSWER SECTION: greentree.systems. 1798 IN A 192.64.119.41 ;; Query time: 190 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Mon Mar 29 11:34:37 SAST 2021 ;; MSG SIZE rcvd: 62public ip returned
-
@lifeboy This looks like expected behavior in unbound.
https://utcc.utoronto.ca/~cks/space/blog/sysadmin/UnboundLocalDNSOverride
https://forum.netgate.com/topic/112091/dns-resolver-host-overrides-ability-to-choose-record-types
There is, however, a specific type of override you can use. See Also
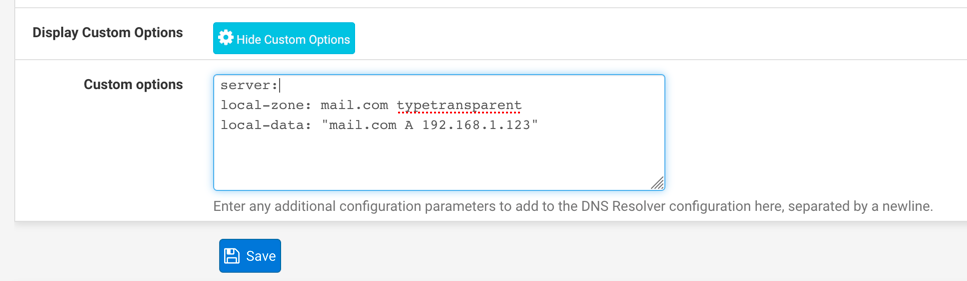
typetransparentin the aforementioned unbound documentation.Instead of specifying a host override in the gui (delete it), try this manual custom configuration:
server: local-zone: greentree.systems typetransparent local-data: "greentree.systems A 192.168.131.188"This might require other work depending on what other overrides you have in that zone.
I have advised against using "domain names" as A records for decades for similar reasons. Back in the day it was moronic MTA developers (usually programming on Windows) that would just resolve the A record for a mail domain instead of an MX record and attempt to deliver mail there even though mail for that domain was handled somewhere completely different.
Despite my advice, "marketing" pretty much invariably wins that argument.
-
@derelict said in Split DNS zone:
I have advised against using "domain names" as A records for decades for similar reasons.
Yeah single label domains - have always been a bad choice ;) Never a fan of pointing A to domain name either.. if your zone/domain is greentree.systems.. Then point the A to a host in that domain host.greentree.systems
greentree.systems looks to be single label domain, systems, which a host greentree.
-
That's actually doing the job! Excellent!
I removed the override record for greentree.systems and added these two rows to the custom options.
Now the override works for the A record, but retains the public DNS MX.
~# dig greentree.systems
; <<>> DiG 9.11.3-1ubuntu1.11-Ubuntu <<>> greentree.systems ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38548 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;greentree.systems. IN A ;; ANSWER SECTION: greentree.systems. 3600 IN A 192.168.131.188 ;; Query time: 0 msec ;; SERVER: 192.168.131.254#53(192.168.131.254) ;; WHEN: Mon Mar 29 15:53:13 SAST 2021 ;; MSG SIZE rcvd: 62~# dig greentree.systems MX
; <<>> DiG 9.11.3-1ubuntu1.11-Ubuntu <<>> greentree.systems MX ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54874 ;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;greentree.systems. IN MX ;; ANSWER SECTION: greentree.systems. 59 IN MX 10 aspmx2.googlemail.com. greentree.systems. 59 IN MX 10 aspmx3.googlemail.com. greentree.systems. 59 IN MX 5 alt1.aspmx.l.google.com. greentree.systems. 59 IN MX 5 alt2.aspmx.l.google.com. greentree.systems. 299 IN MX 1 aspmx.l.google.com. ;; Query time: 0 msec ;; SERVER: 192.168.131.254#53(192.168.131.254) ;; WHEN: Mon Mar 29 15:53:08 SAST 2021 ;; MSG SIZE rcvd: 179I see the resolver has the option to be run as "type transparent" overall, but there is no option to add local-data via the GUI. Would that be something I can submit as a new feature request?
-
-
@johnpoz said in Split DNS zone:
@derelict said in Split DNS zone:
I have advised against using "domain names" as A records for decades for similar reasons.
Yeah single label domains - have always been a bad choice ;) Never a fan of pointing A to domain name either.. if your zone/domain is greentree.systems.. Then point the A to a host in that domain host.greentree.systems
greentree.systems looks to be single label domain, systems, which a host greentree.
I understand the sentiment, but on the other hand, any half-baked programmer should be able to ask a domain for it's MX records when attempting to send mail, yet in this case it's postfix (of all!) that simply tries the A record anyway, when no MX record is returned. Maybe there's a switch one can use to force it not to do this and rather generate an error...
-
-
This is the part of that I like the most ;)
Specify "ignore_mx_lookup_error = yes" to force a DNS A record lookup instead. This violates the SMTP standard and can result in mis-delivery of mail.This violates the SMTP standard and can result in mis-delivery of mail.
-
@lifeboy said in Split DNS zone:
postfix (of all!) that simply tries the A record anyway, when no MX record is returned
As Derelict implied above that's actually correct behavior per RFC. Assuming the answer was indeed returned, and blank.
https://tools.ietf.org/rfcmarkup?doc=5321#section-5
"If an empty list of MXs is returned, the address is treated as if it was associated with an implicit MX RR, with a preference of 0, pointing to that host."Nice there's a workaround. I guess all these years the times I've had to set up split DNS it was for a hostname (office.example.com) and not a domain.
-
@derelict said in Split DNS zone:
http://www.postfix.org/postconf.5.html#ignore_mx_lookup_error
The default is "no", so an mx lookup error should be an error. As was pointed out by @SteveITS, per the RFC if there's no MX record returned, the host address is attempted.
The "type transparent" server setting fixed the problem for me, but I'd like to explore why setting the server type to "type transparent" in the GUI doesn't have the same effect.

It seems this is only for the domain of the system. Can it be set for all domains that are served by this server?
-
@lifeboy Because that is for the pfSense system domain. Not host overrides.
You can look at the configuration pfSense generates in /var/unbound.
-
Yeah that allows you to use a domain that is public, and look up non local resources. I personally think it should default to static.. To prevent queries for domain that doesn't exist in the public space.
I have mine set to static, since the domain I use locally doesn't exist in the public space - so no point in trying to resolve public if there is no local record..