Multiple IPsec Mobile Clients
-
Hi,
I need to set up multiple IPSec Mobile Setups with different Auth Server, WAN IP and LAN Subnets on one pfSense installation.
As i've seen this topic came up last time in 2017 and i'm unable to find something new about it, or how to solve such a scenario.I would be glad if somebody could help me out with it.
Best Regards
Phil -
@ironphil Using the built-in IPSec VPN feature (mobile) it can’t be done. There’s only support for one instance of the built-in mobile IPsec VPN engine.
You should look into OpenVPN to get your needed features. It allows for multiple running instances.
-
Hello @ironphil , what do you need? I've implemmented IPsec remote clients with AD auth. If this scenario could help you please let me know.
-
@viniciusmerlim I have multiple VLANs with different Active Directories behind one pfsense. Each user should be able to log in to the Ipsec VPN with their own AD Credentials and should only have a Phase 2 Entry for their corresponding VLAN net.
Does anyone know if there s a chance to realize that with some direct configuration changes or is such a feature planned in the future? I have multiple WAN IPs, so i can easily assign one WAN IP for each VLAN Mobile config if needed.
-
@ironphil Like I said, pfSense IPSec can only have one instance for mobile users, so you can’t create an individual IPSec setup pr. AD.
On normal IPsec VPN boxes you could handle your situation by creating several IPSec instances, or you could radiusproxy your different Radius/AD’s from a local FreeRadius package, and have the different radiusservers return a group ID so you could apply different firewall rules to different users. But pfSense IPsec does not support that either, so I’m sorry to say it again, but if you want to use pfSense, you need to use OpenVPN to solve your needs. The built-in IPsec mobile features are very rudimentary - works great for a simple one type user/network setups, but it is useless for more advanced setups.
The Mobile feature is a sort of “bolt on” to the Site-2-Site IPsec engine. It was originally a site-2-site design it was created for.
-
@keyser said in Multiple IPsec Mobile Clients:
It was originally a site-2-site design it was created fo
Hi,
I have a similar question here link text.
I understanding correct that is not possible to implement something like what in the schema below?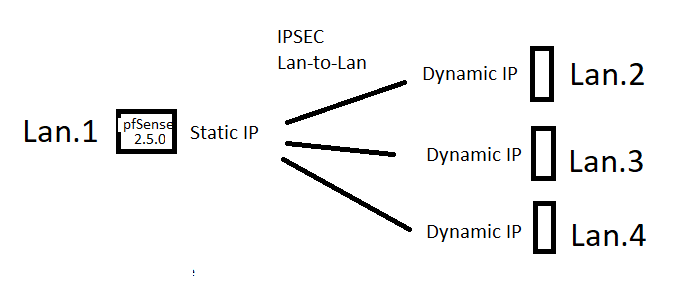
Best Regards
Albe -
Well that should indeed be possible without any trouble. All you really need to make sure is that you are not using Mobile VPN for the setup but instead create a unique P1+P2 for each connection, and make sure the identifiers are specific for each connection (so it can tell each remote apart).
Since they are using Dynamic IP, I would make sure to have the remote sites register a DYNDNS name for their IP, and have the tunnel endpoint and identification use that name.
-
@keyser thanks' for the answer, is that mandatory to register DYNDNS? because configure 3 different P1+P2 only one VPN goes up (seems a difficult to distinguished link)
Best Regards, and thanks' again.
Alberto -
@alberto-0
No, DYNDNS is not mandatory - you can configure the remote endpoint in each P1 by IP adress instead. but if you do, then you need to reconfigure your tunnel every time the endpoints change IP. That’s why DYNDNS makes it easier.You need three different P1 +P2’s on your central box - how would it otherwise be able to distinguish the 3 endpoints from one another? Each of them also needs different IP subnets routed i P2 - otherwise the routing will fail and it cannot know which tunnel to use for which traffic.
-
@Alberto-0 you can also use a noip free account.
-
@viniciusmerlim ok, thanks' a lot for answers. I used no-ip to configure all af three VPNSs!
-
@alberto-0 Then it won’t work because you are in effect using the mobile IPsec framework.
With Mobile IPSec only the client can initiate the connection, and you are not using remote site routing where the central hub can initiate the tunnel.So like I said, you need to create three distinct P1+P2’s centrally that connects to the remote device IP in P1, and have a distinc IP subnet for each site in P2
-
I have multiple IPsec in place. But only 1 mobile. For each site-to-site you need to create P1 and P2 like @keyser said.