Can't connect to internet hosts when VPNed into internal VPN Server behing PFSense Router
-
Hey Folks,
Newby here with PFSense, running 2.5.0.
All in all, got the setup going fine, but having some problems with my OpenVPN Server connections, where my VPN connected devices (OpenVPN Server running on a separate host in my network through port forwarding) can not connect to any internet hosts.
See diagram for my setup:
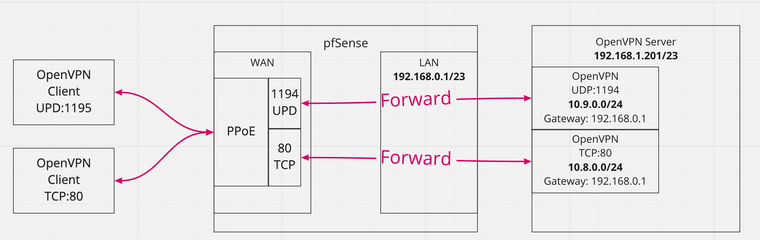
With the setup, I can connect to the OpenVPN Server(s) from the outside (UPD or TCP). When connected I can ping/http/ssh to any of the IP addresses in my LAN Address Space (192.168.0.0/23).
However, I can not access any hosts on the internet (Ping/HTTP etc).
I want my VPNClients internet connections to go through my OpenVPN Servers and out through my PPoE/WAN so that they appear to be coming from my network.
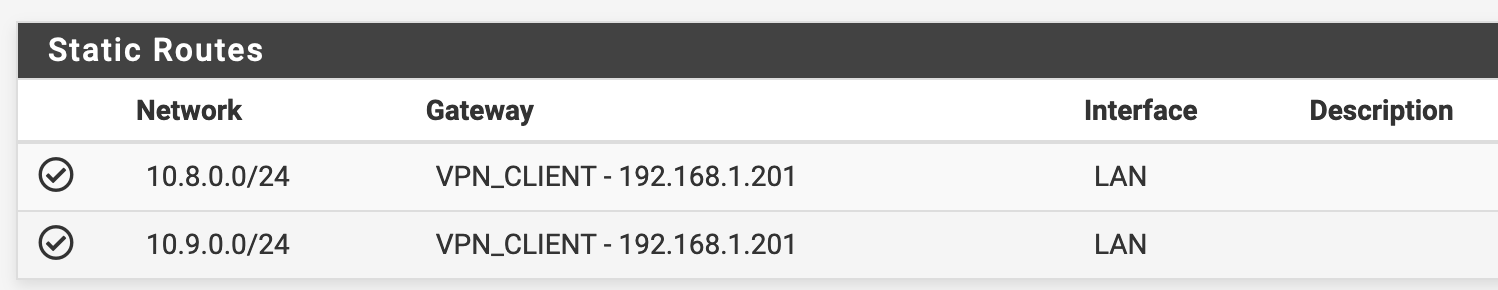
I previously had this working with a Tomato/Shibby router and the exact same OpenVPN Servers (although the LAN network was 192.168.0.0/24 previously), but I remember had to add static routes on the router for 10.8.0.0/24 and 10.9.0.0/24 to go through the OpenVPN Server Host - 192.168.1.201. otherwise, the responses from the internet hosts could not find their way back to the VPN Clients through the VPN Servers.
So, I added a gateway for the OpenVPN Host to PFSense and added 2 static routes for the 2 VPN network address ranges. But no go.
I also added (not sure if I need it) Outbound NAT rules for the VPN Networks to NAT through the WAN:
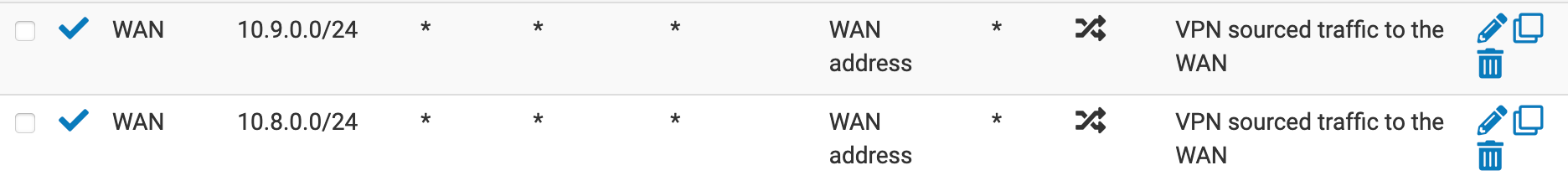
But still no go.Any ideas of what I am missing? Is it the mix of /23 and /24 network address ranges that is causing the issue?
Please let me know.
Cheers
G./
-
I added a firewall rule to log if I am passing or dropping traffic from LAN on 10.9.0.x to the WAN, but it looks like they are being passed on:

Is there a way I can check if the responses are being routed back to the 10.9.0.x network over the static route to 192.169.1.201?Cheers
G./
-
OK, I worked it out!
I had the following Firewall rule for LAN:

But of course, the 10.8.0.0/23 and 10.9.0.0/23 (I changed them to /23 instead of /24) are not in the "LAN Net", so I had to add extra rules to allow that traffic out:

That as well as the static routes fixed it!