Authenicated NTP
-
Auth. NTP servers give you a bit more safe feeling, because they are knowing how many users are using that servers!
Its not like "tomorrow 15 million users" begin using that server and it is going down or responding slower, the delay is growing or the server is not any more responding.I use a mix of more then one NTP and also want to let it grow. At first I use NTP servers pool over WAN they are
connected to or based on an atomic clock. Might be the
best in my eyes. I have a fallback line over LTE for a
second chance to get the time over the internet.
The LTE modem has also a GPS antenna connected
so I got one more time source.The next way to set up was a miniCPIe GPS (only) card
inside of the pfSense and all is fine now.- wired internet
- wireless internet
- gps only
May be that auth. NTP server will be an option on top of all, because they know then the amount of users exactly
and can set up another one if the responds time goes down or will be lower and not anymore so fast. -
@dobby_ in the early 2000s we use to have to set the DTE and DCE clock rates for the network routers to work correctly, if they had no clock rates set they would not function. Imagine something like a Ciena or Juniper backbone system today, how perfectly in time they have to be to support supernet city to city communications. Time is amazing stuff as it is time of use specific.
-
@jonathanlee said in Authenicated NTP:
@lamaz were you ever in the past having issues that's with time jumps 10-15 mins around noonish?
Thankfully I've never seen this behavior. It would have driven me mad as well when taking the OSCP exam and I was down to the wire.
I haven't been using multiple servers.
Maybe I shouldI'll grow my list. There are only 4 servers that support authenticated NTP according to https://tf.nist.gov/tf-cgi/servers.cgi.Nice touch ensuring that no local hosts are trying to skirt around your NTP. I do the same thing with both NTP and DNS. Local DNS requests get re-mapped to my pfSense DNS which then does it over TLS. I watch my WAN and ensure no traffic is going out on UDP port 53 :).
EDIT: I did it. Thanks @JonathanLee for the informative posts on NTP. I learned something new today.
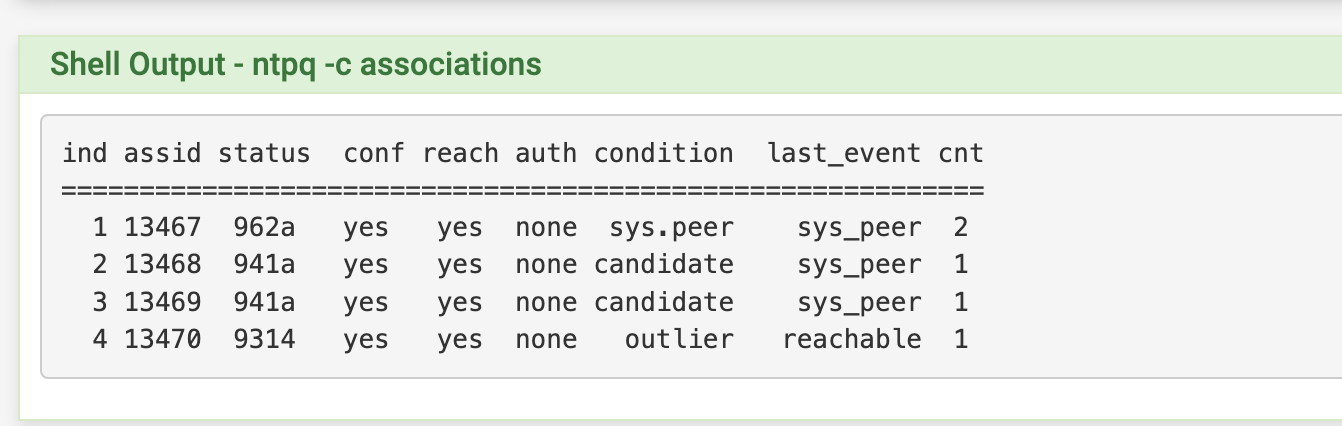
[23.01-RELEASE][admin@your-sweet-pfsense-server-name]/root: ntpq -pc as remote refid st t when poll reach delay offset jitter ============================================================================== *ntp-g.nist.gov .NIST. 1 u 62 64 3 5.755 +0.244 1.500 +ntp-c.colorado. .NIST. 1 u 65 64 3 44.843 +0.668 1.292 +ntp-wwv.nist.go .NIST. 1 u 64 64 3 45.135 -1.426 1.312 +ntp-b.nist.gov .NIST. 1 u 66 64 3 42.373 -1.416 1.486 ind assid status conf reach auth condition last_event cnt =========================================================== 1 30934 f61a yes yes ok sys.peer sys_peer 1 2 30935 f414 yes yes ok candidate reachable 1 3 30936 f414 yes yes ok candidate reachable 1 4 30937 f41a yes yes ok candidate sys_peer 1Full tinfoil hat.
-LamaZ
-
Folks,
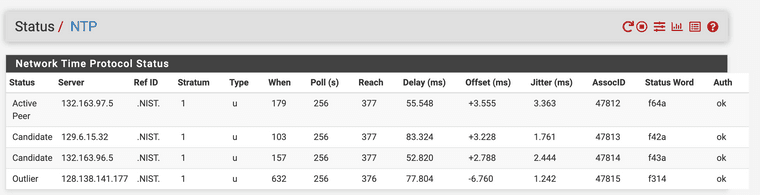
In an effort to facilitate checking the status of authenticated NTP, I've added some columns to the NTP Status page to parse the output of
ntpq -c associationsas defined in the ntpq Command spec. Let me know what you folks think.The last 3 columns have been added (AssocID, Status Word, Auth). I only added those 3 to the GUI, but I added the plumbing for the most of the fields in case someone wanted to display them as well.
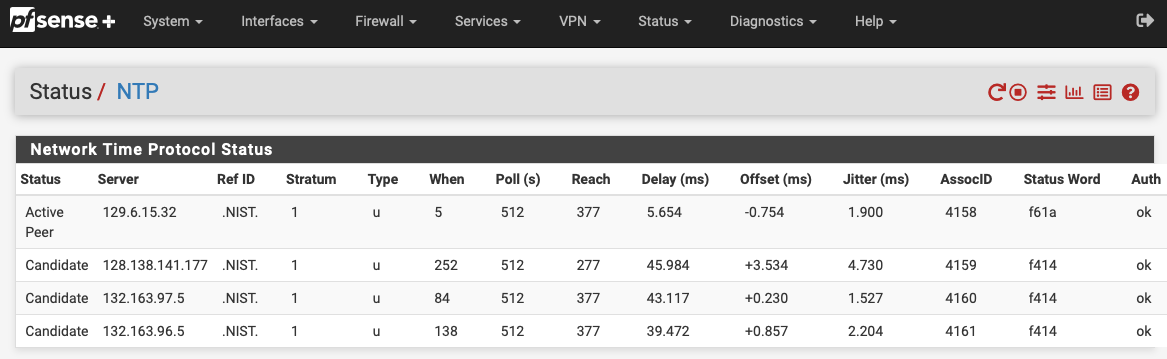
Patch file provided if you want to try it out. It worked for me :)
status_ntpd.php.auth.patchPS - I'm trying to unlock my Redline account to add this as full fledged feature request. Somehow I'm not getting the password reset email at the moment.
-LamaZ
-
@lamaz I just got my official secure email from NIST and was given a key and a value, do I only use the value inside of pfsense, it seems to work correctly with that again I will need your patch to see if it authenticated correctly. COOL encrypted secure time!!
-
I added my key however it is not using auth
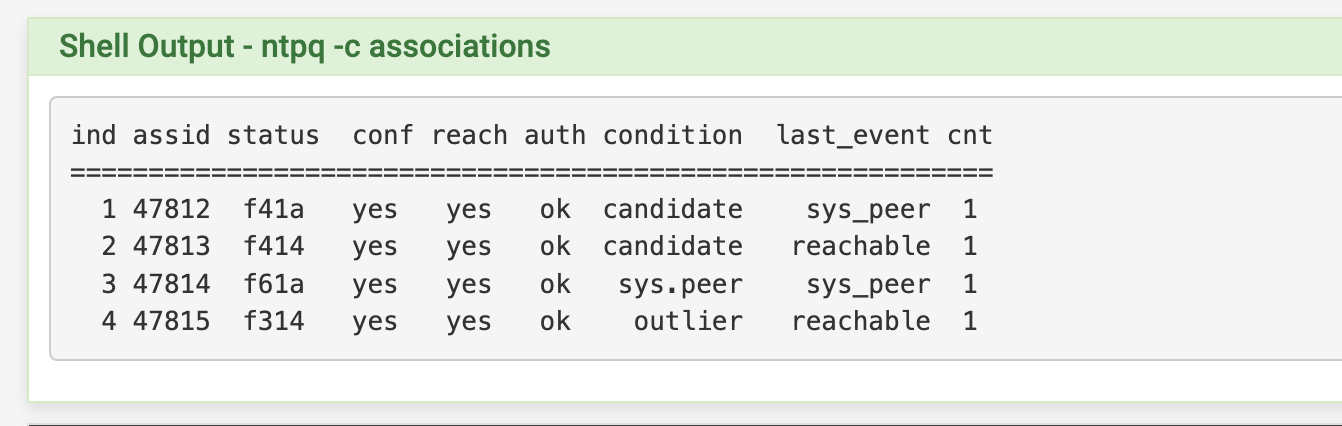
With your patch so I can add my key number to use with key value now it works !!! Thanks -
@lamaz I am going to open a redmine ticket for you as this is missing the key value and redirect the ticket to this page so others can see this.
-
-
Awesome! Warms my heart to see someone else getting value out of these patches and that they are working for others.
@jonathanlee said I am going to open a redmine ticket for you as this is missing the key value and redirect the ticket to this page so others can see this
Let me know how that goes. I tried many moons ago to get it added with no luck. Here is the last time I tried: https://redmine.pfsense.org/issues/8794
I'd follow up myself, but I somehow can't reset my redmine password. I'm guessing too many recent reset password attempts from my IP. The password apparently can't be too complex.
-LamaZ
-
@lamaz that is from 2018 ?? Wow I added some notes in your older ticket just now.
-
@lamaz thank you for the patches. I appreciate you.
If you wanted the leap second file this is the one I am using
https://www.ietf.org/timezones/data/leap-seconds.list
-
@jonathanlee Has it been that long?! Time flies.
-
@jonathanlee Just added the leap seconds to my setup. Thanks for the tip!
I like that I tried adding my comments to the file and it validated the hash. Put another it gave me an "signature mismatch" because something had changed. I went back and copy/pasted as-is and now have the leap seconds properly setup.
cat /var/log/ntpd.log | grep leap Mar 3 19:02:51 pfSense ntpd[61552]: leapsecond file ('/var/db/leap-seconds'): signature mismatch Mar 3 19:03:36 pfSense ntpd[75239]: leapsecond file ('/var/db/leap-seconds'): good hash signature Mar 3 19:03:36 pfSense ntpd[75239]: leapsecond file ('/var/db/leap-seconds'): loaded, expire=2023-06-28T00:00:00Z last=2017-01-01T00:00:00Z ofs=37-LamaZ
-
@jonathanlee Off topic, but how do you get Status/NTP to sort like you have shown? 2.6 CE to 22.01 and 23.01 Plus all act weirdly when trying to sort by columns, for me. Thanks.
-
@jonathanlee said in Authenicated NTP:
@johnpoz you can fax them also I just did, I want to test this, I have seen time jumps during cyber security classes in the past. 10-15 min jumps. Maybe this will fix it again with the use of my firewall I have not seen that in a while. Still I want to check it out. "Users who wish to use this service should send a letter to NIST using the US mail or FAX machine (e-mail is not acceptable)."
@JonathanLee - do they still require a static IP address or can a host name be given instead (in case the IP is dynamic)? Thanks in advance.
-
@tman222 I was required to provide the IP address provided to me by my ISP.
-
@deliver I installed the patch that is listed above. LamaZ provided it to us, I am very thankful for it. Use the 23.05 version
-
@lamaz time flys haha
 as we talk about time servers
as we talk about time servers -
 D Dobby_ referenced this topic on
D Dobby_ referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
@LamaZ said in Authenicated NTP:
@LamaZ said in Authenicated NTP:
Folks, just upgraded to 23.05 and these patches still work. Copy them to your /root folder (that's ~ for admin).
cd /etc patch -u -b /usr/local/www/status_ntpd.php -i /root/status_ntpd.php.auth.patch patch -u -b inc/system.inc -i /root/system.inc.ntp-auth.23.01.patchI periodically come back to this thread and remember what I've done over the years :).
-LamaZ
-
I have a PR open that incorporates the patches @LamaZ made (more or less) as well as adds a key ID field to the web GUI. If anyone is interested in testing it out to make sure I didn't miss anything, I can upload equivalent patch files here.
pfsense/pfsense#4658