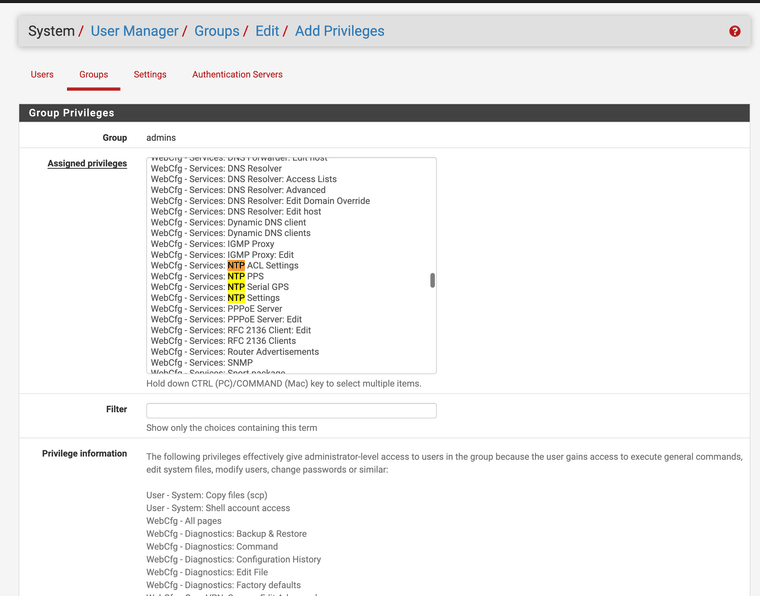
Authenicated NTP
-
@lamaz thank you for the patches. I appreciate you.
If you wanted the leap second file this is the one I am using
https://www.ietf.org/timezones/data/leap-seconds.list
-
@jonathanlee Has it been that long?! Time flies.
-
@jonathanlee Just added the leap seconds to my setup. Thanks for the tip!
I like that I tried adding my comments to the file and it validated the hash. Put another it gave me an "signature mismatch" because something had changed. I went back and copy/pasted as-is and now have the leap seconds properly setup.
cat /var/log/ntpd.log | grep leap Mar 3 19:02:51 pfSense ntpd[61552]: leapsecond file ('/var/db/leap-seconds'): signature mismatch Mar 3 19:03:36 pfSense ntpd[75239]: leapsecond file ('/var/db/leap-seconds'): good hash signature Mar 3 19:03:36 pfSense ntpd[75239]: leapsecond file ('/var/db/leap-seconds'): loaded, expire=2023-06-28T00:00:00Z last=2017-01-01T00:00:00Z ofs=37-LamaZ
-
@jonathanlee Off topic, but how do you get Status/NTP to sort like you have shown? 2.6 CE to 22.01 and 23.01 Plus all act weirdly when trying to sort by columns, for me. Thanks.
-
@jonathanlee said in Authenicated NTP:
@johnpoz you can fax them also I just did, I want to test this, I have seen time jumps during cyber security classes in the past. 10-15 min jumps. Maybe this will fix it again with the use of my firewall I have not seen that in a while. Still I want to check it out. "Users who wish to use this service should send a letter to NIST using the US mail or FAX machine (e-mail is not acceptable)."
@JonathanLee - do they still require a static IP address or can a host name be given instead (in case the IP is dynamic)? Thanks in advance.
-
@tman222 I was required to provide the IP address provided to me by my ISP.
-
@deliver I installed the patch that is listed above. LamaZ provided it to us, I am very thankful for it. Use the 23.05 version
-
@lamaz time flys haha
 as we talk about time servers
as we talk about time servers -
 D Dobby_ referenced this topic on
D Dobby_ referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
@LamaZ said in Authenicated NTP:
@LamaZ said in Authenicated NTP:
Folks, just upgraded to 23.05 and these patches still work. Copy them to your /root folder (that's ~ for admin).
cd /etc patch -u -b /usr/local/www/status_ntpd.php -i /root/status_ntpd.php.auth.patch patch -u -b inc/system.inc -i /root/system.inc.ntp-auth.23.01.patchI periodically come back to this thread and remember what I've done over the years :).
-LamaZ
-
I have a PR open that incorporates the patches @LamaZ made (more or less) as well as adds a key ID field to the web GUI. If anyone is interested in testing it out to make sure I didn't miss anything, I can upload equivalent patch files here.
pfsense/pfsense#4658 -
@MatthewA1 That's amazing can you post the patch, I would like to test it on 23.05.01 "pfSense Plus"?
-
@JonathanLee Thanks! I tested on a CE 2.7.1 VM as I only have one Plus device, and it's very much a production device. Here are the three patch files. I'm not 100% sure they are compatible with Plus as I have not looked at the PHP source files for 23.09, but I don't believe there is any difference with the modified sections in CE vs Plus.
These are created based on master+9257345. It seemed to work fine with my NTP server, but it would probably be good if someone could test against NIST NTP servers (as I also just setup my GPS based NTP server, so it's possible it was misconfigured but worked anyways)
system.inc.patch
status_ntpd.php.patch
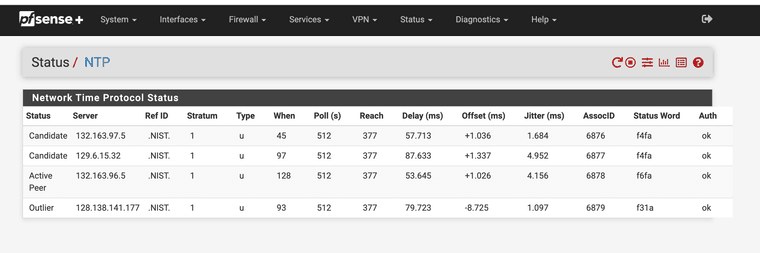
services_ntpd.php.patchAlso, the table on the NTP status page is wider than the title header. I'm not sure there is a way to fix that other than removing one of the columns. If anyone has suggestions, please do share.
-
@MatthewA1 @LamaZ his was the same way with the column issue see below.
-
All of them show ok under debug thanks for doing this.
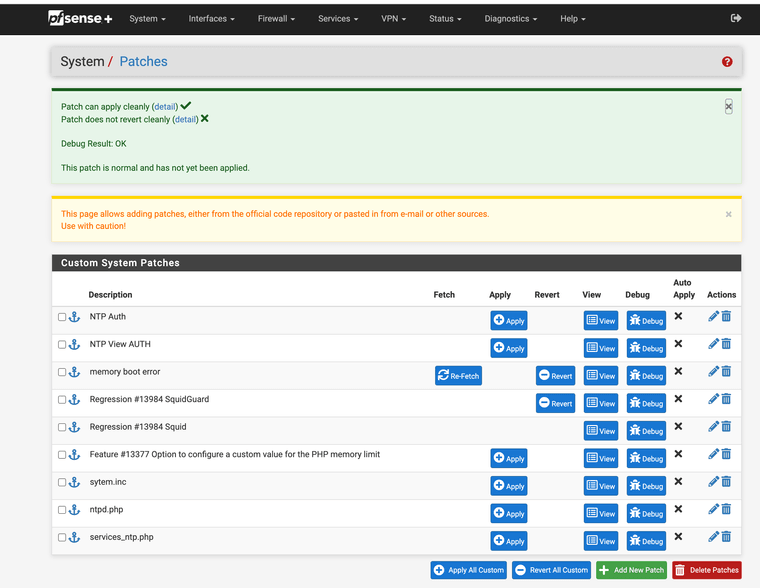
I had to remove /src from all the patches or they would not work with plus that was the only issue strip count zero
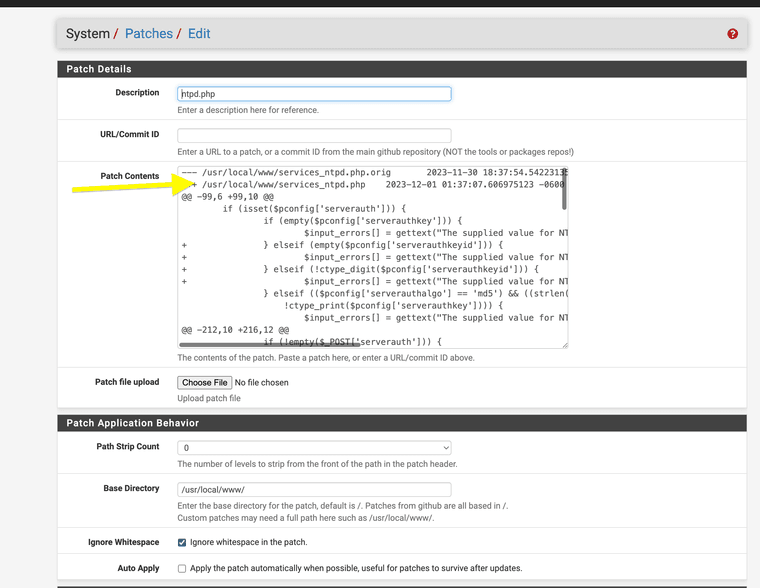
System works as expected for input area YEAH!!!
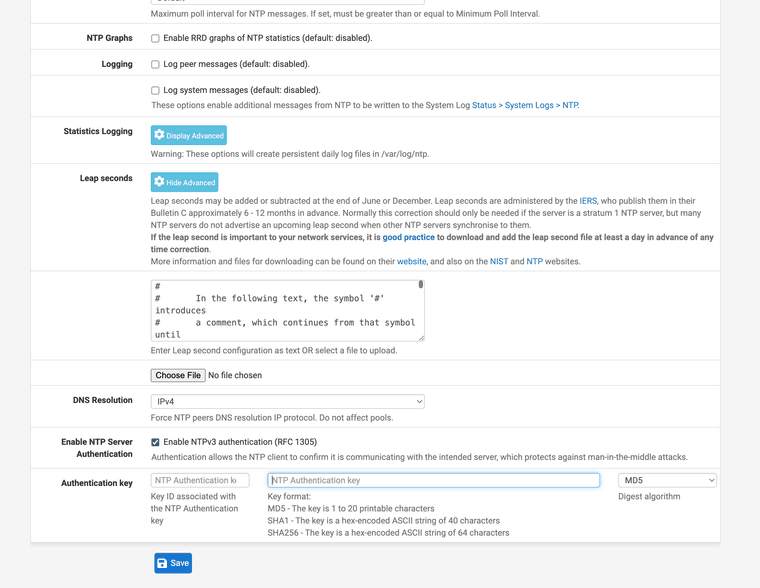
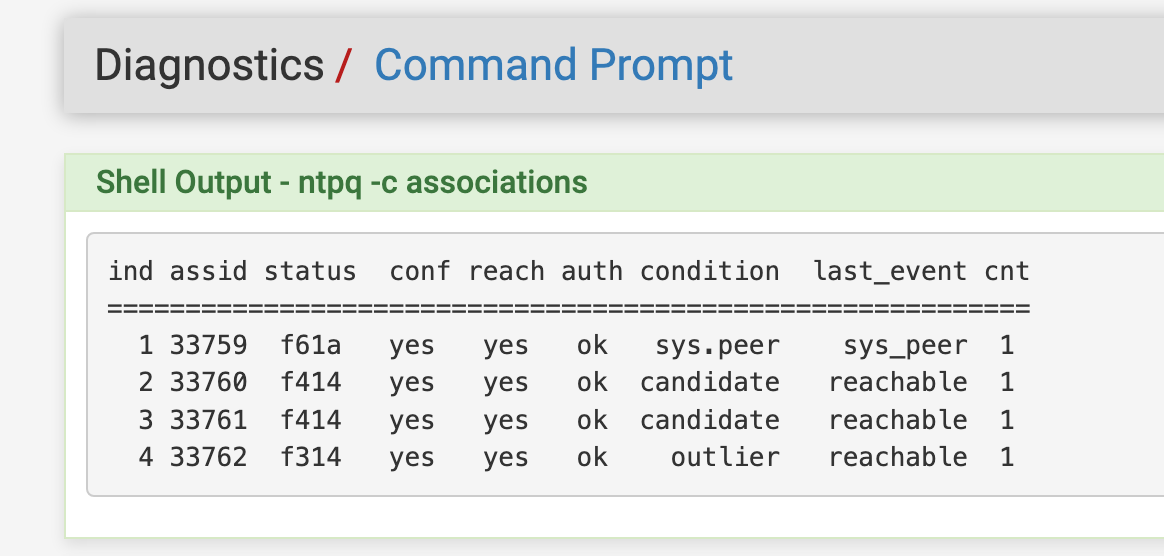
Time is showing AUTH under ntpq -c associations
This is great !!
Functions with the status patch also for nist.gov authenticated NTP project.
I had to originally get approved by NIST to even be able to use authenicated NTP with them.
This is an amazing addition to pfSense for time protection from the aging non autheniticated NTP protocol.
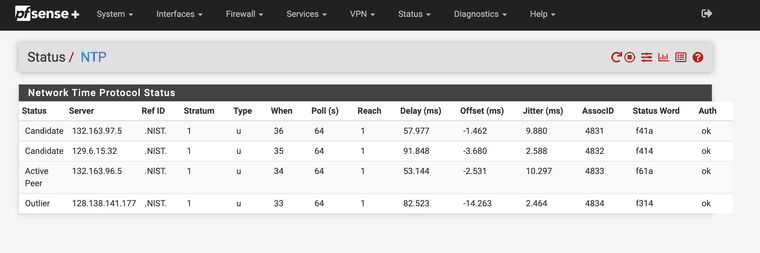
-
Ah I had been using Path Strip Count = 1 when I was testing. It probably makes more sense to just edit the patch file.
Here they are corrected (it won't let me edit the previous post):
system.inc.patch
status_ntpd.php.patch
services_ntpd.php.patch -
@MatthewA1 After so many posts in the forum you can edit old posts I think it has been a while for me.
-
i was fully onboard until i realized access requires the requestor to furnish the following:
- Name and postal street address of the organization or individual
- Name and contact information for the system operator and an alternate name if possible. These should include the e-mail addresses and the preferred contact method.
- Network IP address of the client system that will be used to query the NIST server. A network name is desirable but not required, since the system will authenticate the request using IP addresses only. Users may request up to 4 contiguous IP addresses that will share the same key.
you can't claim tinfoil hat and then furnish a full government and USPS street address to the Feds!
all seriousness though, these patches could easily be modified to configure a private authenticated NTP provider. good stuff, OP. i agree they should be added to base install.
-
@cyberconsultants The patches are not specific to NIST's authenticated NTP service, as NIST just implements authentication per the NTP RFCs. In fact, I tested these with my own NTP server which sources time from GPS and provides authenticated NTP service. The difference is, if you control your own NTP server, you can get by with only using key ID 1 (currently hard coded in the pfSense source) whereas using NIST's (or likely anyone's) public service, you have to be able to set a different key ID.
Side note: For anyone who doesn't want to go to the trouble of sending a letter or finding a fax machine, unlike what the NIST website says, they now do the key process all via email (and their file transfer site).
-
@cyberconsultants I can tell you projects that seek to improve aging protocols (NTP) take time (no pun intended) and trusted testers. I personally had issues with NTP getting hacked and having 10-15 jumps durring college tests without use of authentication (checked with analog gear clocks). I have not had that issue once it was moved to NIST authenticated time. It's a great project that seeks to fix issues like this. So far I have not had issues with use of these services. Again I was taking cyber security tests so I would expect the class wanted to drip students toes into some of the major issues, and gage how they resolved it. For me I flat moved to authenticated time. I trust it, it works it's secure. They even renewed my keys for me. Thank you NIST. I have not had time jumps now and I pray it stays that way.
From a university network perspective, the use of authenticated NTP with NIST is an improvement over the non authenticated version. Deployment of it requires it be tested, and a GUI that is easily accessible. Again the key should be hidden from prying eyes
 . It's that important. Make a new username hide the key from everyone that access the firewall important.
. It's that important. Make a new username hide the key from everyone that access the firewall important.With that thought

@stephenw10 can NTP options be specifically assigned in user manager and be blocked for others? With reflections on this GUI patch I just tested maybe it is also a good time to check with you. I do not think many admin have had the ability to use it without custom patches. Maybe the user manager does not list it yet.
@MatthewA1 maybe your GUI option should also be included in a user manager feature.
You know that song

 one thing leads to another...
one thing leads to another... -
https://redmine.pfsense.org/issues/15073
I just submitted a feature request for new user NTP keys privileges profile to be added. It should specifically list NTP keys so super admin can hide them from settings.