WiFi STA as Gateway - need to SSH into pfSense from Gateway
-
I have a WiFi station router connected to hotspot acting as a pfSense gateway which receives an IP from router.
pfSense WAN Interface 192.168.8.5 <-> WiFi Router 192.168.8.1
pfSense LAN Interface 10.0.1.1 <-> Switches and APThis works fine for using internet but when I'm ssh logged into 192.168.1.1 I cannot reach pfSense. Any suggestions?
Edit: Corrected typo in IP
-
pfSense WAN Interface 192.18.8.5 <-> WiFi Router 192.168.8.1
This doesn't make much sense..
What is the IP on pfsense that is connected to your wifi router?
So pfsense gets a wan IP of 192.168.8.5 I take it, typo?
Pfsense wan rules would block all unsolicited traffic inbound to it.. And there would be the block rfc1918 rule as well.
If you want to ssh from 192.168.8.1 to 192.168.8.5 (pfsense wan IP).. You would need to disable the rfc1918 block rule, and allow for ssh to pfsense WAN Address.. From where you want to allow it from.
-
@johnpoz Yeah it's not conventional. pfSense shows the gateway as 192.168.8.1 and the pfSense interface (opt2) is 192.168.8.5.
On the opt2 firewall rules, the first one is allow all for testing.
This is only used as a Tier 5 gateway when the other Tier goes down. But I'd like to be able to get into the gateway router via relay or reverse tunnel then get to pfSense. First I need to determine why I can't get from the opt2 router (192.168.8.1) to pfSense.
-
Not that, that didn't make sense.. Its the 192.18, and 192.168 address that didn't make any sense. I take it that was just a simple typo.
First I need to determine why I can't get from the opt2 router (192.168.8.1) to pfSense.
Already told you why you would not be able to get to a WAN connection on pfsense. Even if not the rfc1918 block rules. Any new interface that is added to pfsense would have ZERO rules on it.. What are you rules on this interface 192.168.8.5?
-
@johnpoz There's only one rule on this interface allow all.
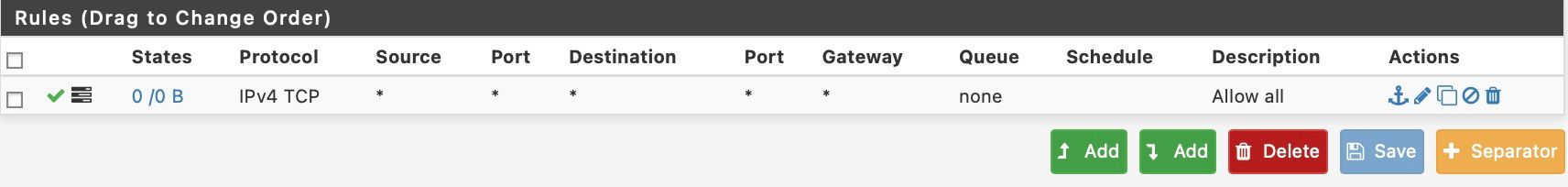
-
Well that is a horrible rule.. For a wan type interface.
But you can see there is no hits on that rule its got 0/0 - so be it you think your hitting pfsense? The rule says otherwise.
Do you have any rules in floating that would block access?
Look on this wifi router your trying to ssh from.. Do you see pfsense IP in the arp table? Not going to be able to hit 192.168.8.5 from 192.168.8.1 if there is no arp in the arp table.
-
@johnpoz It's CG-NAT on this WAN-type interface, but you're right. It's horrible rule that won't stay once there's traffic. I know I'm not hitting pfSense which is the reason for my post. I can get out fine. If I curl --interface opt2 https://icanhazip.com it returns the gateway further upstream.
This is my arp -a result:
10.224.0.1 0x1 0x2 f4:3e:9d:03:64:bc * wlan-sta 192.168.8.5 0x1 0x2 00:eb:cb:40:01:93 * br-lan 8.8.4.4 0x1 0x0 00:00:00:00:00:00 * wlan-sta -
Here is the thing - does your rule show other than 0/0 now.. If not its not being evaluated.
Sniff that interface on pfsense while your trying to ssh to that pfsense IP.. If you don't see anything then wherever your trying to connect from is not getting to pfsense interface