Comcast IPv6 works for 1-2 days, then stops routing
-
@jknott How do you block inter-VLAN traffic in your setup? With IPv4, you can just block RFC1918 addresses, but for IPv6, they're public, and since (for Comcast) they are subject to change, I've had to create rules to block access to every other VLAN I don't want each VLAN to have access to, i.e. reject traffic to "LAN net".
-
You have to specifically allow routing between VLANs. So, just create rules to pass what you want.
-
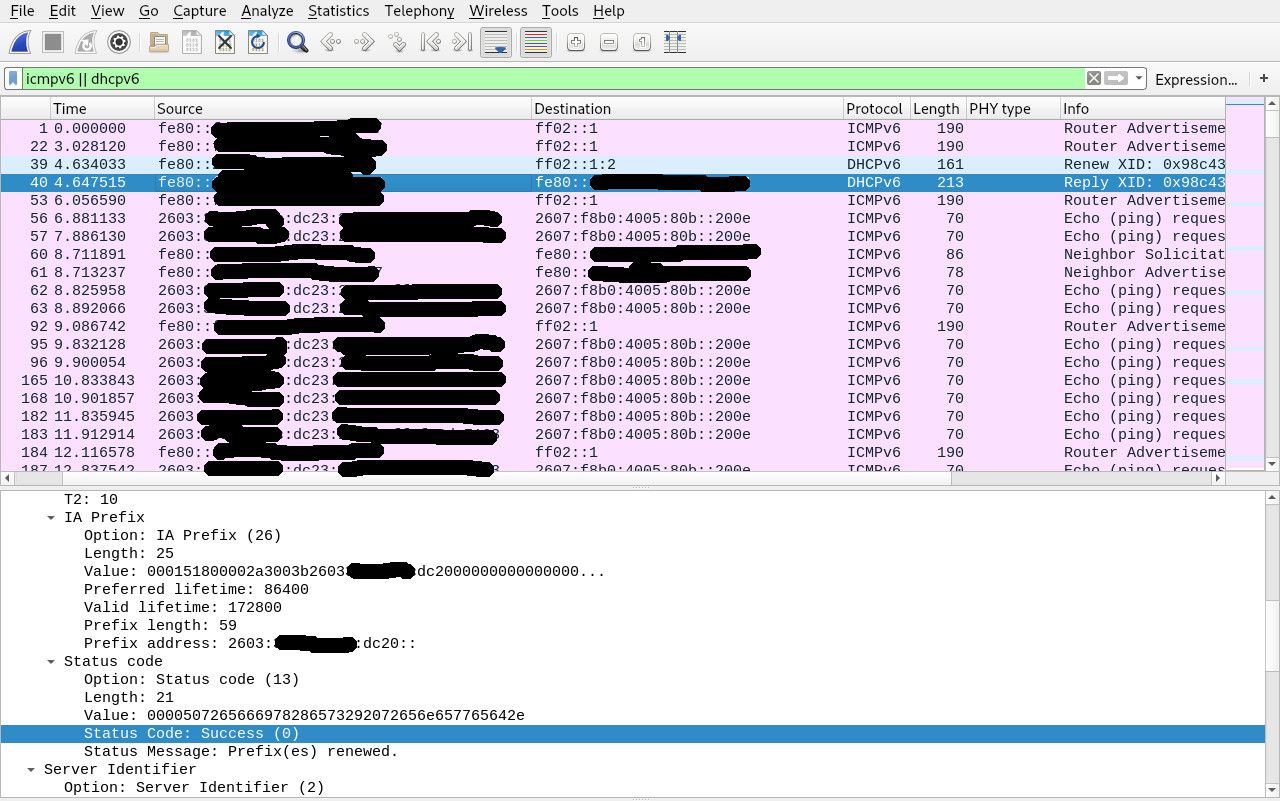
@jknott I don't think that works. Specifically allowing routing you want means rejecting traffic by default (when it reaches the end of your chain of rules). But if you're rejecting anything unknown, then you have no internet access, since "local" IPv6 addresses are public ones and there's no way to distinguish those from internet addresses. If Comcast changes my address block by giving my router a new block via DHCPv6-PD, then my old addresses then become external internet addresses and should be routable from any VLAN that has access to the internet.
-
Here's an example. This is for my test LAN, but would be exactly the same on a VLAN.
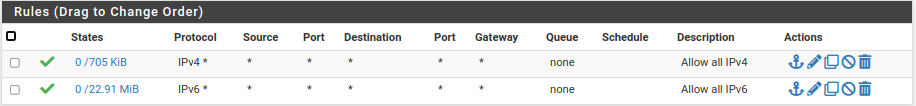
I had to create both those rules to allow IPv4 & IPv6 from my test LAN to anywhere else. If I hadn't created those, I wouldn't be able to reach anything beyond the test LAN.
-
@jknott Yep but if you have a rule like that, you have to specifically block everything you don't want to allow above it, right? Like routing between that VLAN and another VLAN.
-
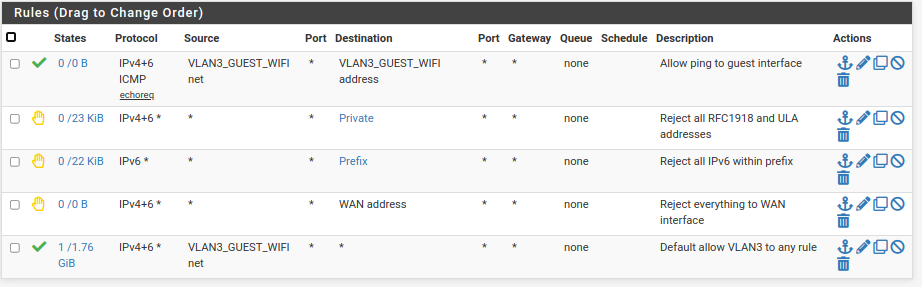
You allow only what you want to. In this case, I didn't want to block anything. On the other hand, my guest WiFi VLAN is configured to allow only pinging the interface or going out to the Internet.