DONT NAT on Destination network
-
I have my firewall behind a router that has a couple of VPN connections to it. From LAN of my firewall I need to connect to these VPN connections. I am looking for a way to NOT NAT when I am going to these networks. I dont see an option on the NAT rules that disables it.
Where / how can I create a NAT rule that says if destination network is X then dont NAT? -
I would try something like this: (Not sure if this is going to work).
1 - create an alias with the destination networks that are behind the VPN.
2 - Go to:
Firewall / NAT / Outbound
3 - Click in ADD
4 - Tick the option 'Do not NAT'
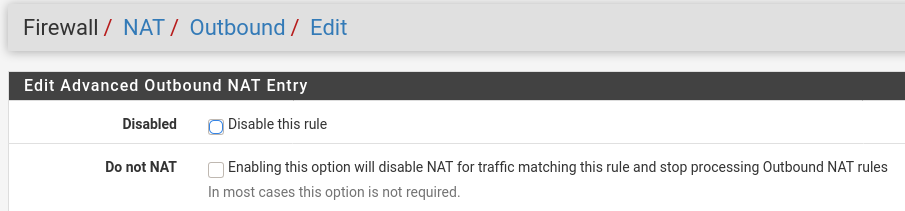
5 - Fill the remaining options (destination would be the alias created in the 1st step)And make sure this NAT is above the NAT used for internet access.
Edit: You will probably need to create a static route in the router pointing to pfsense as the next hop for the networks that are behind pfsense.
Edit2: Actually, you don't need a NAT from pfsense to the router at all, you would only need the static routes, and disable the WAN NAT for LAN network.
-
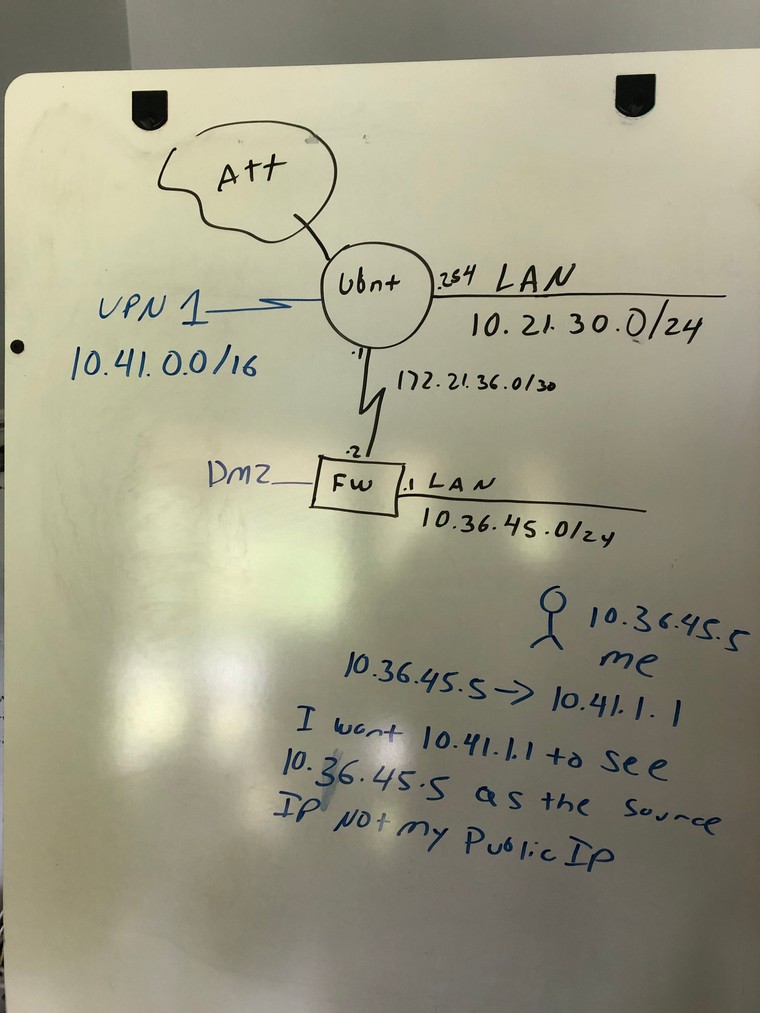
huh? What is the transit network between your router and your firewall?
How would your upstream router know about these downstream networks if you do not nat to your firewall(pfsense) connection to the transit network?
I assume this is what your doing because you say your natting, and want to turn it off for something specific.
Could you draw up your network, and what is trying to go to what without natting, etc.
-
-
How would 10.41.1.1 ever see your public IP as source? Other than the IP to create the vpn tunnel. Traffic inside the tunnel would look likes its coming from whatever pfsense gets for its tunnel IP after creating the vpn.
For you to use your downstream network like that - would have to be setup. the network on the other side of the vpn would have to know to route traffic down the tunnel to get to your 10.36.45 network..
So your natting on pfsense to this 172.21.36.2 address now? If you don't you have the ubnt setup to route this traffic via your transit?