Has my SG-1100 been pwned?
-
Coming back home from a long-weekend trip to parts with very poor internet connectivity I discovered that I couldn’t log into my SG-1100:
 
Immediately after a power-cycle I was again unable to log in. Seven hours later, my login credentials work. My password possesses similar data entropy as this one: !d2MnYm4tptqj!E. 1Password considers that “excellent.” It would rule out a brute-force attack.
Also, my ability to log into my Linksys Velop system (in bridge mode) is intermittent. Immediately after my return, I was unable to authenticate for connection to the WiFi network using my established password. A couple of hours ago it worked. Now it again is failing.
What should I do. I have very limited cybersecurity experience and no forensic skills. I was going to reset the SG-1100 to factory settings and import the last known good settings file. Would I have to reinstall the firmware image from scratch, too?
-
Have you reviewed the logs to see if there was a login while you were away?
-
@amarcino: Well, the authentication logs show this:
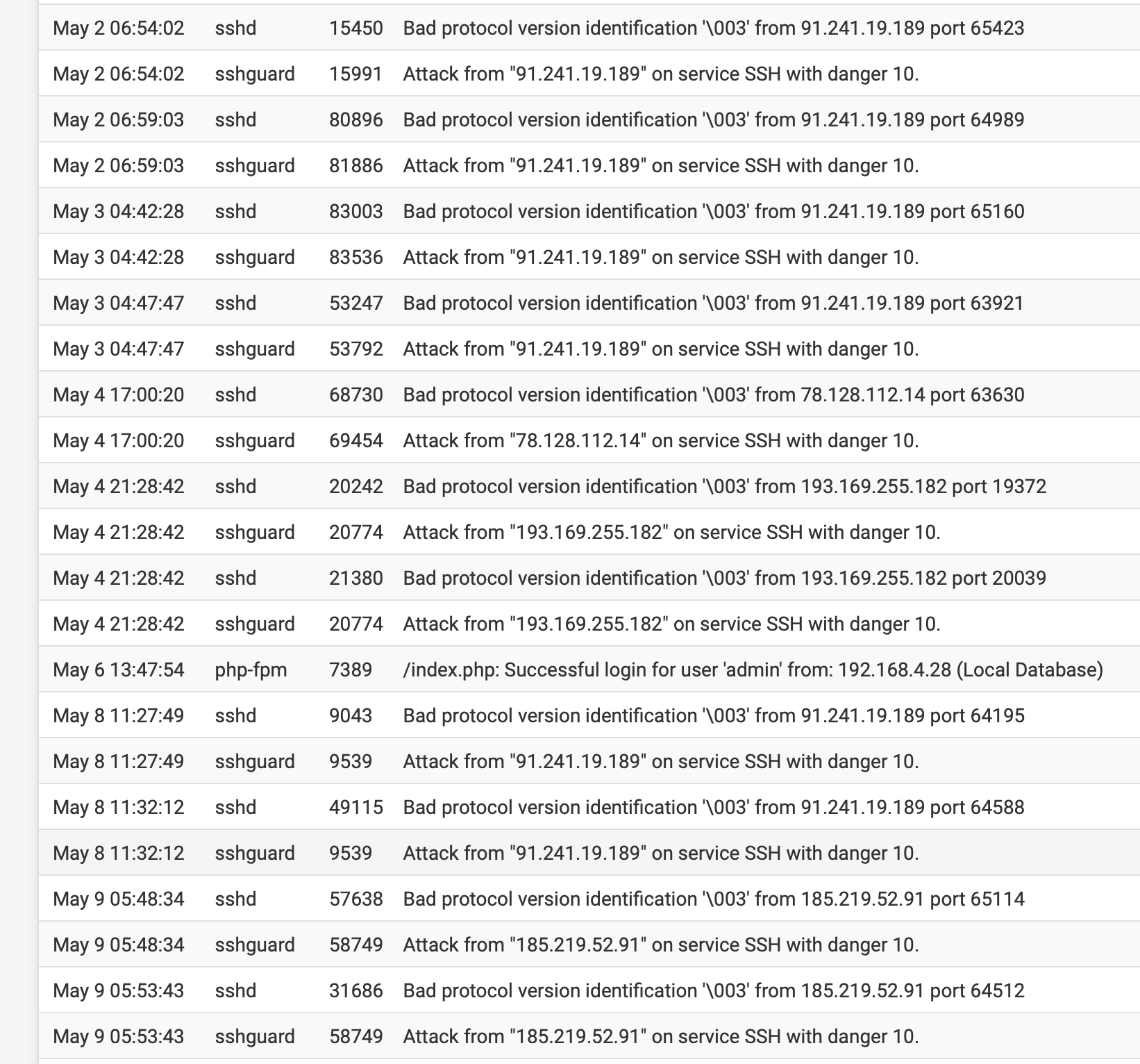
Not sure, how truly scary this is. Password-ssh is disabled.
-
@dominikhoffmann
Are you allowing SSH access to your device remotely (across the Wan)? -
@amarcino: Yes, I do. Through a password-protected private-public key pair, only.
-
Well then you are going to have people/bots or whatever banging away at it.
You could create a firewall rule to block those IP's. You will have to create a list and use that named list in the rule. It is going to get very big though.
Have you looked any of them up?
p.s. I have this turned off on mine, because I don't want to deal with the garbage. If I am away from home, and some fault in my network occurs, I just deal with it when I get back through console access.
You have to weigh for yourself the balance of convenience and security. If is something you really must have, I would suggest changing the port for ssh access. That might slow them down a bit.
-
FWIW - You may want to enable OpenVPN for remote management and then only enable it as needed. Any open port will get bot-scanned.
-
@provels, @amarcino: I am aware of that and am letting the built-in defenses take care of it.
At this point I am mostly interested in learning about the cause for what I saw this morning. Could it have been so overwhelming that the GUI on the LAN side was unable to authenticate because of that, rather than a maliciously changed password?
-
@amarcino said in Has my SG-1100 been pwned?:
I would suggest changing the port for ssh access. That might slow them down a bit.
Again FWIW, I tried running my OpenVPN on a random high port and found I could not access it from some locations. Likely ISP blocked. That's why I switched back to 1194 (and 443).
-
-
@dominikhoffmann I very much doubt you were hacked. If you were, they're certainly the most helpful hacker group in the way they put your old password back.
There is more likely a benign reason for what you saw. I would never open ssh to the world. Either put it behind OpenVPN or modify your NAT rule so that it only passes traffic from a known source location, like your home or office desktop.
Don't worry about bots & scanners. Just let your defenses do their thing and ignore the log spam.
-
@dominikhoffmann exposing SSH to the Internet and not terminating it correctly is a no no. Change default Port and disabling Password Logins is recommended. Use Public Keys instead but I highly recommend using OpenVPN for remote management. Don't expose SSH without configuring it properly
-
Yup. Use a VPN if you have to open it to any source address.
-
@violetdragon
Hi, what would "terminating it correctly" mean in this context? -
@dominikhoffmann said in Has my SG-1100 been pwned?:
I discovered that I couldn’t log into my SG-1100:
In that case - do nothing - and switch over right away to the second access :
That could be the SSH access (has to be setup up before) - or the console, which always works.
The menu shows up ?
Use option 11 - (restart the GUI part).@dominikhoffmann said in Has my SG-1100 been pwned?:
Now it again is failing.
Time to regain access and do what admin always do :
By looking at the dashboard you'll learn nothing. The dashboard is there for the times when all is ok.
Look at the - all the - logs.
You should always be looking at the logs. Eventually, you'll know what messages are normal.
The day things go south, you'll know what messages are new, and you know what happened.@dominikhoffmann said in Has my SG-1100 been pwned?:
rather than a maliciously changed password?
They would have to use the certificate to gain access, first.
Just ise the classic 1234 password for GUI access.
Lock down the GUI access to a trusted LAN - do not let non trusted devices access this LAN, and use a OpenVPN access if you need to do some remote admmining of pfSense. See the Youtube => Netgate => OpenVPN vdeos (even the old ones).