DNS Resolver not sure how to call it but to me just broken.
-
Doesn't properly resolve dns:
- DNSSEC fails, yes the domain is valid, not sure what it does but it does not work well with multiview DNS. Partially resolves different views.
- Does not work well with multiple DNS zone views, for some reason it manages to resolve the wrong view even when the source is properly defined.
- When it works only a partial resolve has happend either it doesn't know the AAAA record or it doesn't know the A record. This doesn't matter that much for dual stack clients but it does matter a lot for IPv4 only clients.
- The fact it resolves wrong in multi view is because either the routing is not respected or the source interface isn't respected not sure which is worse, both resulting in resolving the wrong IP
- Maybe it doesn't respect the fact that forwarding is enabled.
Doesn't matter how you look at it it doesn't do what it is supposed to do.
-
Going through the unbound configuration file, I figured out what was causing these weird DNS results. Maybe make a reference on the DNS resolver page, .. why would you even filter internal resolved IP. Assuming you've got an internal network this is a common thing.
This seems a strange feature especially if the domains have DNSSEC, ..To be clear this is supposed to be on. (disabled)
Just spend 3 days figuring out what was causing this, the usefulness of this feature still boggles my mind. I can't think of any reason why you even would enable this by default. Other then wasting CPU, breaking DNS, .. I mean why, would anyone think this was a good idea !?
-
@ofloo said in DNS Resolver not sure how to call it but to me just broken.:
Doesn't properly resolve dns:
DNSSEC fails,
..... the fact that forwarding is enabled.
Start with the first fact : DNSSEC (checking) is useless, and should be turned of if the Resolver is not resolving, but forwarding.
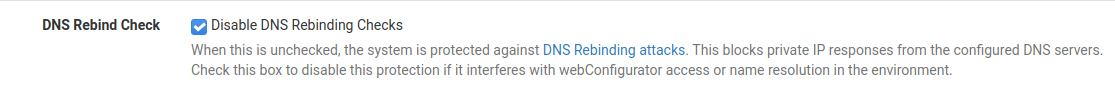
The rebind check :
It's unchecked by default.@ofloo said in DNS Resolver not sure how to call it but to me just broken.:
I can't think of any reason why you even would enable this by default.
"Do not change settings that are meaningless".
Some reasons why this option exist. -
@gertjan sorry but dns rebind check means that if a domain is resolved to an lets say 10.0.0.1 IP it says you know what that can't be right lets not return it !?
It is to prevent that some hacker redirects you're dns session to some other site. To me useless inside a LAN.
Basically what it boils down to you know someone is going to search for google.com lets just reply the a record for google.com before they query it or at least before the authorized nameserver can respond. And make it seem like it is responding.
If you have no servers what so ever or if they all have a routeable IP then this might seem like a good idea.
Or turn on PureNAT so it reflects back. Then maybe.
Otherwise a big fat NO.
How would you determine if it isn't supposed to return a non-routable IP
-
@ofloo said in DNS Resolver not sure how to call it but to me just broken.:
sorry but dns rebind check means
I know what DNS rebind attack is ;)
This is my option : it's an anti shoot in the foot option.
To mitigate against a somewhat broken DNS situation (?).