Kill switch
-
Hello, i need some help understanding why my setup for kill switch is not working.
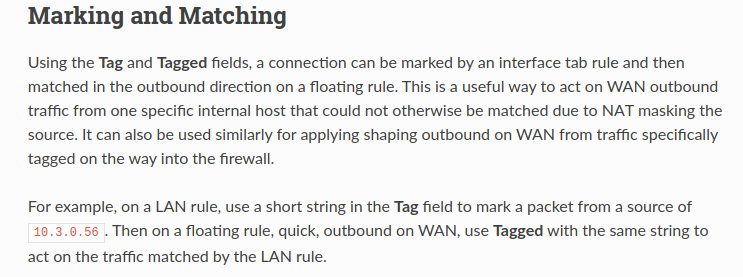
All the resources i found are talking about creating a floating rule with tag.
One station i need to use always my wg connection.
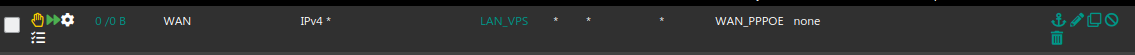
I made a lan rule only with that ip , i select the Wg gateway and i Tag packets.
Also i made a floating rule rejecting connection to Wan based on the tag, but for some reason if my wireguard go down after few seconds i will get out using my wan gateway.
Lan

Floating
Thank you. -
Try like this:
LAN:
1st rule: allow VPS to any - VPN gateway
2nd rule: allow VPN to any - WAN_PPPOE or default if this is the default gateway - tag noegressFloating rule:
Reject: Interface WAN_PPPOE - Quick - Direction out - tagged noegress -
@mcury said in Kill switch:
Try like this:
LAN:
1st rule: allow VPS to any - VPN gateway
2nd rule: allow VPN to any - WAN_PPPOE or default if this is the default gateway - tag noegressFloating rule:
Reject: Interface WAN_PPPOE - Quick - Direction out - tagged noegressThank you for your answer, but i found the problem in the next 5 min after i made the post.
On the Lan rule i set Tag and should be Tagged and on the floating i set Tagged and should be Tag. -
@lcbbcl said in Kill switch:
On the Lan rule i set Tag and should be Tagged and on the floating i set Tagged and should be Tag.
You are welcome, but strange, you should tag it, then use the 'tagged' to match..
-
@mcury You are right i it didn't work, i was blocking that station to wan and wg also..now i am at the same position
-
I did it with a Lan rule to reject all connections for that station with the wan gateway.
For some reason using tag is not working. -
I did it with a Lan rule to reject all connections for that station with the wan gateway.
Yes, this would accomplish the same goal.
For some reason using tag is not working.
You actually don't need to use tag.. Just make sure you are allowing the VPS group to have access to internal resources in case you need, and insert this rule above the reject rule.