Plex not working outside the network
-
Exactly - I have another test, that home that just pings my IP to see if my internet is up. But the tcp test tells me if plex went down, but my internet is still up.
More often than not its actual internet that goes down - but plex now and then does hang or crash, etc.
Or maybe I dicked with the rules and messed up remote access to plex, etc. Its great to have both tests internet, and then specific service.
-
That is useful to me as well, here where I live the Internet goes down everyday.. I'm not sure if its cabling here inside the building or if it's the ISP itself, I don't hear other users complaining so much as I do..
More often than not its actual internet that goes down - but plex now and then does hang or crash, etc.
A very fast troubleshooting that you could do through your phone
Or maybe I dicked with the rules and messed up remote access to plex, etc. Its great to have both tests internet, and then specific service.
Who never did it? :)
-
@mcury said in Plex not working outside the network:
Who never did it? :)
Exactly ;) hehehe - so its good to know very quickly if plex is no longer available when you might be playing with rules, etc.
And yeah you can see pretty easy right on your phone if total internet is down, or just something wrong with plex.. Great service - and very usable even at the free level.
-
@johnpoz Is it OK to just NAT stuff out? I have had my share of opening ports. Unless you are using another obvious anti scan tool, snort, etc, you'll get traffic from anywhere straight to your NAS for it to handle, how do you secure that?
Instead of doing that I just VPN in.
-
Plex is pretty secure on its own.. You have to auth through their service, and you can now enable 2fa if you want.
I limit who can hit my open ports using pfblocker, only US ips - I at one time had the users give me their public IPs. But this was just to difficult for typical users ;)
And they change, and then they can't access from their phones while on cell data, etc. And some of them travel about, my one buddy spends time down in FL for example at different Air BnBs - yeah he is crazy during covid.. But he still wants to access my plex ;)
Part of the reason I put mine on a different port then 32400 on external - was to be able to see how many scans just to 32400.. I don't see any in the last 24 hours, 2000 log entries..
Yes if it was just you - by all means vpn in to your network vs exposure - agree 100%.. But then I have family that just has shit isp wifi router, and their tv is connected to the wifi.. How am I going to get them to setup a vpn to my pfsense.. I sure and the F am not going to spend the time, effort and most likely my own money to do that..
If your concern - then don't expose.. I am not that concerned. And I want to be able to share with my friends and family - and relay (outbound only is too slow 1 or 2mbps limit if your plex pass - I am), and locking to their ips while that would be next best option to vpn is too much work.. With all things related to security it always comes down to level of security vs ease of use..
Same goes for my request system, while this also requires login. I limit these standard port 443 to US ips. This is where my users are, and also behind a reverse proxy, and if you don't send the correct headers for the actual fqdn - you don't get connected. So this prevents random scans just scanning to an IP on 443. You can setup this restriction in haproxy.
example here is from external to my wan IP where 443 is sent to my ombi and overseerr request systems based on the fqdn used in the headers. If you don't have a valid name - you don't get past the reverse proxy
My biggest concern really is my plex users have shit plex passwords ;) And their account could get compromised. But I log all IPs, and get notifications of new IPs that connected (tautulli can do this). If I see some odd out of area for where that friend is, I contact them and ask, etc..
example
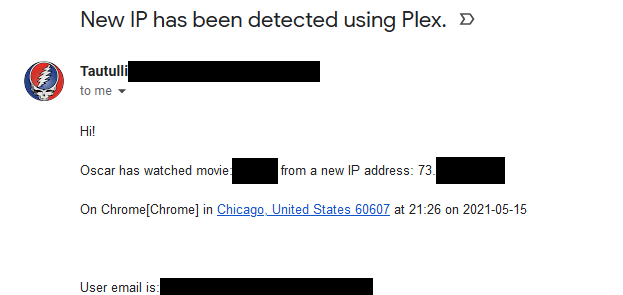
One of my friends came from a new IP.. Geo location is correct for him - He is in Chicago, and that IP is owned by comcast, his ISP.. So most likely his IP just changed.. No real reason to dig into that any further.. But if was not his isp, and was not somewhere in the area where I know he lives I would reach out to him, hey were using plex at that time watching this movie, etc.
This also keeps them from sharing their accounts with their friends ;) heheh That very well could be some friend of his, that he shared his account with. But I know him quite well, if I didn't he wouldn't have access to my plex. And he knows better to share his account, etc.
Yes security requires vigilance.
-
@johnpoz Excellent answer, thanks!
-
I just looked - and I do have 2 hits to 32400.. I had just looked yesterday is why I said nothing in last 24 hours.. But got me curious to see if anything current.
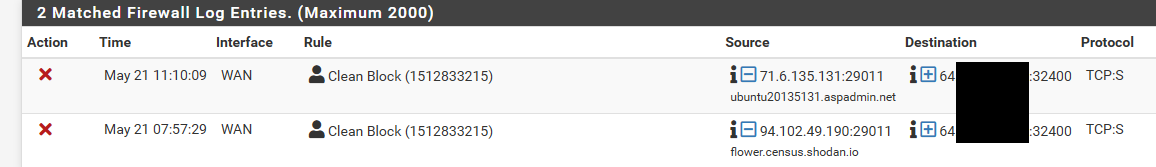
That shodan one is most likely ok - just a tool looking to see how many have that port open, etc. for their info base you can look at, etc.
Running on different port or obscurity does not equal security - but it does allow me to easier look into logs to what is going on vs trying to weed out all the possible legit IPs of my remote users from what is bad traffic.
Odd that same exact source port, I would think the ips are related in some way, and its the same tool doing the scanning.
I watch my logs more than most I would "bet" ;) and I don't see much traffic to 32400 to be honest.. I see shit ton to ssh, telnet, 80, etc.. sql port - the commons ones. I would think 32400 would be more popular - but if no real exploits available for it - its not very valuable spending time finding IPs running it. I do watch security forums and read the CVEs and lots of security sites - I don't recall running across any sort of serious concerns with plex exploits, etc.
-
@johnpoz Did you enable the spectre/meltdown protection in the Synology?
I wonder if that is important if we leave the port 32400 opened..
I don't want a performance hit.. I'm using the DS218+This setting is found in Control Panel > Security > Advanced, at the bottom.

-
No I do not have that enabled - it does not come into play unless you are running some sort of untrusted apps or have other users accessing that can run stuff.
Its going to be a performance hit - when there is pretty much zero way that could be exploited. It really only comes into play with multi tenet sort of hosts, where you have multiple users running apps..
-
Great, thanks :)