Traffic Won't Route Through Outgoing VPN
-
@crackerjackshot said in Traffic Won't Route Through Outgoing VPN:
That IP is the address of the DMZ VPN connection, that is why it's different than the internal VPN connection IP. As I said in earlier parts of this thread I have all of the DNS piped out just the one DMZ connection.
Well, but the outgoing interface the log is showing is "OUTGOINGEXPRESSVPNINT" which seems to me not being the DMZ interface as there is an other one you called "OUTGOINGEXPRESSVPNDMZ".
-
@viragomann Yeah that's interesting. I see what you're saying.
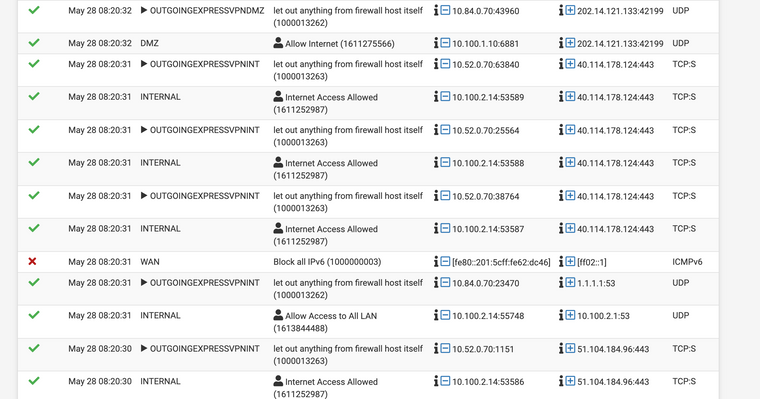
This log shows it more. All the internal traffic going out 443 displays the OUTGOINGEXPRESSVPNINT and it has the correct address. But the DNS traffic shows the same interface but then goes out the DMZ address. Up top theres a piece of traffic that shows the DMZ contacting the internet and it correctly shows it as OUTGOINGEXPRESSVPNDMZ.
Not sure what that's about
-
@crackerjackshot
So what is initiating these DNS requests?
I assume the DNS resolver on pfSense itself. If so is there any reason for using only the DMZ-VPN interface?
Check the resolvers outgoing interfaces and correct them if you want.Then configure your outbound NAT accordingly.
If it's the resolver and it should be able to go out on the INT-VPN add a rule to this interface for the source 127.0.0.0/8, if desired restrict it only for TCP/UDP 53. -
@viragomann You can see the DNS request just below the one going out the VPN pipe to the 1.1.1.1. It was originated on a machine in the internal net that has the 10.100.2.14 IP right now. Everything is set to query the .1 address in the subnet and then as far as my understanding goes the resolver takes care of it after that. Why it is saying the INT VPN interface is beyond me unless the traffic is getting passed there first but I wouldn't think so. The only reason I was doing it that was was to add more obscurity of the traffic on the server side. Getting connections to from a 443 that doesn't match the location of the DNS requests.