Internally resolving hosted services over Reserve Proxy
-
Dear Community
I have encountered the following problem with my configuration and need your valued help.
Initial situation:
- pfSense with PPPoE WAN connection and one static Public IP address
- DNS resolver enabled
- No standalone internal DNS server, pfSense manages the DNS requests
- Resolving external DNS queries works fine (google.com, yahoo.com etc.)
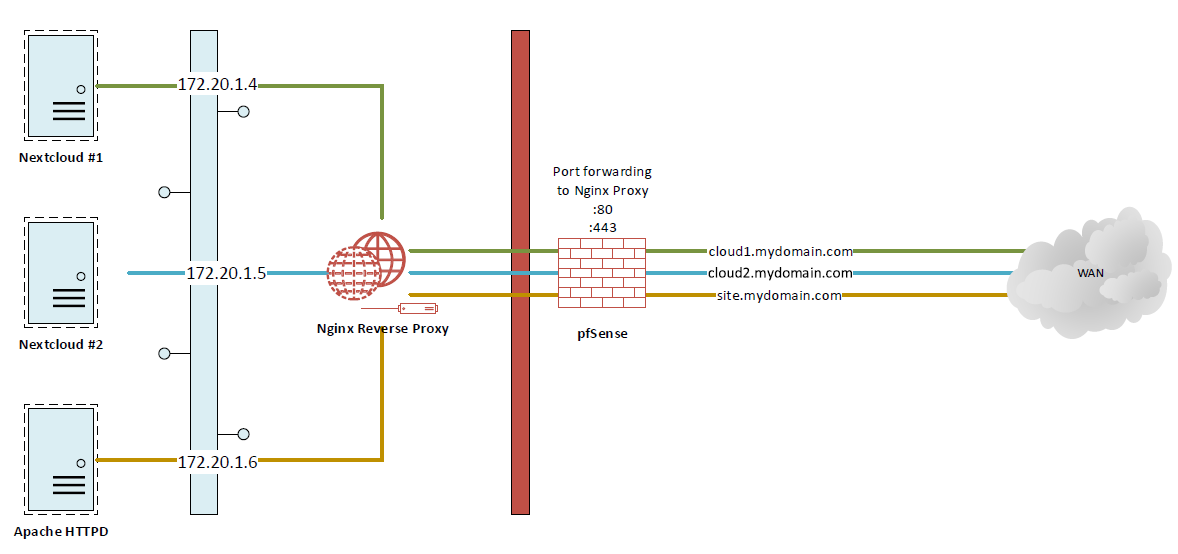
On the internal network, I am hosting two Nextcloud instances and one HTTPD Server (Lab) which are made available externally with the help of an Nginx reverse proxy. Both Nextcloud instances as well as the HTTPD Server work fine outside my LAN.
The problem now is that the resolution of the instances on the internal network do not work. So basically I want to be able to access cloud1.mydomain.com, cloud2.mydomain.com and site.mydomain.com internally, the request should of course also be processed by the Nginx reverse proxy and send back to the internal network.
My configuration looks like this:
Your help is greatly appreciated.
-
@latency0ms
Add host overrides for your hostnames to the DNS resolver settings and point them to the proxy. -
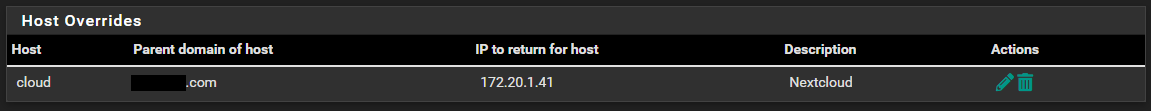
I followed your suggestion, here's what I did:
- 172.20.1.41 = Nginx Reverse Proxy
DNS Resolver - Host overrides:
nslookup:
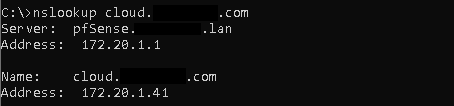
The nslookup query points to the correct IP address 172.20.1.41 > Nginx Reverse Proxy
Unfortunately this adjustment does not lead to success, as soon as I enter the URL in the browser of a local client, the connection ends in a timeout.
-
@latency0ms
Is the proxy in transparent mode? In this case, that won't work.If it's an option to bypass the proxy you can point the host overrides to the servers IPs directly.
If you want the internal traffic to pass a transparent reserve proxy you can try to enable NAT reflection instead of the host overrides.
-
@viragomann said in Internally resolving hosted services over Reserve Proxy:
@latency0ms
Is the proxy in transparent mode? In this case, that won't work.I am using Nginx Proxy Manager (NPM), and I am not entirely sure if it's in transparent mode
If it's an option to bypass the proxy you can point the host overrides to the servers IPs directly.
I think this is not an option since NPM is adding HTTPS to the session, I also need HTTPS on the internal host connection
If you want the internal traffic to pass a transparent reserve proxy you can try to enable NAT reflection instead of the host overrides.
What setting would you recommend for my scenario?
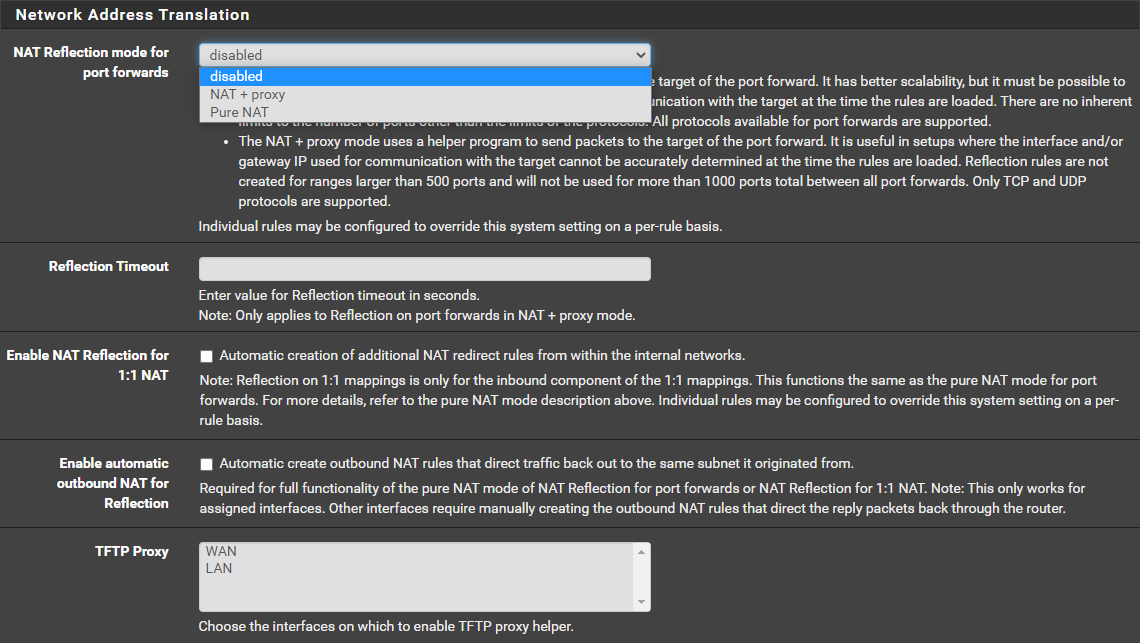
-
@latency0ms
In transparent mode you see the origin clients IP accessing the webserver, if not you see the proxys IP.You can also enable NAT reflection only in a single NAT rule (that one which forwards the web-traffic to the proxy) if you don't need it globally. The options are equal.
As I learned some time ago, the proxy mode is needed if client and server are connected on the same pfSense interface. When the traffic is passing pfSense, pure NAT mode is sufficient. But you may try it. -
@viragomann said in Internally resolving hosted services over Reserve Proxy:
@latency0ms
In transparent mode you see the origin clients IP accessing the webserver, if not you see the proxys IP.Then it's definitively transparent mode. Screenshot from Session-Log in the Webserver
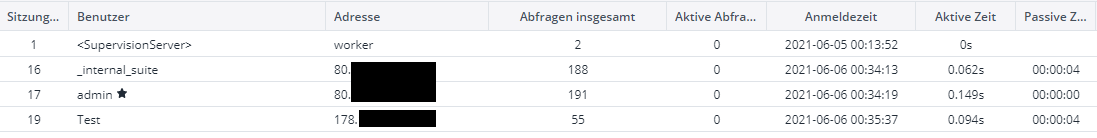
You can also enable NAT reflection only in a single NAT rule (that one which forwards the web-traffic to the proxy) if you don't need it globally. The options are equal.
Got that, I'll keep this as an option.
As I learned some time ago, the proxy mode is needed if client and server are connected on the same pfSense interface. When the traffic is passing pfSense, pure NAT mode is sufficient. But you may try it.
Ok, I will try this and report back the results.
Thank you for your support so far!
-
@latency0ms
Yes, if the proxy is in transparent mode, you run into asymmetric routing issues, cause the webserver is sending responses back directly to the client instead to the proxy. But the client thinks, he is talking to the proxy and hence won't accept the responses.Consider that you have to remove the DNS overrides when activating NAT reflection.
-
@viragomann said in Internally resolving hosted services over Reserve Proxy:
@latency0ms
Yes, if the proxy is in transparent mode, you run into asymmetric routing issues, cause the webserver is sending responses back directly to the client instead to the proxy. But the client thinks, he is talking to the proxy and hence won't accept the responses.This makes total sense, yes.
Consider that you have to remove the DNS overrides when activating NAT reflection.
They have been removed already, thanks for the hint.
Huge! It's working with NAT + proxy!
This is my config:
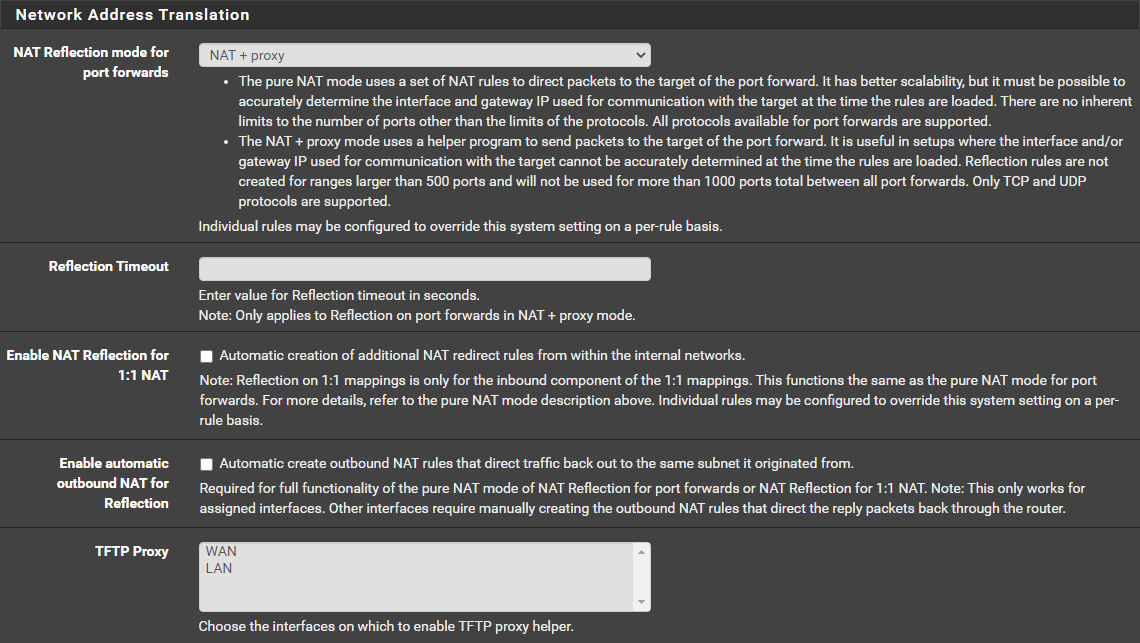
Kudos to you sir! Thank you!

-
@latency0ms
great.
-
This post is deleted!