Please help: VLAN and NAT port forward to Shadowsocks server behind pfsense (Netgate SG1100)
-
Hi everyone!
I need your help. Not a network professional here, so you might see, what I miss in my setup.I have my pfsense firewall (Netgate SG1100) with two VLANs (LAN and IOT).
Shadowsocks server is sitting on IOT vlan (will move it later to DMZ) listening on port 9999 (tcp and udp).
My workstation is on LAN vlan.nmap scan from pfsense shell to shadowsocks server (just tcp):
[21.05-RELEASE][user@pfSense.cipherpunk.lan]/home/user: nmap -p 9999 192.168.10.6 Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-21 20:17 EEST Nmap scan report for 192.168.10.6 Host is up (0.0057s latency). PORT STATE SERVICE 9999/tcp open abyssLooks good here.
nmap scan from my workstation (LAN vlan) to shadowsocks server (just tcp):
❯ nmap -p 9999 192.168.10.6 Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-24 18:46 EEST Nmap scan report for 192.168.10.6 Host is up (0.53s latency). PORT STATE SERVICE 9999/tcp filtered abyss Nmap done: 1 IP address (1 host up) scanned in 5.97 secondsAnd the same
filteredwhen I scan from outside while sharing 4G from my mobile (I have static ip for my domain name, using dynamic DNS service)The firewall rules on pfsense:
WAN interface (note NAT automaticly created rule to froward 8443 external interface to 9999 internal shadowsocks server):

LAN interface (where workstation is) - note the first rule allows ALL traffic (temporarily for troubleshooting only):
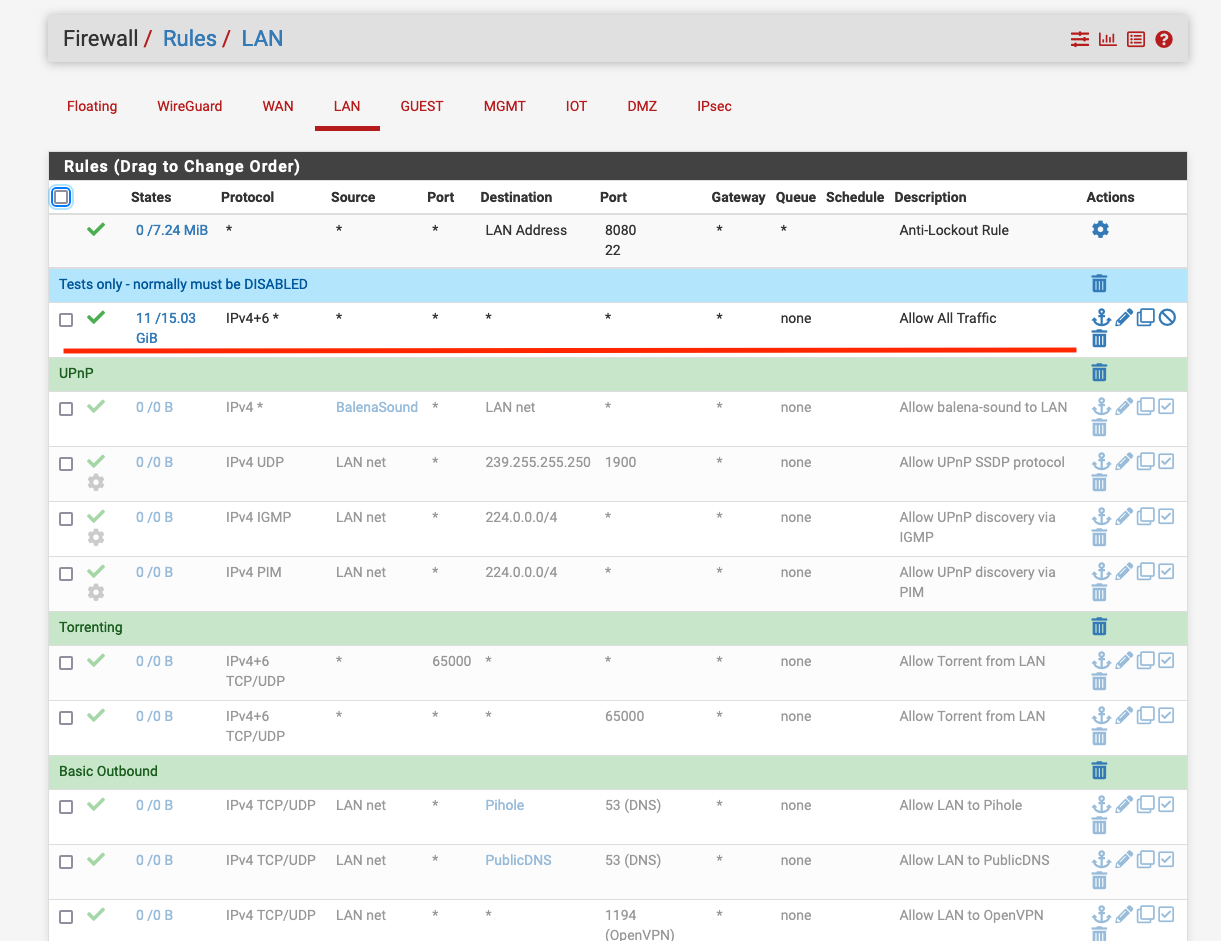
IOT interface (where the shadowsocks server is) - note the first rule allows ALL traffic (temporarily for troubleshooting only):

And here are my NAT rules:
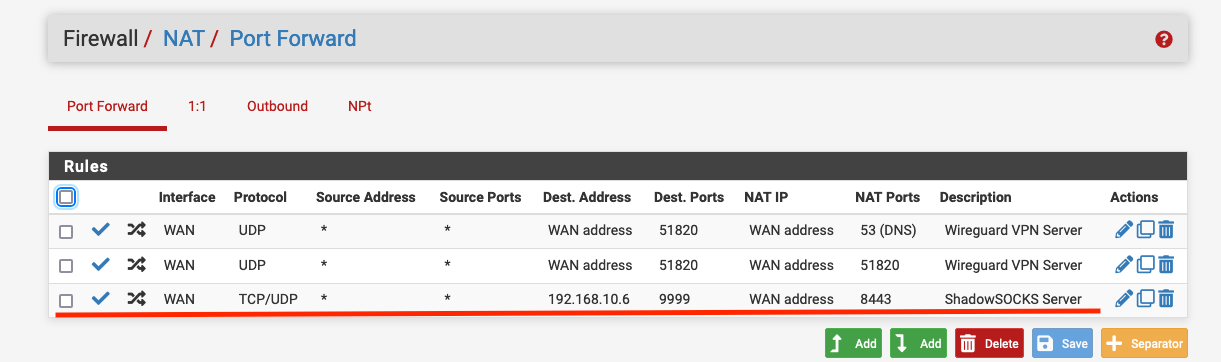
At this point I have no ideas what may be wrong in my setup.
Why this particular port forward does not work AND why I cannot even successfully nmap from one VLAN to another for this particular server 192.168.10.6 when all my rules on both interfaces basicaly allow ALL traffic (IPv4+6 all protocols).
At the same time my Pihole is sitting on the same IOT vlan and I can successfully nmap it's port 53 seeing it as
open. Please help me to troubleshoot this. Any help is appreciated. Thank you -
@drew-kun
Your NAT rule seem quite wrong.
The destination should be the WAN address (on WAN), while the target IP should be your internal address.
WAN address as NAT IP on WAN interface doesn't make any sense at all. -
@viragomann Thank you very much for your reply!
I know it may sound weird, but I actually use the following pfsense version: 21.05-RELEASE (arm64) built on Tue Jun 01 16:52:48 EDT 2021 FreeBSD 12.2-STABLEAnd I suspect that something was changed in this update, because the WAN firewall rules that are automatically generated look correct (please correct me). At the same time when I change the NAT rules as you suggest, the automatically generated WAN firewall rules changes the WAN port from 8443(WAN port which should be open and forwarded) to 9999 ("internal", shadowsocks server port, sitting behind firewall).
See screenshots:
NAT:

WAN Firewall rules:
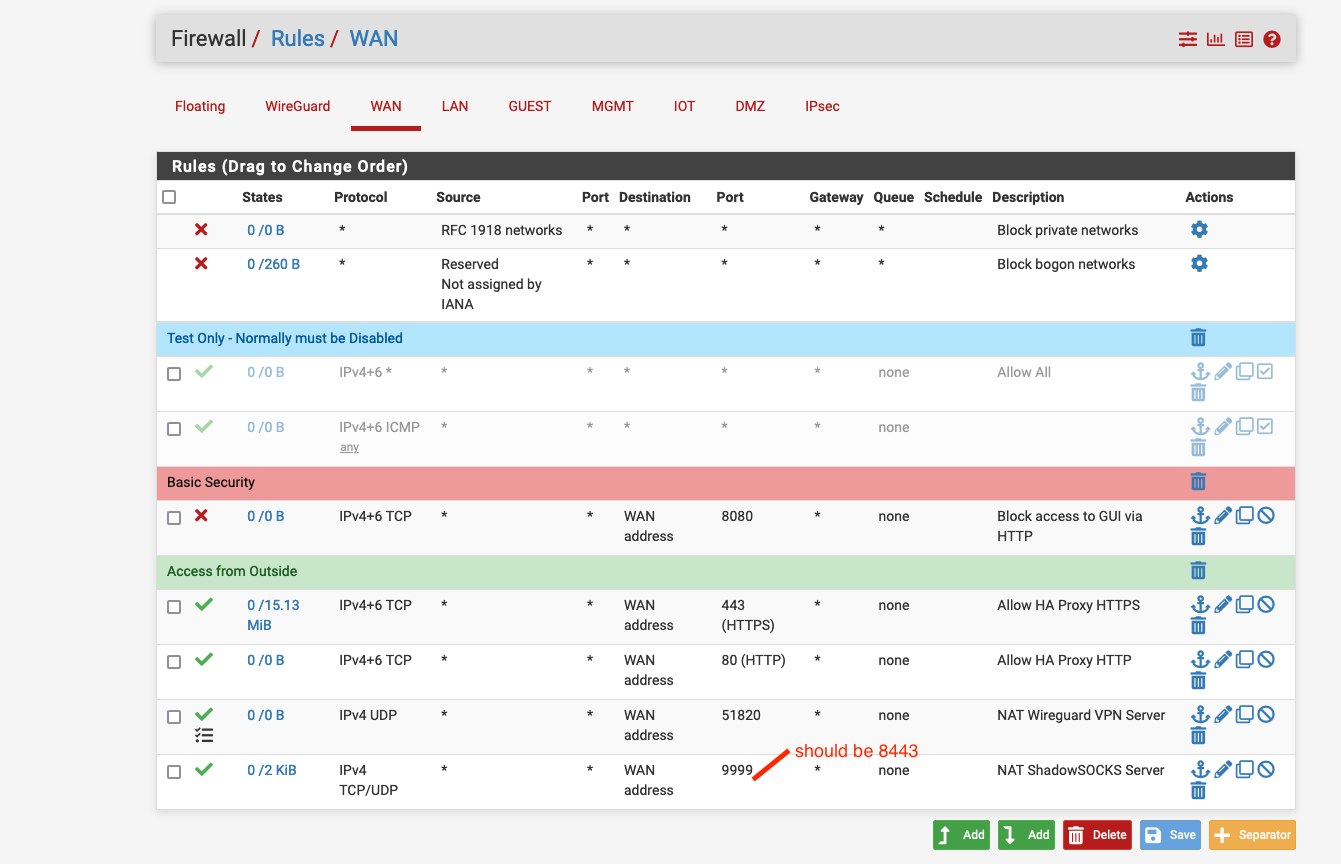
Thus either your suggestion is wrong, or the auto created WAN firewall rules are being generated improperly.
I am pretty sure you are right, and thus, could you please confirm that auto-generated rules use the ports wrong way around?
Thanks!
-
@drew-kun said in Please help: VLAN and NAT port forward to Shadowsocks server behind pfsense (Netgate SG1100):
I cannot even successfully nmap from one VLAN to another for this particular server 192.168.10.6 when all my rules on both interfaces basicaly allow ALL traffic (IPv4+6 all protocols)
Well if you can not get to it from another vlan.. Does the device even have a gateway set. Its quite possible iot devices meant for lan usage do not set a gateway. Or they could have firewall blocking access from anything other than their local network..
When troubleshooting anything like this be it port forward or access from another vlan.. Sniffing (packet capture) is your friend. Can be found on the diagnostic menu in pfsense.
Send your traffic be it from public internet or your other vlan - sniff on the interface the traffic will come in on.. Do you see it?
Ok now sniff on the interface on pfsense your destination device is on.. Send traffic again - do you see it being sent.. If so the problem is not pfsense.
The wan rule should have the destination port even if your changing it.. Because the nat(port forward rules) are evaluate first, and then firewall rules are evaluated to see if allowed.
Example I have this rule for my plex, outside is different port
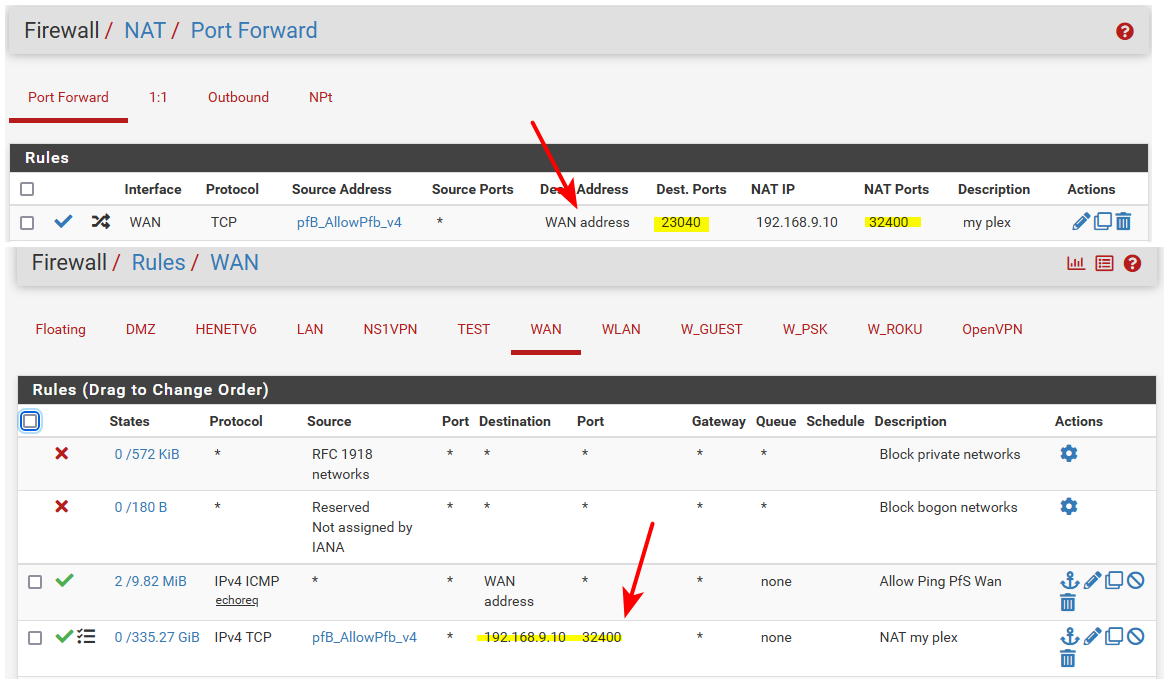
Your firewall rule with wan address is wrong.. And that is not what is created automatic with a port forward... Here on 21.05 just did a test forward.. port 4444 to 3333 for example.

When you setup a port forward - wan should be selected in the port forward rule. But the firewall rule on the wan will list the rfc1918 address your forwarding too.
here I just tested this port forward with can you see me . org. And while this device is not even listening on 3333 that sending the traffic too. You can see the traffic hit my wan in my sniff, and then sniff on the lan side interface sending the traffic on 3333 to the device.
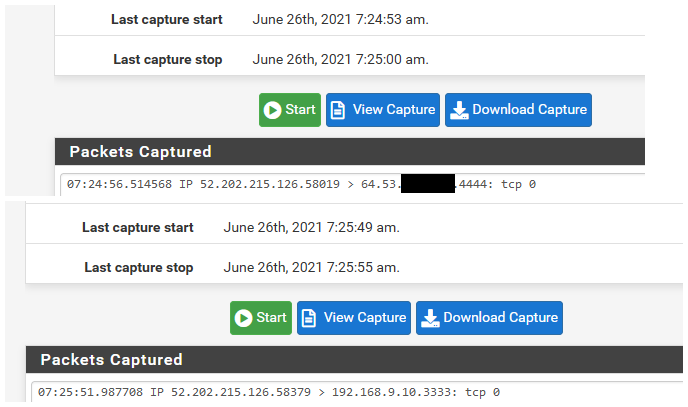
Pfsense doing exactly what told - if the device is not listening on the port, or doesn't have a gateway to get back, or a firewall. Or your sending to the wrong IP, etc. Then no it will not work even though pfsense doing exactly what told it to do..
-
@johnpoz Oh man! Thank you so much! Your explanation makes so much sense now!
So I simply misunderstood how NAT creates the rules and how the WAN rules work!
It's fixed now! You are amazing! -
@drew-kun said in Please help: VLAN and NAT port forward to Shadowsocks server behind pfsense (Netgate SG1100):
You are amazing!
And yet not even a thumbs up to say thanks..