WPAD + LIGHTSQUID
-
Hi guys, good afternoon.
Hope someone can help me with the following problem please.
I have my pfsense configured with wpad, the problem is that I also want to use lightsquid to get a monthly report of the network traffic generated with the users, the problem is that since I configured the wpad on my server the lightsquid process stopped working.
Does anyone know if these two services can work together? or if anyone knows why this is happening to me i've been thinking about it for days :(
Thanks !!
Sorry for my english, is not my language
-
@maria-1 They are not really related in any way. One does not directly affect the other. As for why Lightsquid isn't working, you haven't provided any detail at all so it's impossible to say.
-
@kom Sorry for not specifying.
I have 3 files: wpad.dat, wpad.da, proxy.pac on my server, each with the following content:
Function FindProxyForURL(url,host) { return "PROXY 192.168.1.1:3128"; }When configuring wpad I activated the dns forwarder, being as shown in the image:
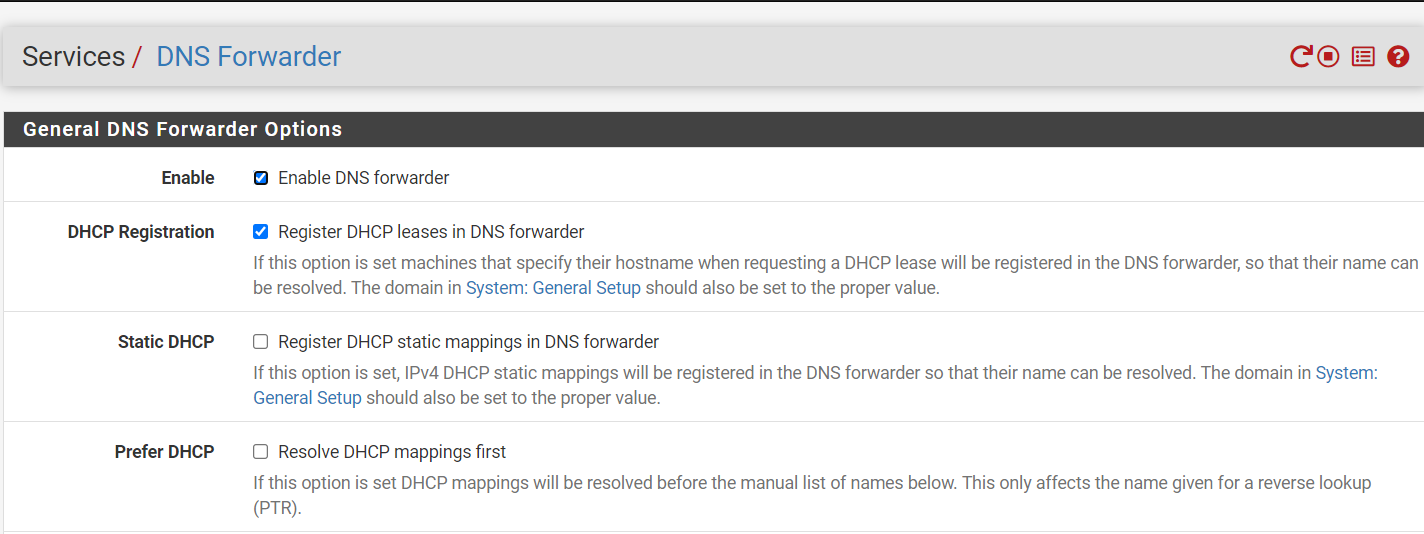
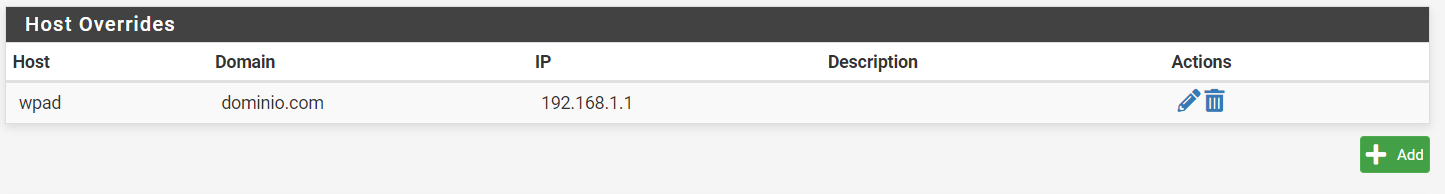
in advanced configuration I have https active.
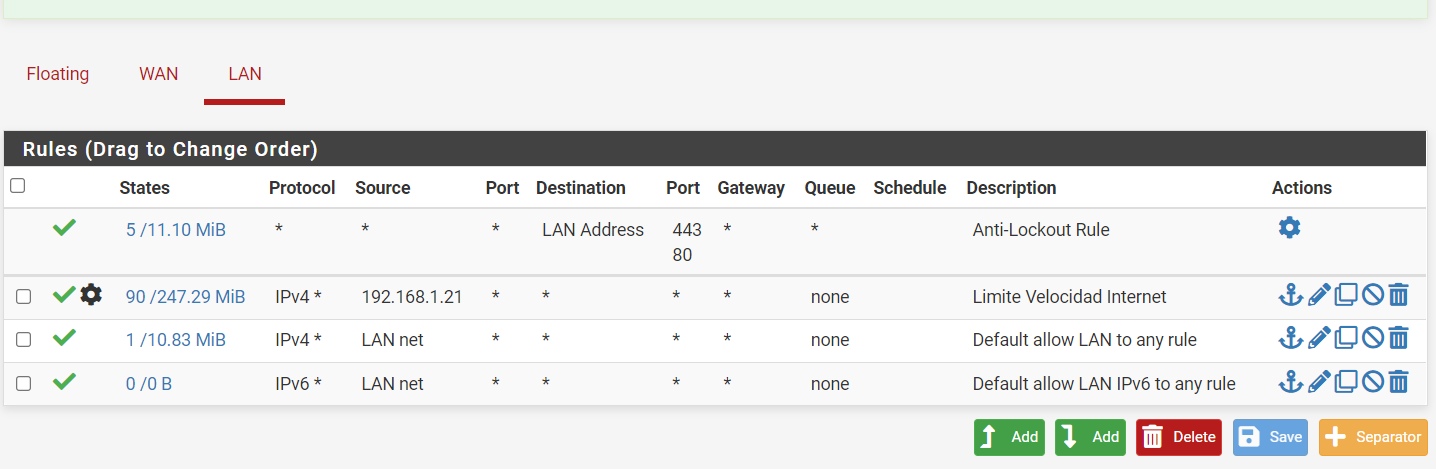
my rules only have the following, actually I have not put much.
in lightsquid I have the following box disabled.

Ligthsquid only records the following:
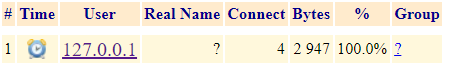
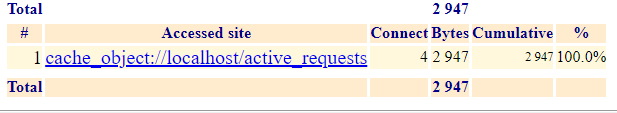
but I want it to record the activity per user and not just the localhost
I haven't been using the software for long, so I'm just learning it
Thanks
-
@maria-1 I am using pfsense 2.5.0-RELEASE but I have already tested it with previous versions and the same thing keeps happening
-
@maria-1 If I had to guess I would say that Lightsquid is working fine but you don't have any users going through your proxy. You aren't blocking access to tcp80,443 on LAN so how are you forcing people to use the proxy? Do a test where you manually configure your PC to use the proxy then go somewhere and then check the Squid access logs. Lightsquid can only report on what is in squids access logs. You do have squid set to log, correct? One thing I'm not 100% sure on but I thought that WPAD requires an HTTP server, not HTTPS.
-
@kom You're right, I did the test to manually configure the pc and it worked !!, I started to see activity in lighsquid
Thanks!!!You are also right about http for wpad, I did some more research and found out.
I'll fix what I have again thanks.

-
@kom Sorry to ask again, but now that I'm creating my rules, I notice another error :(
I have my rules as follows, where according to me I am already forcing the traffic to go through the proxy, but in rule number 5 I notice that the status is 0/0 and apart from that when I try to navigate I have no internet. . . .
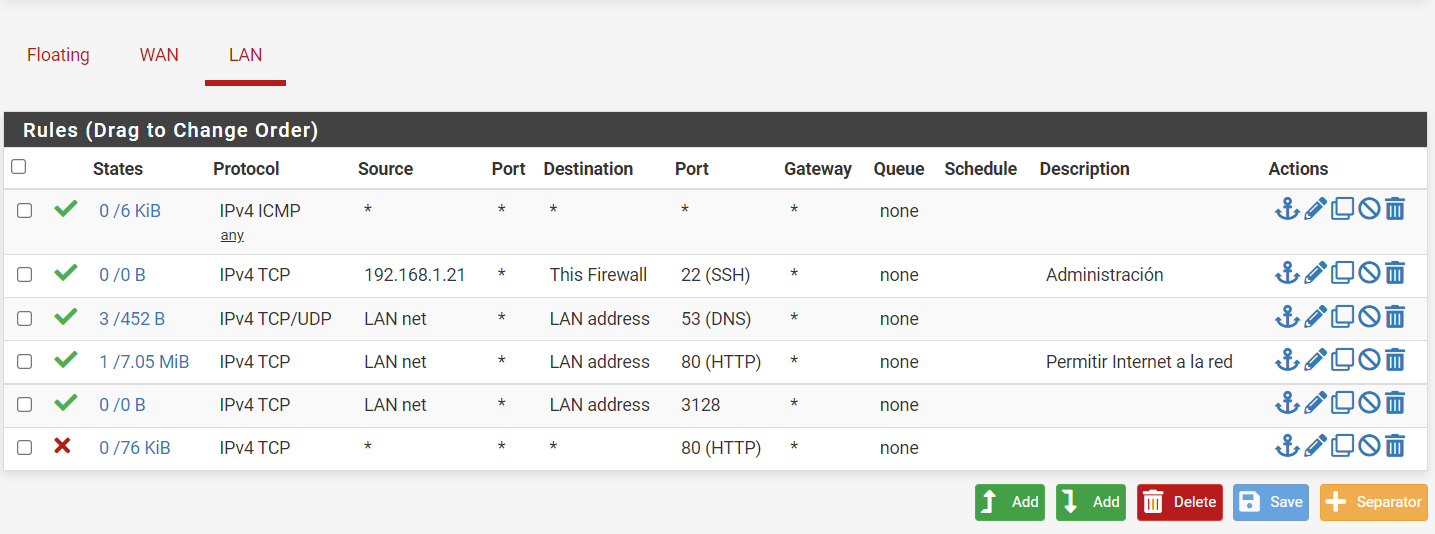
I am using the creative portal to enter the network.
The strange thing is that when I ping the server or a page from the terminal, I get a response.
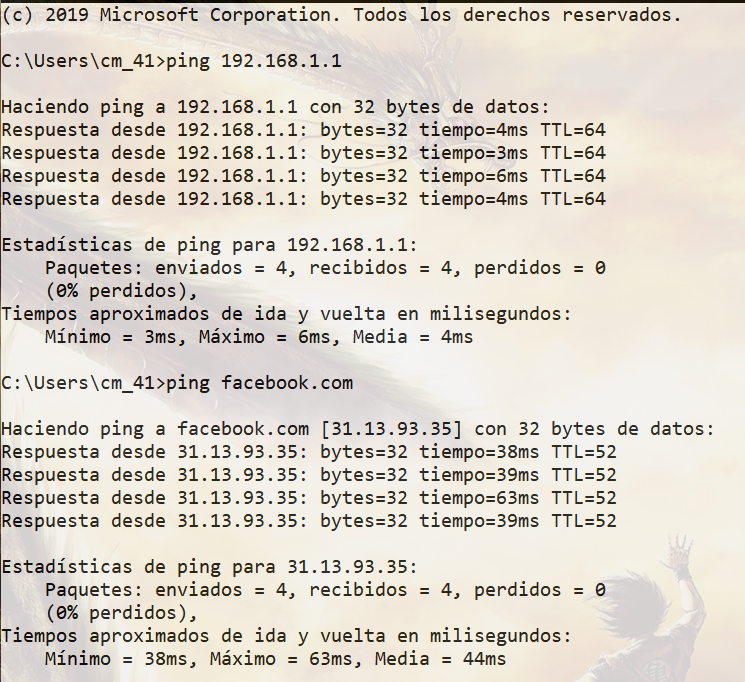
Could you guide me please?
I hope to be giving the necessary details.
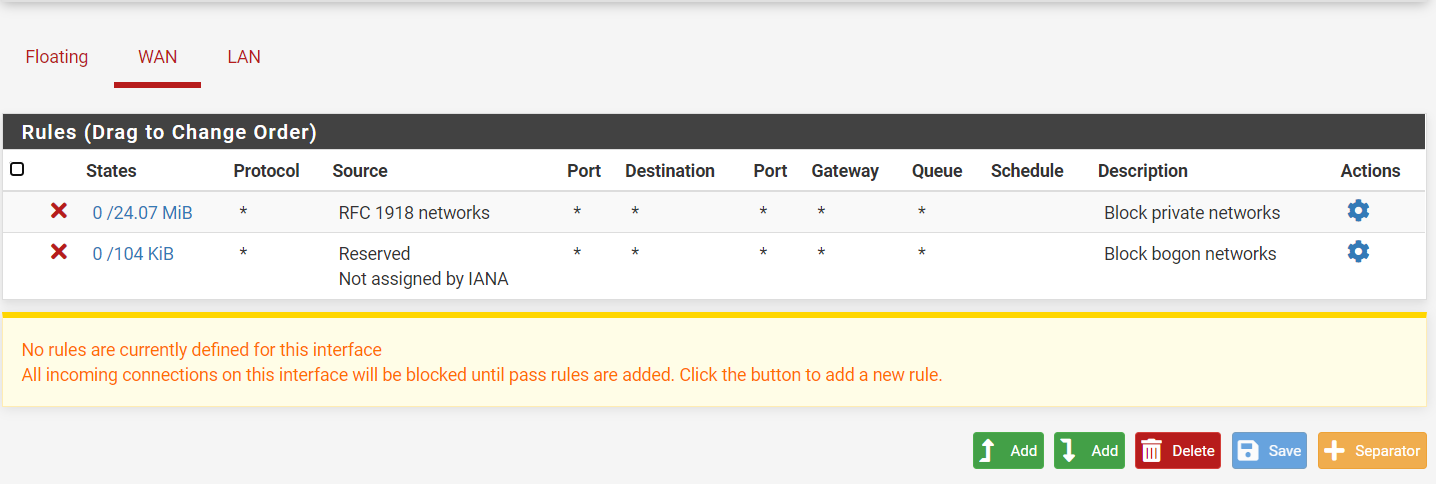
-
@maria-1 Your firewall rules are all wrong. Normally on LAN you do not want it to be too restrictive or else your users complain that things they need don't work. With that in mind, you would usually block what you want blocked and then allow everything else. You are trying to do the opposite where you try to allow some things and block everything else.
Firewall rules are processed top-down, first match wins and no other processing is done. Start by putting an Allow All to Any rule at the bottom. Then start stacking your restrictions above it.
I will go by your rules one by one:
- This won't be necessary since the Allow All rule at the bottom will handle everything.
- This rule is ok but could be better. Create a Port Alias called Admin_Ports and fill it with 22,80,443 and then use that alias in place of port 22 in your rule. That will allow only .21 to access pfSense via ssh or http/s. We will add a block rule later.
- Destination should be This Firewall if pfSense is your DNS server. There is a way to redirect all external DNS queries to pfSense if you want to capture all DNS.
- Add a new rule here that blocks LAN net to This Firewall
- This rule allows anyone to reach port 80 on pfSense. Inter-LAN traffic does not go to pfSense at all, so this rule only takes effect when someone tries to hit pfSense via tcp/80. It's not necessary and you can delete it.
- This rule is useless. What you want here is to create a Port Alias called Web_Ports and fill it with 80,443. You then create a block rule that blocks everyone from accessing anything via Web_Ports.
- Useless rule that should be deleted.
Before, you were not blocking tcp/443 which is https and the way 99.999% of websites are served now.
With tcp/80,443 blocked, nobobdy will be able to access any websites except through the proxy. You can create an IP alias to hold IP addresses of people allowed to bypass the proxy such as admins or management, and then create a rule directly above your tcp80,443 block rule to allow that alias to access anything.