Routed IPSEC Unifi devices hit the default deny
-
Good day,
Today I've replaced an aging firewall with a SG-5100 and everything went very smoothly.
I've got 4 IPsec VTI routed connections with OSPF managing the dynamic routing.
Everything works fine, all traffic is flowing due to an "Allow All" rule on the IPsec firewall Tab.When I look at the firewall log however: it's filled with connections from Ubiquiti Unifi products such as AP's and switches talking to the Unifi server on our main site (where the pfSense is).
All AP's and switches connect fine to the Unifi server and we'renot experiencing any trouble whatsoever.
It's just all those loglines in the firewall log that I want to get rid of.The culprit is (I think) the way Unifi devices make contact with the Unifi server.
I've tried a "pass" rule at the top of the IPsec tab with logging enabled to see if I could make it hit a rule, but it doesn't.
I've tried a couple of TCP flags options, but I don't really understand that.Does anybody know how I can get rid of all these loglines and/or what's causing them?
Here are some log lines and some raw log lines (they aren't the same).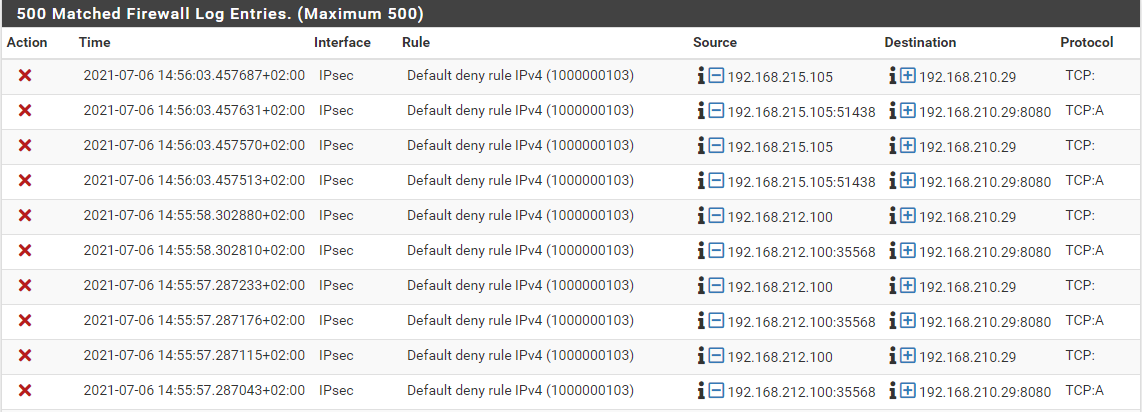
<134>1 2021-07-06T14:57:11.256670+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10064,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS <134>1 2021-07-06T14:57:11.256609+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10063,1376,none,6,tcp,124,192.168.213.101,192.168.210.29, <134>1 2021-07-06T14:57:11.256537+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10063,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS <134>1 2021-07-06T14:57:10.255314+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10062,1376,none,6,tcp,124,192.168.213.101,192.168.210.29, <134>1 2021-07-06T14:57:10.255258+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10062,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS <134>1 2021-07-06T14:57:10.255198+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10061,1376,none,6,tcp,124,192.168.213.101,192.168.210.29, <134>1 2021-07-06T14:57:10.255141+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10061,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS <134>1 2021-07-06T14:57:10.255081+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10060,1376,none,6,tcp,124,192.168.213.101,192.168.210.29, <134>1 2021-07-06T14:57:10.255023+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10060,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS <134>1 2021-07-06T14:57:10.254964+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10059,1376,none,6,tcp,124,192.168.213.101,192.168.210.29, <134>1 2021-07-06T14:57:10.254889+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10059,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS <134>1 2021-07-06T14:57:09.255509+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10058,1376,none,6,tcp,124,192.168.213.101,192.168.210.29, <134>1 2021-07-06T14:57:09.255453+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10058,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS <134>1 2021-07-06T14:57:09.255393+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10057,1376,none,6,tcp,124,192.168.213.101,192.168.210.29, <134>1 2021-07-06T14:57:09.255337+02:00 filterlog 96514 - - 8,,,1000000103,enc0,match,block,in,4,0x0,,63,10057,0,+,6,tcp,1396,192.168.213.101,192.168.210.29,45855,8080,1344,A,3107533259:3107534603,2524922705,913,,nop;nop;TS -
After some reading I think these are "out of state" connections and they are logged by the default deny rule.
Question: how can I make a rule to filter out these "out of state" connections going to that one ip address?
A rule with the option for logging turned of, so the packets don't hit the default deny.