IPSec routing issue (I think)
-
Hi,
I have an IPSec S2S between my on-prem pfsense device and a little Ubuntu VM in Azure running strongSwan.
The tunnel is connecting nicely, and I can ping from the Azure side both of the P2 tunnels that I created for 192.168.2.0/24 and 192.168.3.0/24.
The strongSwan host in Azure is 10.1.0.254 and it's serving the 10.1.0.0/17 subnet to the tunnel.
Pinging the Azure host from either the pfsense device or a device on 192.168.2.0/24 doesn't work. So I can ping in from Azure, but not png back to Azure.
I feel like this is an issue with my routing on the pfsense device, because I had this issue with WireGuard previously and as such I had to create a gateway from the WireGuard interface and define a static route to that gateway to get it to work.
With IPSec however, there is no interface presented for me to create a gateway, and therefore I am unable to create any static routes. So how am I supposed to route traffiv to 10.1.0.0/17 over my IPSec tunnel?
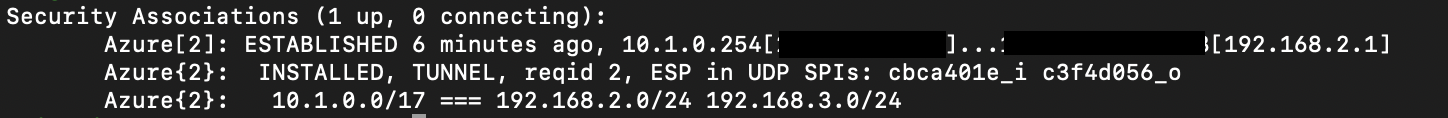
Also I notice this on the pfsense side:
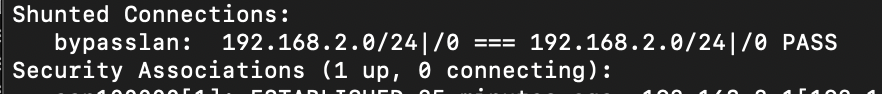
I don't know what that is but it's automatically done it so I assume it's a good thing?
Eh I informed myself on shunting, it makes sure inter-lan packets ain't going through the tunnel so it is a good thing.
-
Ok so after a metric f ton of googling, I came across this post:
https://forum.netgate.com/topic/118667/resolved-ipsec-tunnel-ok-but-routers-can-t-ping-each-others/4
Which points to this article: https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/access-firewall-over-ipsec.html
Which describes the procedure of making the static route as defining the LAN interface as a gateway, and assigning routes to it. I did that and at least i can ping through the tunnel to the Azure host now.
Now I just need to be able to ping past the Azure host.
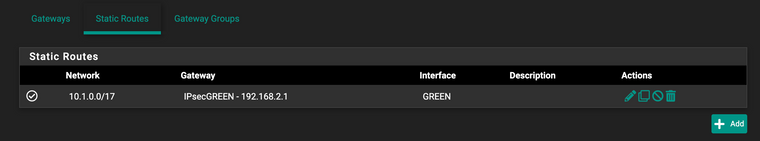
-
Aaaaand pinging beyond the Azure host was, as per my gut feeling, I shouldn't have been relying on the little IP forwarding switch in Azure and it was solved by enabling IP forwarding on the Azure host directly:
sudo nano /etc/sysctl.confnet.ipv4.ip_forward = 1 net.ipv6.conf.all.forwarding = 1 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0sudo sysctl -pSource: https://www.tecmint.com/setup-ipsec-vpn-with-strongswan-on-debian-ubuntu/