Routing only / Disable all packet filtering.
-
From our new ISP we have been given a public main IP, and a block/29 of public IP’s which we then need to route to.
So my idea was to use a pfSense as a ‘routing only platform’ by Disable all Packet filtering on System / Advanced / Firewall & NAT. But I have ran it some problems
My test set up look like this, where I try to simulate the ‘real world’:‘Wan’
Main IP: 20.30.40.2
GW 20.30.40.1
‘Lan’
50.60.70.1/29<192.168.0.0> Firewall1 < 20.30.40.0> pfSenseRouter <50.60.70.0> (and in real life our mail firewall comes here)
On each network i have a test-webserver:
- WebSrv1 on <192.168.0.0>
- WebSrv2 on <20.30.40.0>
- WebSrv3: on <50.60.70.0>
When I haven’t disabled packet filtering, then I can ping/browse ‘upstream’ e.g. from WebSev3 i can access WebSrv2 and WebSrv1
But when I disable it: From WebSrv3 can’t access WebSrv1, regardless of if I place a static route on Firewall1 where I point at the <50.60.70.0> network via the WAN-interface on pfSensand, or let WebSrv1 default gateway point at the WAN interface on Firewall 1.
There is no problem both up and downstream between WebSrv2 and WebSrv3.Any suggestions where my problem is?
-
@automan said in Routing only / Disable all packet filtering.:
But when I disable it: From WebSrv3 can’t access WebSrv1, regardless of if I place a static route on Firewall1 where I point at the <50.60.70.0> network via the WAN-interface on pfSensand, or let WebSrv1 default gateway point at the WAN interface on Firewall 1.
I suspect the firewall is the default gateway on WebSrv1. If so you need to add the static route on WebSrv1 for correct routing. Otherwise you will run into an asymmetric routing issue.
-
Hi Viragomann
Thanks for your reply, pls. notice, as i wrote: "or let WebSrv1 default gateway point at the WAN interface on Firewall 1."
So WebSrv1 have the downstream Firewall1, as it's default gateway. Not its upstram firewall as its gw. -
What is the point of firewall1?
You understand you can have a public network that is routed to pfsense without having to disable the firewall right. Just don't nat it, and create the interface/vlan with your public space on it.
https://docs.netgate.com/pfsense/en/latest/recipes/route-public-ip-addresses.html
-
In my test environment, the firewall1 is just there to mimic the internet.
Pls. see the attached schematic of my test environment.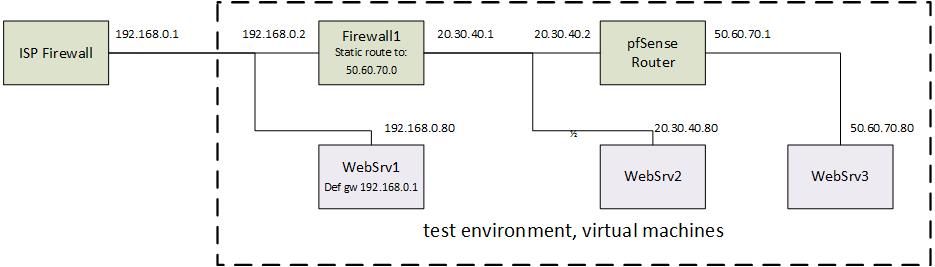
I was not aware of that feature you refer to, in the link. I must give that some attention tomorrow and test it out. What you mention, is what I tried to do by using the Disable all Packet filtering on System / Advanced / Firewall & NAT
Below you’ll see what i’m aiming at.
Thanks for your hint
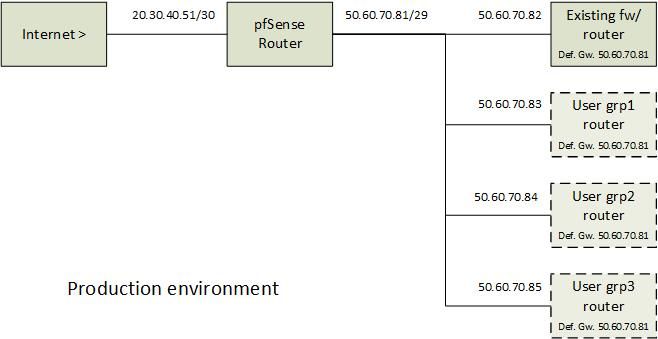
The IP's are just made-up.
-
Exactly your 2nd drawing is how you would do it.
Normally you have a transit network your /30 that routes whatever other networks, you then put your /29 just behind pfsense. You could then have other rfc1918 networks as well behind pfsense. Or other routed networks.. Or if you had a bigger network say a /28 you could subnet that and have 2 different /29s, etc.
-
This post is deleted! -
@johnpoz
As i could not get it to work, i created the example just as shown on https://docs.netgate.com/pfsense/en/latest/recipes/route-public-ip-addresses.html, but just with a larger segment on the 198.51.100.64 network, so i could have web-server on network to test against, I also place at web-server on 192.0.2.130.I did a 1:1 installation of the guide, however I still can’t pass traffic, such as accessing the any of the web-servers, across the router. From the router itself I can ping any hosts.
The web-server at the 198.51.100.64 segment, have the routers LAN interface as default GW 198.51.100.66, so it should be able to send any requests back.I’m controlling the router via a classic LAN setup (192.168.1.1) on a separate network.
I have also looked into https://docs.netgate.com/pfsense/en/latest/firewall/additional-ip-addresses.html#figure-multiple-public-ips-twoblocks-diagram without it have brought me any closer.
Any suggestions`?
-
@automan said in Routing only / Disable all packet filtering.:
Any suggestions`?
No not really because this just works - and without you showing what your actually doing have no idea what your doing wrong..
-
@johnpoz
would a couple of screenshots do? -
be a start.. This is really no different then setting up some other vlan/network... Your just not natting it.