Unable to reach ip alias on remote pfsense through ipsec tunnel
-
Hi all
I have two pfSense 2.5.2 boxes connected via ipsec. On the first box i have an ip alias 10.10.15.1/32 and on this alias is a webserver running at tcp port 80 and 443 - it's the webserver from pfBlockerNG-devel. My goal is to reach the webserver on 10.10.15.1 from the right side (10.0.2.0/24). This is my schema below.
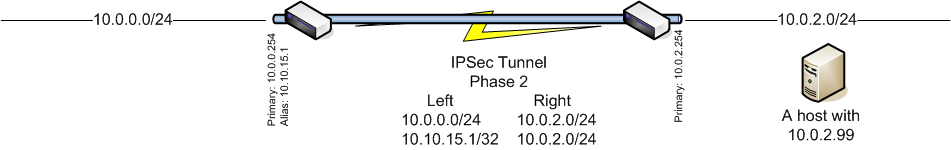
My host 10.0.2.99 can ping my ip alias 10.10.15.1, i can see the traffic flowing on 10.0.2.254
[2.5.2-RELEASE][admin@gw-ch-003]/root: tcpdump -i igb1 icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on igb1, link-type EN10MB (Ethernet), capture size 262144 bytes 13:05:19.379149 IP 10.0.2.99 > 10.10.15.1: ICMP echo request, id 1, seq 1466, length 40 13:05:19.395672 IP 10.10.15.1 > 10.0.2.99: ICMP echo reply, id 1, seq 1466, length 40 13:05:20.385170 IP 10.0.2.99 > 10.10.15.1: ICMP echo request, id 1, seq 1467, length 40 13:05:20.401283 IP 10.10.15.1 > 10.0.2.99: ICMP echo reply, id 1, seq 1467, length 40 13:05:21.388536 IP 10.0.2.99 > 10.10.15.1: ICMP echo request, id 1, seq 1468, length 40 13:05:21.409268 IP 10.10.15.1 > 10.0.2.99: ICMP echo reply, id 1, seq 1468, length 40 13:05:22.393433 IP 10.0.2.99 > 10.10.15.1: ICMP echo request, id 1, seq 1469, length 40 13:05:22.405288 IP 10.10.15.1 > 10.0.2.99: ICMP echo reply, id 1, seq 1469, length 40Interesting is, i can not see the traffic on the other side (interface with 10.0.0.254).
More interesting is, if i issue a telnet to 10.10.15.1 on port 80 from 10.0.2.99 to check if i can reach the http server, then i do not get any response.
[2.5.2-RELEASE][admin@gw-ch-003]/root: tcpdump -i igb1 src 10.0.2.99 and port 80 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on igb1, link-type EN10MB (Ethernet), capture size 262144 bytes 13:10:09.328352 IP 10.0.2.99.62984 > 10.10.15.1.http: Flags [S], seq 959874038, win 64320, options [mss 1340,nop,wscale 8,nop,nop,sackOK], length 0 13:10:10.339211 IP 10.0.2.99.62984 > 10.10.15.1.http: Flags [S], seq 959874038, win 64320, options [mss 1340,nop,wscale 8,nop,nop,sackOK], length 0 13:10:12.352183 IP 10.0.2.99.62984 > 10.10.15.1.http: Flags [S], seq 959874038, win 64320, options [mss 1340,nop,wscale 8,nop,nop,sackOK], length 0 13:10:16.359187 IP 10.0.2.99.62984 > 10.10.15.1.http: Flags [S], seq 959874038, win 64320, options [mss 1340,nop,wscale 8,nop,nop,sackOK], length 0Interesting is, i also can not see the traffic on the other side at (interface with 10.0.0.254)...
Additional facts:
- There are no firewall rules preventing the communication.
- The webserver is reachable from any host on the left side (10.0.0.0/24).
- The ping response comes from the ip alias on the other side (if i change the ip alias to another address, then the ping does not answer anymore).
Wtf? Any idea?
Best regards
Tom -
Have you set up routing to that alias? Otherwise, the computer on the right has no idea how to reach it and will try to use the default route.
-
@jknott
The traffic goes through the IPSec tunnel because the networks are defined in IPSec phase 2.