DNS Resolver reverse lookups question
-
Hi all,
Running pfSense 2.5.2, I have followed the following Netgate article to enable DNS over TLS:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html.All is well, except for the fact that local lookups are now quirky, as in returning the right name for the firewall in nslookup requests, observed when connected on VLANs (the .10 VLAN in this case is the 'trusted' VLAN in my situation):
C:\Users\w10test>nslookup microsoft.com Server: UnKnown Address: 192.168.10.1 Non-authoritative answer: Name: microsoft.com Addresses: 40.113.200.201 40.76.4.15 13.77.161.179 40.112.72.205 104.215.148.63This behavior happens on VLANs that are outside of the native VLAN where pfSense is located in. As soon as I plugin the laptop to the management VLAN, it nicely returns 'firewall.home.lan', which is the name I set under General Settings:
C:\Users\w10test>nslookup microsoft.com Server: firewall.home.lan Address: 192.168.1.1 Non-authoritative answer: Name: microsoft.com Addresses: 40.113.200.201 40.76.4.15 13.77.161.179 40.112.72.205 104.215.148.63I understand "server: UnKnown" is due to all DNS requests being forwarded to Quad9 (which I have selected as public resolver) because that's what the article prescribes, which of course subsequently fails to resolve names that are intended to be resolved locally.
DNS Resolver is configured with following options:
- Network Interfaces: all of my VLANs + localhost
- Outgoing Network Interfaces: WAN
- DNSSEC, query forwarding and SSL/TLS for forwarded queries is enabled
- Static DHCP reservations checkbox is enabled
When searching the forum, I found, among other posts (which not yet led to a solution) a post from @johnpoz here, talking about host overrides that are to be used to return the name of the pfSense system, fixing what I currently notice.
My question is: Is this the right thing to do, or are there more elegant alternatives?
Looking for advice. Thanks! -
@mg85 said in DNS Resolver reverse lookups question:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html.
That should prob be updated to address the changes that were done for dns lookups..
pfsense should always just ask itself for dns. Which then if the resource is not local - then sure it could use dot to whatever you want to forward too.
There was an issue with the old way of putting dns in the general tab, where pfsense might ask something remote vs just asking the local unbound, which then in turn asks upstream..
Your client asking pfsense for dns, should always return the local host name of pfsense. Or something is wrong with resolving your local stuff.
If you see unknown like you did - then yeah something is not right.
-
@johnpoz thanks so much!
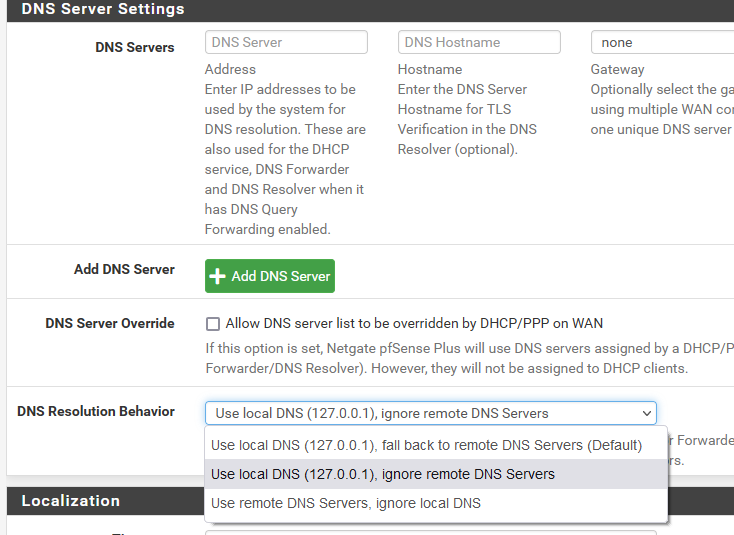
I have just set that option to "Use local DNS (127.0.0.1), ignore remote DNS Servers".
Hope the pfSense team is picking up on adapting the manual, as you indicate ;).The behavior that "unknown" is returned with nslookups is however not yet gone.
In your post, you mentioned you created host overrides for your VLANs. I have applied this just to test, which indeed returns the DNS suffix I have set under the DHCP configuration for that VLAN.Do you recommend to implement the host overrides this way?
This is by the way not a huge issue, as I can resolve local hosts by providing the full FQDN (e.g. "printer.iot.home.lan", which returns 192.168.20.5, which is my printers IP.Thanks again!
-
if your goal is for say devices on 192.168.x/24 using 192.168.x.1 (pfsense) as their dns to return say pfsense.xdomain.tld and devices on say 192.168.y/24 using 192.168.y.1 (pfsense on this vlan) to return pfsense.ydomain.tld then yes a simple host override is the easy solution..
example... my pfsense domain is local.lan, if I ask 192.168.9.253 (pfsense lan IP) it comes back with pfsense name..
$ nslookup www.netgate.com 192.168.9.253 Server: sg4860.local.lan Address: 192.168.9.253 Non-authoritative answer: Name: group3.sites.hscoscdn00.net Addresses: 2606:2c40::c73c:671e 2606:2c40::c73c:67e2 199.60.103.226 199.60.103.30 Aliases: www.netgate.com 1826203.group3.sites.hubspot.netIf I talk to one of its other IPs, 192.168.3.253 for example which is pfsense IP for my "dmz" vlan then it comes back as..
$ nslookup www.netgate.com 192.168.3.253 Server: sg4860.dmz.local.lan Address: 192.168.3.253 Non-authoritative answer: Name: group3.sites.hscoscdn00.net Addresses: 2606:2c40::c73c:67e2 2606:2c40::c73c:671e 199.60.103.30 199.60.103.226 Aliases: www.netgate.com 1826203.group3.sites.hubspot.netYou could prob get fancier today with views and such - but that is much more work to setup ;) then just a simple host override for what you want specific IPs to resolve to via PTR.
here are my host overrides
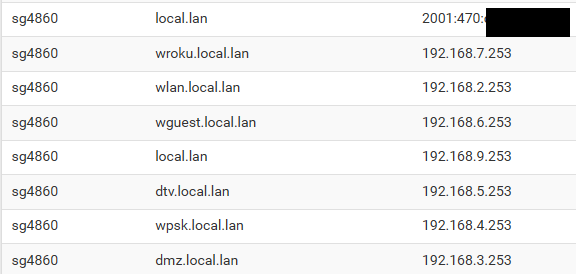
so if I query say the 4.253 address.
$ nslookup www.netgate.com 192.168.4.253 Server: sg4860.wpsk.local.lan Address: 192.168.4.253Once setup its a easy way to know exactly what vlan your on ;) since the name is returned in the pfsense domain for its IP address on that vlan.
-
@johnpoz gotcha, much appreciated! Implementing this right away ;).