Policy based routing stop working
-
Hi,
I am using PFSense 2.52 with tri WAN configuration.Everything works fine until some months ago. Now I see that rules with Policy Based Routing didn't work anymore.
The traffic specified in rule pass correctly but ignore the gateway selected and use the default gateway of PFsense.
If I disabled a rule the traffic not pass anymore, so the rule is working. But don't work only the PBR.
I notiche that the stats of rules that have PBR enabled still to 0/0 like this
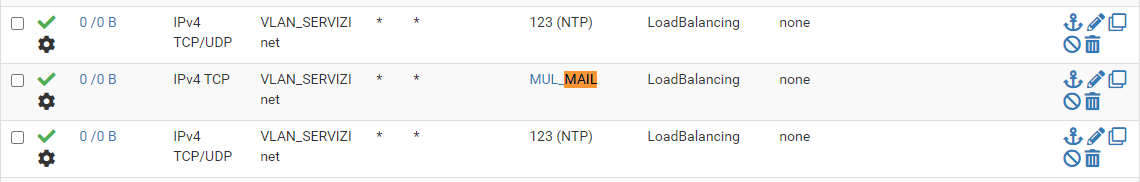
other rules without PBR have the stats counter correct

I can't undestand where is the problem...
-
Looks like the traffic isn't matching, but seems like it would be helpful to see the bigger picture. Post the full pic of your rules from each interface.
What subnet is VLAN_SERVIZI net? Where are you testing from and how are you testing? What ports are in the MUL_MAIL alias?
-
@marvosa thanks for answer
After a lot of searching I found the issue,
I had to be enable the "Disable Negate rule on policy routing rules" in "Advanced -> Firewall & NAT" because in negate_networks tables I found the 0.0.0.0 networks (it is in that table because I created a IPSEC VPN with 0.0.0.0 in remote subnet of phase 2).But I couldn't undestand what the option "Disable Negate rule on policy routing rules" does. What is negate rule?
Thanks
-
@polcape
Here's an explanation from the wiki:https://docs.netgate.com/pfsense/en/latest/config/advanced-firewall-nat.html#disable-negate-rules
-
Thanks @marvosa!
I read it, but it's not completely clear.
Can you show me an example of this negate rule that PFSense automatically insert? And that I have to manually insert if I check the option?Thanks
-
@polcape
TBH, I've never had a multi-WAN setup and didn't know this setting existed until yesterday, so it's not exactly clear to me either :)Although, skimming thru the explanation a few times and then coming across the IPsec section of https://docs.netgate.com/pfsense/en/latest/firewall/rule-methodology.html referenced here, negation rules appear to be hidden firewall rules generated for IPsec that negate policy routing:
"Because of the way policy routing works, any traffic that matches a rule specifying a gateway will be forced out to the Internet and will bypass IPsec processing. Rules are added automatically to negate policy routing for traffic destined to remote VPN subnets, but they do not always have the intended effect. To disable the automatic negation rules, see Disable Negate rules and add a firewall rule at the top of the rules on the internal interface to pass traffic to the VPN without a gateway set."
Unfortunately, the rules are hidden, so I'm not readily aware of how to generate an example. It may be as simple as a pass rule stating the source and the remote subnet. Regarding rules related to the tunnel, you'd generally want them to be explicit, so I don't think you want 0.0.0.0 configured as the remote subnet in your phase 2... this may have been the issue to begin with.
-
@marvosa Thanks a lot!
Now I understood