beginner-level question: pfSense versus AV on devices and router
-
Hello everyone,
[This is a newbie question.] For our home WiFi network, I have an Asus router with its own onboard AV protection and Bitdefender on our devices [Windows and iOS, and a NAS device with its own AV protection], and I would like to know what additional protection a pfSense appliance such as the Netgate 3100 will provide. This is for a residential network, not a commercial one. I do like the idea of a firewall in front of our home network as an additional layer of security, but before investing the time and $$$ I'd like to understand what it provides over and above these other layers.
Thanks for your help!
John -
@2cor521 I used to have a Zywall router with AV and intrusion detection that I paid for yearly. Issue with that on a router, looking at inbound traffic is, that most everything is HTTPS. Unless the router is doing man in the middle it's not doing very much as the traffic is encrypted. So I stopped paying, then went looking for something else and landed here, asking myself what you are asking now. I ended up with SNORT (intrusion detection) and PFBlocker installed. With those, I can block users from going to known bad sites, and the router checks for updates daily and those lists are chosen by me. Snort watches the LAN, not the WAN, again for activity going OUT which is suspect, and seeing the IP of the device doing it, I can respond to the device on my lan to clean it up if infected or if it needs to have software with known vulnerabilities updated. I can (and do) limit the outgoing ports to known ports for the programs I use and anything attempting to use some other random ports is blocked. I used to run a PROXY in PFSense with man in the middle setup to decrypt the HTTPS but found it too much trouble; PFBLOCKER and SNORT provide what I need with less hassle. PFSense also supports VLANS, which means you can segregate the IOT junk (doorbells, phones, game consoles, TVs...) onto another VLAN if your router supports that, and you can also use VLAN supporting wireless access points. Segmenting that stuff away from the PCs is a smart move. Yes it costs money if you don't have VLAN supporting hardware, but the point is that it can do it if needed. In the end, it's all about how much you are willing to learn and setup.
-
Separating you network into different VLANs for different risk devices is well worth it.
Anti-virus on a firewall/router is next to useless unless you're full proxying all traffic to/from the internal clients. And there is a strong argument to be made that simply doing that is a security downgrade!
AV on the firewall is definitely not a substitute to running on the devices. You need access to the hosts at a far deeper level than the firewall ever sees to do a decent job.Snort/Suricata can be useful once configured correctly.
Running pfBlocker to prevent hosts connecting to lists of known malware servers is useful.
IMO.

Steve
-
@stephenw10 said in beginner-level question: pfSense versus AV on devices and router:
Anti-virus on a firewall/router is next to useless unless you're full proxying all traffic to/from the internal clients. And there is a strong argument to be made that simply doing that is a security downgrade!
OH yes soooooo true and by the way
That's called somehow a full man in the middle attackDo it with style... Do VLAN firewall and pfblocker with AV on each client device,
When someone ask you why you do it this way tell them the guys who can read binary and calculate subnets in their head (aka the wise guys from the 90s) told you todo so

-
Thanks for the detailed responses. So would this be correct ...
- The Netgate firewall appliance would provide the first line of security, the internal segregation and the WiFi router capabilities, and I would no longer use the Asus router;
- The topology would be [incoming cable] -> [modem] -> [appliance] -> { internal devices };
- It isn't feasible to keep the router and have the topology [incoming cable] -> [modem] -> [appliance] -> [WiFi router] -> { internal devices } in order to add the firewall protection while retaining the services the router already provides (e.g., user time scheduling).
Thanks again for your help [and your patience with the new guy
 ]
]John
-
looks like something like this
/me not sure if you're mixin up te term of a wireless Access Point (like a Ubiquiti AcPro) with a
wireless router like a WRT54G i would go with Access Pointno you do not want double NAT or router cascade in your network ... more problems and issues
you will stumble across when u start using the full potential of pfSensescheduling per IP
limiter (up/down) per IP can easy be done by pfsense.keep in mind that if you want segregation all your switches must be capable to deal VLAN.
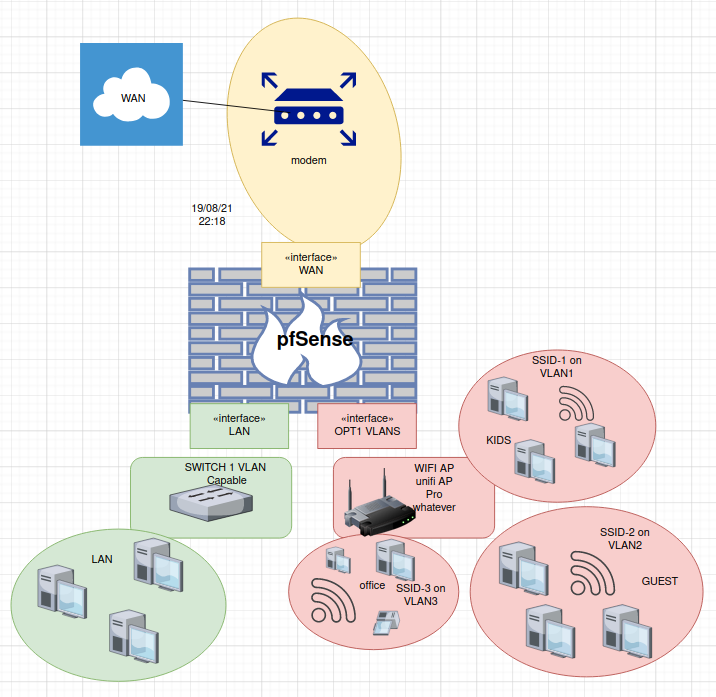
-
@noplan the one thing I would do differently (if you have the ports available) is connect your AP into your vlan capable switch. You can still use an uplink just for those vlans to another interface on pfsense.
But doing so allows you to also put wired devices onto those vlans that your using for wireless.
With your drawing, and only 1 vlan on that switch - it doesn't even have to support vlans, only your AP would since it looks to be directly connected into a port on pfsense.