Comcast Residential /64 Delegation
-
@bearhntr said in Comcast Residential /64 Delegation:
pfSense Firewall could be better adjusted for ICMP as well. As it is pretty much wide open on the ICMP port in the firewall.
What about the device your actually pinging - its firewall would also have to allow for ping, etc. While you might be allowing the icmp through to your client - doesn't mean your client is going to answer.
Some local server has zero to do for a PTR of public space - while it would be possible for you to set it up so your local devices could resolve them - the public internet isn't going to be able to. Not unless you got with ARIN and pointed to your NS as the the authoritative NS for that arpa space ;)
PTRs are handled by the owner of the IP space - in your case that is comcast. Comcast is the only one that can answer or set the records for that space. HE electric allows users of the space they hand out via tunnels to control that via a web interface..
-
@bearhntr said in Comcast Residential /64 Delegation:
Did you ever get this worked out? I seem to be stuck with one pending issue....says REVERSE LOOKUP - but I think that I have done everything correct.
Comcast wouldn't have any idea about host names on your LAN. They would likely have a host name for your WAN interface, but nothing behind it. You'd have to set up an external DNS that can be used for reverse lookup.
-
@jknott said in Comcast Residential /64 Delegation:
You'd have to set up an external DNS that can be used for reverse lookup.
Which comcast sure and the hell is not going to do ;) They are not going to let their residential clients set PTR records.. Or allow delegate some NS for some range. I would bet my house on that ;) Now if you have a business connection with them - they should be willing to set some specific records for you - since for example if your running some mail server off said connection. It would pretty much require a PTR to be able to send email to any of the major domains..
The arpa zones and where they point to for the NS is controlled by the owner of the IP space.. You could fire up 100 NS on the planet that all think they are authoritative for some .arpa zone for said space.. Nothing is going to ask them for their records until they are pointed to by ARIN or the RIR for that IP space..
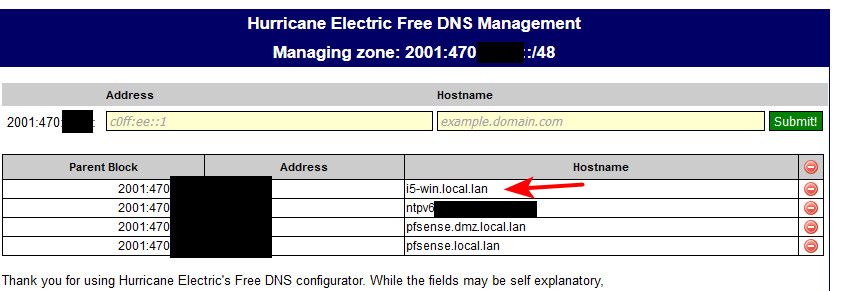
Here is some space I control with arin.. And how I can point specific space to specific NameServers.
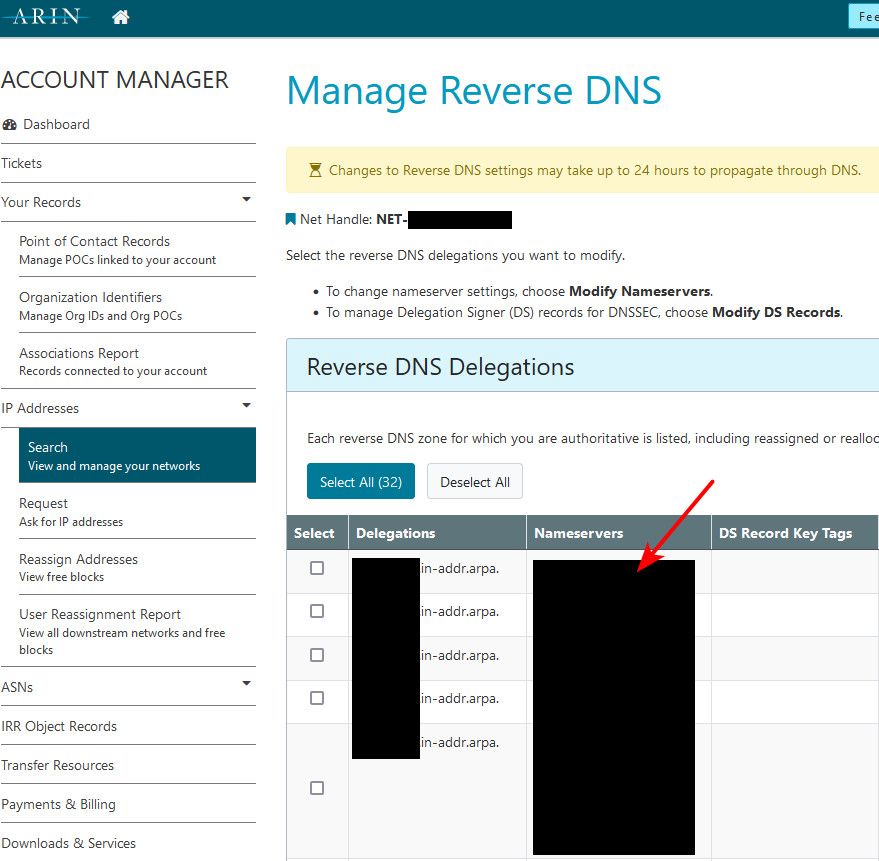
You can lookup the NS listed for any arpa zone with simple dig for the arpa zone asking for NS.
;; QUESTION SECTION: ;80.252.69.in-addr.arpa. IN NS ;; ANSWER SECTION: 80.252.69.in-addr.arpa. 7200 IN NS dns104.comcast.net. 80.252.69.in-addr.arpa. 7200 IN NS dns105.comcast.net. 80.252.69.in-addr.arpa. 7200 IN NS dns101.comcast.net. 80.252.69.in-addr.arpa. 7200 IN NS dns102.comcast.net. 80.252.69.in-addr.arpa. 7200 IN NS dns103.comcast.net.It works exactly the same way for IPv6 space..
Sure in a perfect world with IPv6 - the ISP if they assigned you specific space, like with HE an the /48 they give you - they could set it up so you could edit your own zones records, or even sure if we are making wishes allow you to delegate to your own NS for your arpa zone..
Now with IPv4 many an ISP do setup a PTR, even if it just points to generic sort of record with the IP in it. But this is something they have not really done for IPv6 - because well there are quadrillions of address, so records that would need to be setup, or system to create the response on the fly depending on what was queried for..
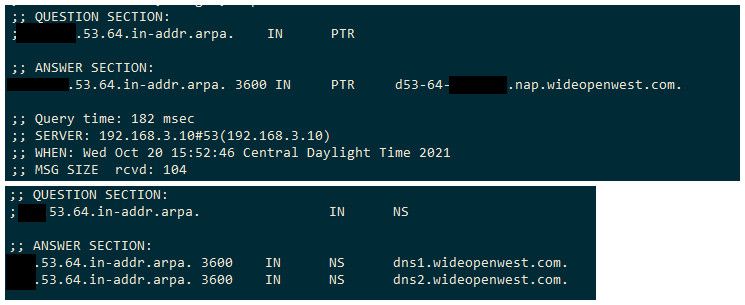
here is for example my isp NS for the zone my IP falls into.
-
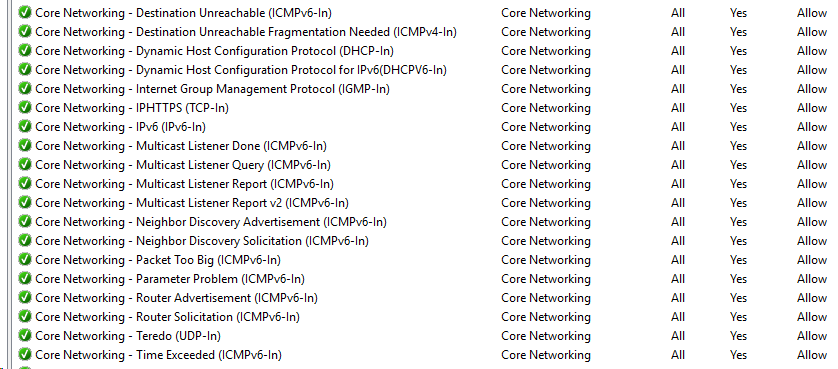
In windows when you enable FILE AND PRINTER SHARING and ALLOW NETWORK DISCOVERY - it enables these:
-
I have looked into ARIN - been reading their stuff for a while.
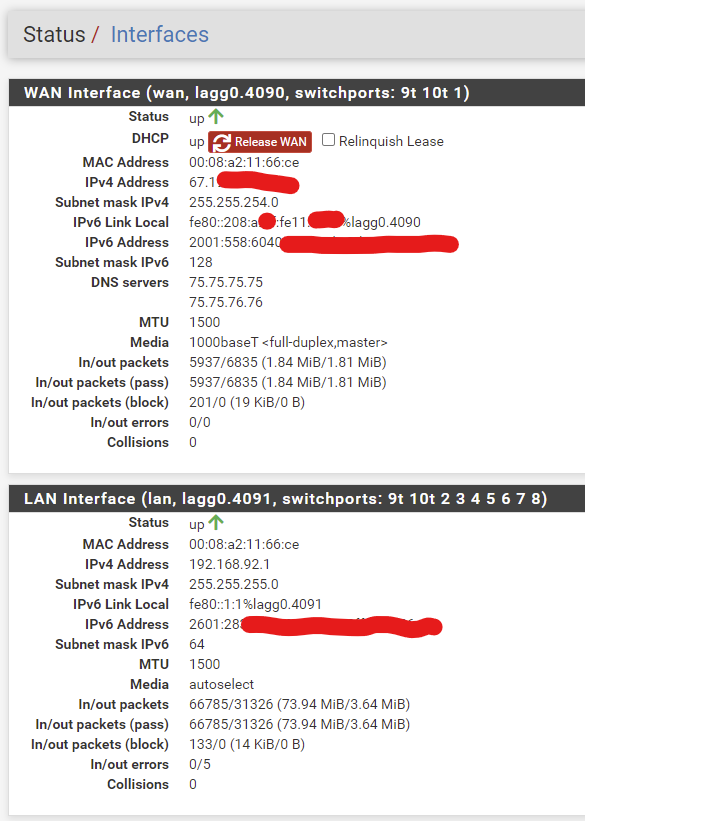
So in the grand scheme - should I change anything on my firewall to make IPv6 more secure? I can see why that IPv6-Test site sees my COMCAST Public IP Address - but still strange why it does not see the IPv6 address that Comcast gave me - instead it shows the IPv6 of the Static address (I made it up) on my Domain Controller.
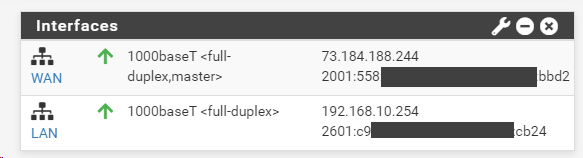
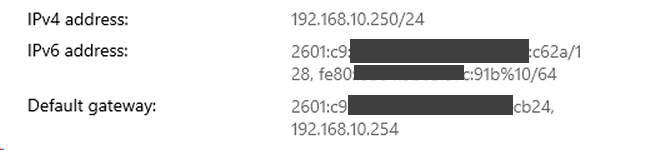
The WAN IPv6 was given by COMCAST - as it is set to DHCPv6 - The LAN - I set as static address after making up an address and testing it with an online CIDR tester.
As you can see below - this is from Windows Network properties (the address showing in IPv6 Test) is the address I have STATIC on my Windows computer:
This is from the https://ipv6-test.com/ site:
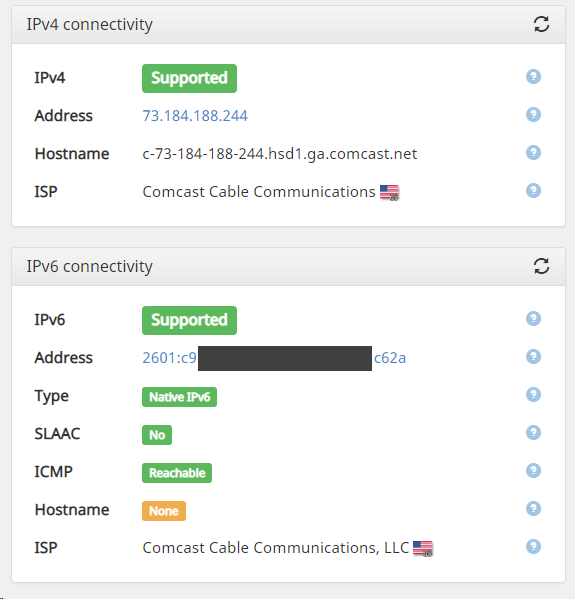
Curtis
-
@bearhntr said in Comcast Residential /64 Delegation:
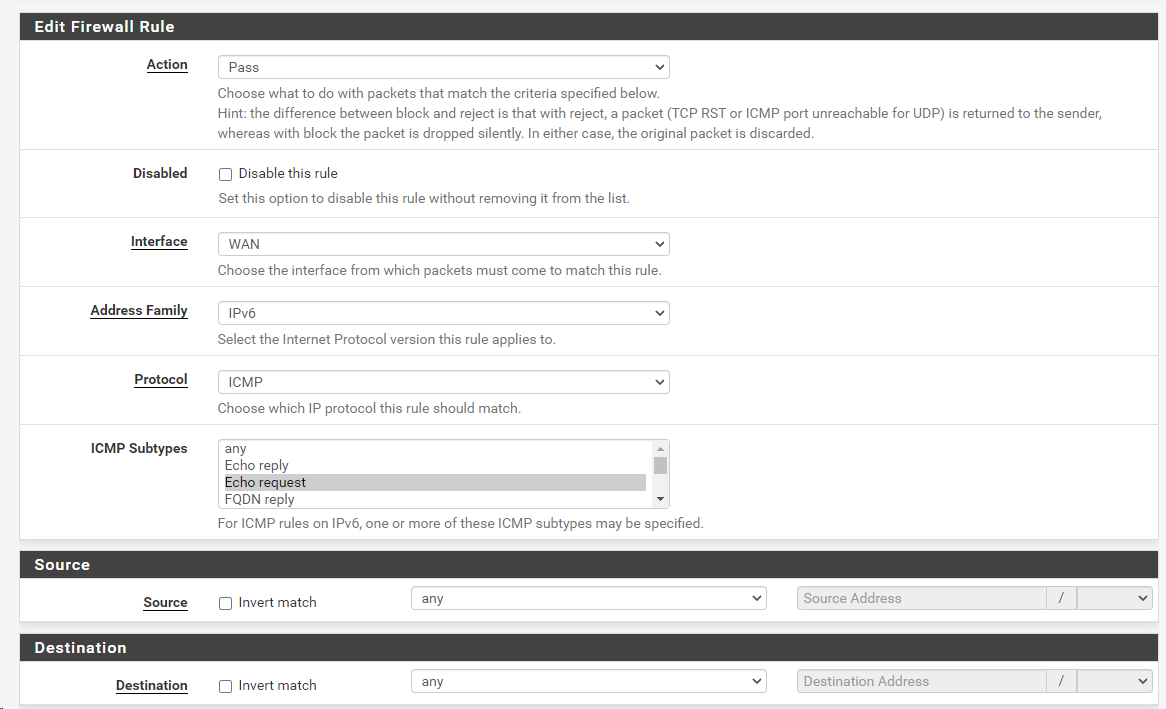
So in the grand scheme - should I change anything on my firewall to make IPv6 more secure?
I sure wouldn't do any any rule like you have ;) even for icmp
And have zero idea why you think you need to allow 547 and 546.. That is just a pointless rule..
Here is my ipv6 rules I allow inbound..
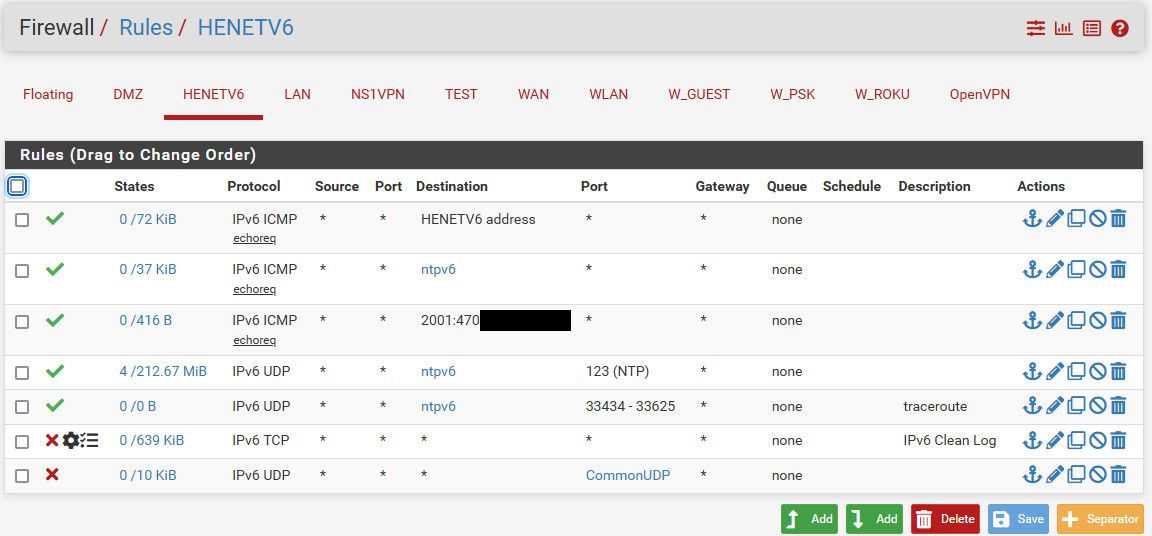
When it comes to a firewall, inbound - min required for stuff work is what should be allowed. I allow to ping my ntp server for ipv6, I allow to ping my tunnel IP for ipv6. I allow to ping my box for ipv6 (ping only).. I allow ntp to my ntp server, I allow traceroute to my ntp server - just because I like to see the it work.. Not really a requirement for anything..
-
@bearhntr said in Comcast Residential /64 Delegation:
but still strange why it does not see the IPv6 address that Comcast gave me
You're not using the WAN address when you go to out onto the Internet. You're using an address within your prefix. In fact, you could likely do without that WAN address, as it isn't used for anything other than identifying the interface. Even routing is normally done using the link local address.
-
This where the 547 and 546 came from:
https://homenetworkguy.com/how-to/configure-ipv6-opnsense-with-isp-such-as-comcast-xfinity/
Granted it is for OPNSense and not pfSense - but as I am reading OPNSense and pfSense are very similar.
Curtis
-
@bearhntr The rules needed to allow your wan to get dhcpv6 are there already - and would assume so in that other distro that will not be named.
More like the guy writing that just doesn't have a clue..
Once you set your wan to dhcpv6 - these rules are auto added..
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.html
# allow our DHCPv6 client out to the WAN pass in quick on $WAN proto udp from fe80::/10 port = 546 to fe80::/10 port = 546 tracker 1000000563 label "allow dhcpv6 client in WAN" pass in quick on $WAN proto udp from any port = 547 to any port = 546 tracker 1000000564 label "allow dhcpv6 client in WAN""using the “Track interface” setting, a firewall rule needs to be created to allow the DHCPv6 traffic from your ISP to assign IPv6 addresses to your local devices."
Oh yeah - as I thought not a freaking clue!!!
That is not even close to how it works! <rolleyes>
When using track interface, pfsense will assign a /64 prefix from prefix delegated to it from the ISP, ie your /56 or /60, etc.. This prefix on your lan side interface is the prefix used and clients on this network will get their IPv6 from this prefix from how you have it configured on pfsense to hand out IPv6 addresses in the prefix.. Sure and the hell not coming from your ISP dhcp server.. And how would that even work? The dhcpv6 is multicast, that isn't going to be sent out to your isp even with those rules.. Its sent to ff02::1:2, why would pfsense seeing this traffic on your lan side interface forward this multicast to your isp??
edit: Lets say it some how worked even remotely like that.. which it doesn't - how would pfsense even see this multicast traffic on the lan side? Your rules there for ipv6 are lan net.. The dhcpv6 coming from the client is going to come form link-local, ie a fe80 IP, which is NOT lan net.. So you have no rules there on your lan interface that would even allow pfsense to see this dhcpv6 traffic and forward it on - which it wouldn't because its multicast.
Good thing pfsense creates the hidden rules for IPv6 to work for dhcpv6 if you enable that on the lan, or the other methods of ipv6 clients from getting their IPs SLAAC
-
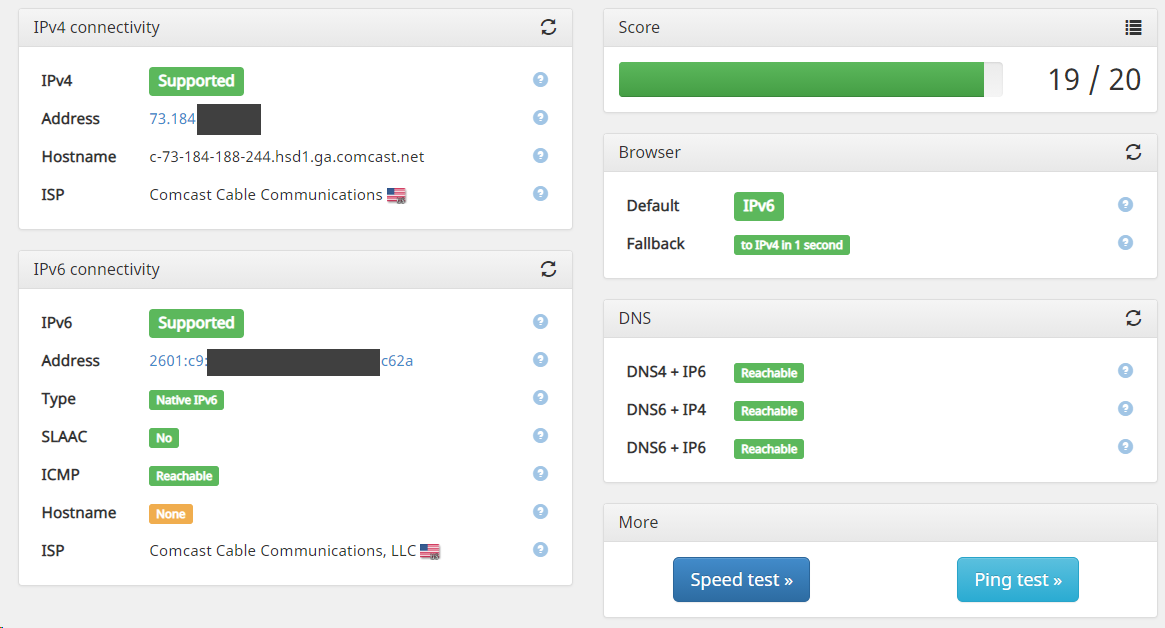
I disabled those 2 rules....
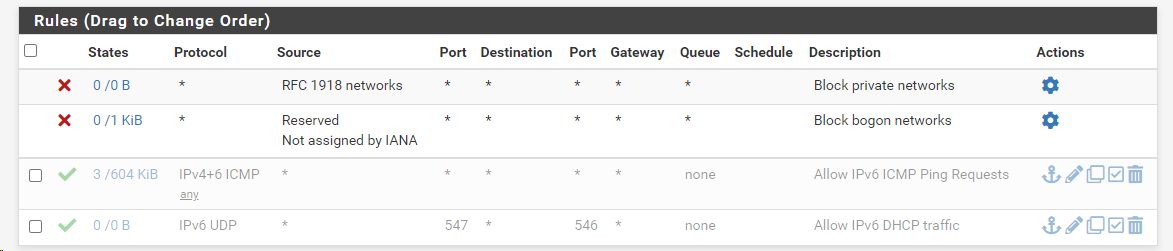
Then ran the IPv6-TEST again -- and now I am back to 17/20:
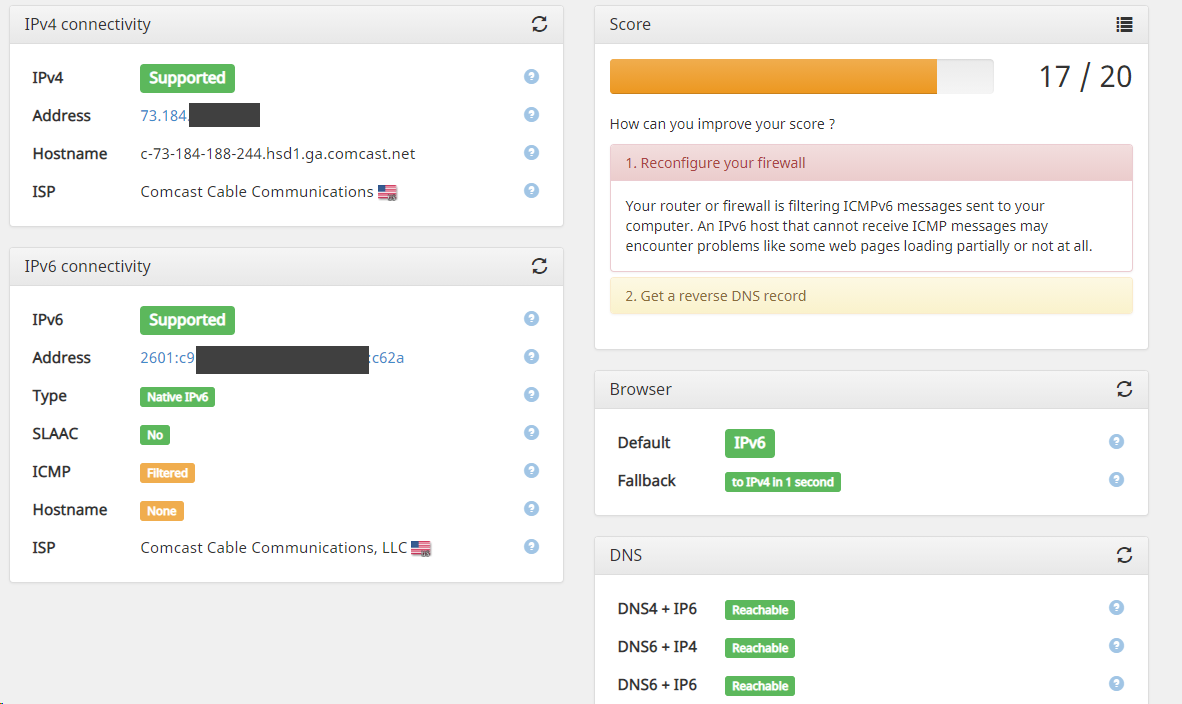
Curtis
-
@bearhntr you can allow icmp.. but your not going to get the PTR, and if no ptr hostname not going to resolve either. I would prob set it to just echo requests.. but you do you.
-
-
@bearhntr I see you hid your ipv4 this time, but its clear as day right there in your hostname for your IPv4, via the PTR - heheh
-
Yeup. I really do not care so much about the v4 IP address - - it will change by mid-day Saturday. <Grin>
I really want to grasp this IPv6 stuff. I would love to move more and more stuff in that direction. I have a few devices in my home which will not do IPv6 and the mfg. says they have no plans of supporting it anytime soon.
Curtis
-
First time I enabled ICMP for IPv6 and getting 20 of 20. Feels so good.

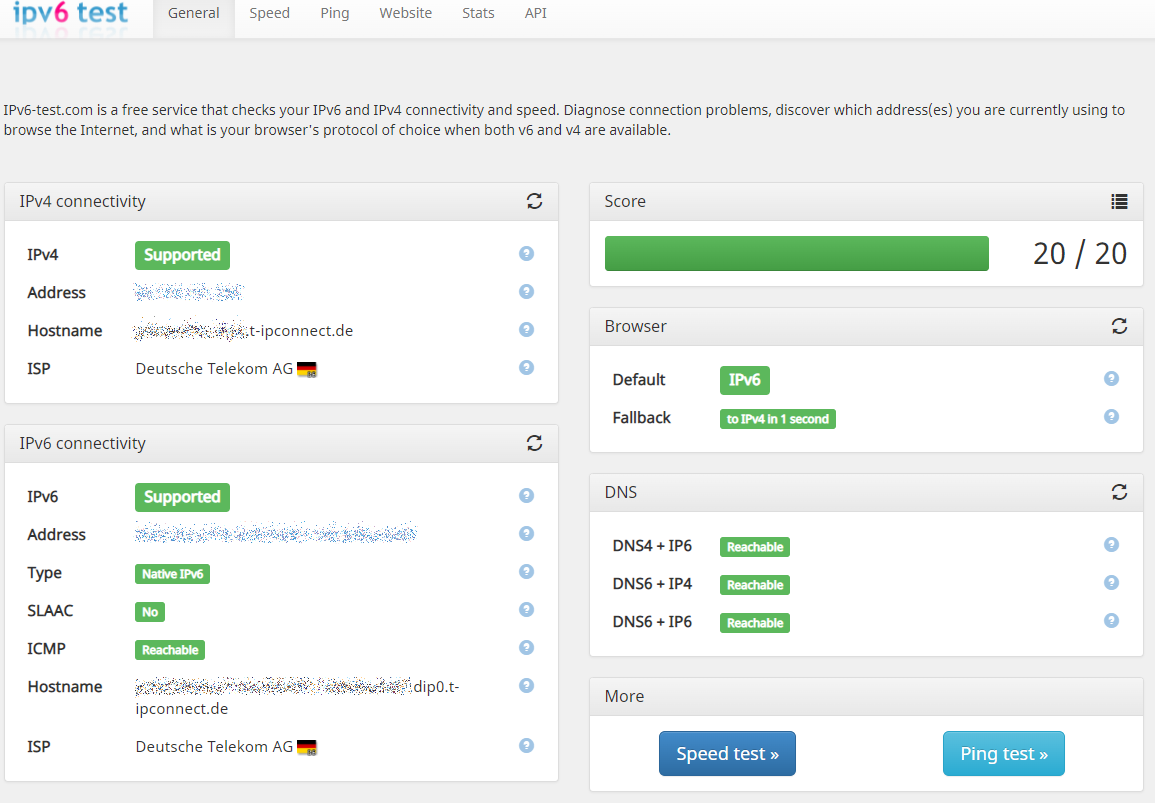
But in the end, never needed that ICMP for anything.
-
@bearhntr said in Comcast Residential /64 Delegation:
I would love to move more and more stuff in that direction.
Why to be honest? Can you name 1 resource that requires IPv6 that you want/need to access.. I agree that it is the future, and applaud your desire to learn it and play with, and sure even enable it.. But sorry no matter how much say jknott wants it to be now, ipv6 as the mainstream protocol is decades away..
Now - if some major players would push, it could be much sooner.. My isp has zero plans to support it, and its not even on their roadmap.. They just got bought by RCN, so maybe that will change..
I have it running on my network in a limited capacity - I can click a button and my pc has ipv6, as you saw for example in my test. But most of the time ipv6 is off.. I just don't really have any need or desire to run it as main protocol.. And it for sure makes limiting what can be done or not done through the firewall more difficult.. Clients love to have loads and loads of different IPv6 addresses they use for outgoing - so its more difficult to say for example my iphone IP can talk to my plex server IP from the specific wifi vlan.. With ipv4 I just assign it a dhcp reservation - and it always has the same IPv4 I can work with.
Not saying can't be done - its just more difficult, for why? Other than it is the "future" I have seen no actual need for it on my network, or for talking to the public internet.. My printer not having IPv6 support means nothing, who cares.. My smart lightbulb or some other iot device - again zero need or want for them to support ipv6.. For 1 it just makes it more difficult to manage..
So yeah learn and play and discover - happy to help in any way I can for sure.. But in the big picture.. The future is not right around the corner - you got plenty of play time heheh..
If you want some fun learning - go get sage cert over at hurricane electric, its free.. Fun to do, will help you learn different stuff about IPv6. And you get a free tshirt when you reach sage level.. Mine is getting a bit ragged - but I still sport it now and then..
Certification Level: Sage earned at 2011-01-26 09:05:43
-
I agree. For some masochistic reason I decided to see if I could figure this out. After I did, I asked myself, “Ok, that’s working. Good job. Now what functionality did it give me?”. I then proceeded to set IPV6 to none for WAN. There is so much more learning I can do that has a real return on investment.
-
I did not know there were t-shirts to earn. That changes everything.
-
@jpvonhemel said in Comcast Residential /64 Delegation:
There is so much more learning I can do that has a real return on investment.
Very true! I have been wanting to leverage IPv6 at work since 2010-11ish time frame.. Nothing ;) And I work for a major player.. I just recently helped them get /32 from Arin for use in a project..
I will for sure be retired before ipv6 becomes real mainstream protocol.. Sad but that is the way it is..
-
The US has plenty of IPv4 addresses. In other parts of the world this is not the case. For instance in Germany there is more and more IPv4 CG NAT and/or DS-Lite (Dual Stack Lite). So if you want to host something at home, you have to use IPv6... but also every major cellphone provider here supports it ootb, so it is doable, although it sucks big time.