is it possible to run multi DNS Resolver via IP Range?
-
hi i have dyslexia so try to bear with me in my explaining..so i trying to resolve DNS for VPN devices and WAN devices the same time
i use nordvpn for the computers and devices, and WAN for gaming computers, xboxs or whatever i need for WAN direct
i have a lancache server/docker running on my Unraid box that handles Game Updates and Windows Updates
so i send my vpn and clients to point to DNS 192.168.0.32
and in the lancache i change the upstream dns from 1.1.1.1 to 192.168.0.1
this way VPN and WAN can use the same DNS server..
but using 192.168.0.1 on WAN connections doesnt work right because the Resolver is setup for VPN connections
is there a way for PFsense to detect
say 192.168.0.2-50 is VPN ips go use the default DNS Resolver
and then 192.168.0.51-100 Is WAN ips go use WAN DNS Resolverso this way all computers would point to 192.168.0.32 for the caching server,, then it points to 192.168.0.1 and then Pfsense would determine by ip address which dns resolver it will use.. either the VPN or 1.1.1.1 for WAN this way there wouldnt be any DNS leakage.. is it possible.. if it isnt possible would it be a future request.. and if still confused i can draw a picture what i trying to do.. and if its possible a different route id try it too..
or do i need different ranges?
192.168.0.x VPNS computers
192.168.1.x WAN computers
to be able to point to 192.168.0.32 then it points back to 192.168.0.1 and resolve properly with no dns leakage etc -
I'm not 100% sure i understand your description or thoughts.
But here are some "options":
Typically DNS is set on a client either "static - typed by the user" or via DHCP, i'll assume you use DHCP here.The "simple" rule is that a DHCP pool will ALWAYS hand out the same (configured) DNS servers to the client getting an ip address from that pool.
The easy way to do it would be to use two interfaces/vlans , and get two pools , where you can configure different servers in each DHCP pool.
I would use this solution , just to get my workstations separated from my gaming stuff.The other might be solved with some policy routing where you match the source ip range , and the DNS port(s) , and policy route the DNS requests to a specific DNS resolver.
But .....
Assumptions:
192.168.0.32 is your Lan cache box
192.168.0.1 is your pfSense boxCan your Lan cache box do it's own resolving to ie. 1.1.1.1 (if configured for it ) ?
If so you could set your pfSense to use (only) the Lan Cache box (192.168.0.32) as "external resolver" , and point all your clients to the pfSense box (192.168.0.1).
Then all clients would ask pfSense for DNS , and pfSense would ask the Lan Cache box.
Edit: Hmmm ... I think i (might) get it now , the workstations (VPN) should avoid DNS leak , and use the VPN providers DNS boxes ....
I'd prob just go with two interfaces , and two DHCP pools.
Edit2:
If you have default gateway out of the VPN , i suppose you have to make sure that you won't send your WAN clients data , or WAN DNS to 1.1.1 - Out of the VPN default gateway./Bingo
-
@bingo600 id have to read up on that stuff.. i simple home user.. so at home i have xboxs and gaming computers and its a headache with them behind the VPN so i wanted it seperate..
with the lancache from unraid.. it has a upstream dns 1.1.1.1 but doing that leaks my vpns if i set the dhcp clients to 192.168.0.32 as the dns..
so i wanted my home computers, tvs, raspberry pis, cell phones all behind the vpn.. but the gaming setups to use wan 1.1.1.1.. but all have to use the lancache.. i dunno if pfsense has it i know kinda the proxy stuff i read in past to cache like Windows updates.. so that way 1 computer downloads like pfsense and then all the computers would get the updates from the pfsense .. but with the lancache it offers a storage in it for Windows updates.. so i wanted all computers to point to it..
and i have setup DNS Resolver for NordVPN like they mention and i know if i choose WAN connection it will leak the DNS as ipleak and dnsleaktest website says your leaking.. so cant do that
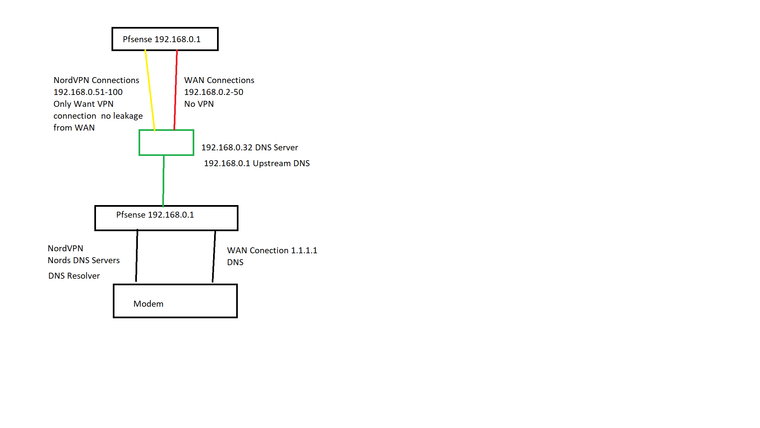
so i wanted a DNS Resolver for the VPN Clients.. and a DNS Resolver for WAN Clients.here is a pic i did in paint basiclly what i want it to do.. and since i not 100% advanced with pfsense may have to help me more.. since i dont use pfsense everyday moding it.. just a home user (:
is one of the ideas fall in this ?i have a 5mbp/s download connection i live in rural area so i dont get fast internet like majority.. so i find i get alot of dns error when i try splitting it.. or if the vpn connection isnt bogged down.. then pfsense can resolve like amazon or google com but its weird when google com doesnt work usually google ca works as i in canada.... so i think because i also have a slow connection and vpn there is probably something setup wrong to get the full advantage.. i think i still have something tweaked wrong that you know 2 things are conflicting..
but ya the pic is basiclly what i want it to do
and i changed the upstream DNS of the lancache in the green box from 1.1.1.1 to 192.168.0.1oh and i only have 1 cable from the modem to the pfsense box not 2.. i just mean it to go its seperate directions.. my dislexia gets in the way sometimes..
-
i also dont have really network switchs at home that can handle Vlan's
i got this one business cisco on i got given to me.. but it took alot to figure it out but then i stopped using the vlans..
everything i have is all on the 192.168.0.x-255 light switchs, computersx,xboxs, phones etc..
its the only setup i know from like 20 yrs ago using wingate and sygate sharing internet and kept it all on one..
so i not really experienced with Vlans -
@comet424
How many Lan interfaces do you have on your pfSense ?
If you have 3 or more you don't have to use Vlans.IF-1 : Wan
IF-2 : VPN
IF-3 : GamingI think your requirement that all boxes must be set to use the lancache box as DNS ,and the lancache must use 192.168.0.1 pfSense as DNS -
Will not go well with the requirement that you would like your VPN machines to use pfSense (VPN DNS) , and your Gaming machines to use ie. 1.1.1.1.
Unless it is ok , that the Gaming machines will use 1.1.1.1 DNS via VPN too , and your gaming machines would be seen as comming from the same country as the VON connects to.
That dilemma would have to be solved on your lancache since you insist that this box is used as a "common DNS".
@johnpoz - Could you chime in here (please) ?
I think @comet424 would have to use some policy routing , or if there's 3 IF's on the pfSense box , maybe some "def-gw" trickery per interface pointing to either VPN def-gw , or WAN-GW.I'm not experienced enough in ie. setting a specific def-gw for a "full IF"
/Bingo
-
Why are their 2 boxes on your drawing called pfsense with 192.168.0.1 as their address?
And no idea what dns has to do with any sort of lancache or proxy.. They are not the same thing at all. If you use a proxy, the proxy is what does the dns, not the client.
I have no idea how to get a proxy to use different dns based upon the client asking it for something.
If your using a transparent proxy - ok you can get the client to do dns, but that can not be the case if the proxy/lancache is on some box 192.168.0.32 - that would be an explicit proxy setup if your clients are pointing to it.
-
@johnpoz @bingo600
ah ok so i not persistant to be stuck with what i havei just trying to make it so 1 dns server the lancache-dns server
as for ports i do have a 4 port network card in the computer now.. i used to only have 2.. 1 for the network 1 for the wan
as for a common DNS ya i dont have another option.. other then WAN connections use the lancache dns server.. and the VPN devices dont use a lancache dns server and just have to download the windows updates from the internet instead of the lancache
i thought there would be simple way.. pfsense tells all the ips that 192.168.0.32 is the dns server main one.. and then it points back to the Pfsense box the real DNS server.. because i dont think pfsense can handle 2 or 4TBs of caching for games as id have gone that route.. cache it right off pfsense and put a 8tb drive in pfsense to cache all windows updates and games..
as for the reason for the 2 boxes of pfsense same ip thats showing you FLow of how it supposed to work what i want
starts off pfsense 192.168.0.1 gives dhcp from 192.168.0.2-255 the IPs from 2-50 get a VPN side.. 51-100 as the exmaple gets WAN connections
all DNS conenctions point to 192.168.0.32 as the DNS server.. then the DNS Server(lancache)192.168.0.32 points to 192.168.0.1 as the UPStream DNS
so then PFsense sees 192.168.0.15 then DNs Resolve using VPN DNS Resolver
when pfsense sees 192.168.0.66 then DNS Resolver uses 1.1.1.1
and then it goes out the modemthis way. WAN cant leak into VPN and the VPN connections cant leak in WAN i want them both the use the exact DNS server
unless pfsense offers a DNS Server for games and for windows update.. i was just making general comment about proxy or lancache.. i thought Proxy server.. cached Windows Updates to the drive so instead of going out to the internet it would just download from the proxy server.. thought that was the purpose.. if i wrong sorry..
hopefully my expaining bit better.. was trying to make the simpliest route.. using 1 DNS Server and keeping it seperate at the same time VPN and WAN seperate but use the same DNS for for windows Updates... as lancache dns server does windows updates and game caching
i couldnt draw it really i dont have a nice flow chart program.. so thats why you seen in the end 2 192.168.0.1 pfsense as it was just to show it went back up to the top and out the modem
-
also like i mentioned it be nice if DNS Resolver worked by IP Adresses's
so you'd have 2 DNS Resolvers or more
-
DNS Resolver sees IP range 192.168.0.2-50 then use VPN DNS Resolver Interface outgoing network
-
DNS Resolver sees IP range 192.168.0.51-100 then use WAN DNS Resolver interface outgoing network be WAN
its just a thought be a nice way to doing it.. this way pfsense could handle both requests at the same time.. and says ok this is a DNS Resolver for the VPN or it says no this one is for the WAN
but like i also mentioned i could have something miss configured too that isnt helping things..
reason why i mentioned in past.. to upload my pfsense config or have you guys log into my pfsense and fix any issues.. like MS does they log into your windows machine and see if they can fix it
-
-
and i thought this would have worked but this causes dns leakage on vpn side
i thought it wouldnt keep things seperate but it didnt
-
@bingo600 i gonna try something popped in my head
if i change the upstream dns ip from 1.1.1.1 and 192.168.0.1 to one of my VPNs dnsi know that when you watch youtube videos they all say use 1.1.1.1 1.0.0.1 that its the fastest dns on the internet.. and such.. i know my nordvpn goes down but i just thought of it now if i try it.. i dunno if it will work as that dns needs you logged in but when not using the vpn side may not work.. but figure i give it a try.. since i asking alot and i didnt mean to confus or make ppl frustrated.. trying to take something simple and made it complicated..
so ill try this and see what happens
-
Putting multiple dns in pfsense dns servers isn't going to do anything related to what you want to do.. Nor is there anyway to say which of those it will talk to for any given query..
People really need to get over this nonsense term, scare tactic of "dns leak" its such utter nonsense..
You understand be it you ask your isp dns or whoever - your isp still can tell exactly where your going via simple sni that is in clear text in your connection with https. And if just http its in the host header, again in clear... And they know exactly what IP your going to as well.
dns leak is a bs scare term put out by the companies running dns servers wanting you to send your dns queries to them..
Your not hiding anything from anyone - all your doing is handing where you want to go to someone asking you to tell you where your going - because we will hide it from the bad bad isp that is spying on you.. But they can't --- because even after you look up that www.whatever.tld is at IP 1.2.3.4.. you still send www.whatever.tld in your sni when you connect to 1.2.3.4 via https - and your isp sees that clear as day..
The only thing you can do with routing dns to some specific dns server is geoip resolution..
Your spinning your cycles trying to hide something you can not hide.. If you want to access netflix for region A while your in region B that is 1 thing.. But don't think leaking dns doing anything!! but wasting everyones time talking about --- arrghhh sorry for the rant!! ;)
Being worried about dns leaking is like being worried that your CC knows that you spent money at the liquor store.. While you took money out at the atm in the liquor store on your CC, and your CC runs the camera at the liquor store and sees what your buying anyway via the camera feed at the cashier. All you did is allow the company that runs the atm to know hey you getting money at the liquor store ;) You didn't prevent the CC from knowing exactly what you did..
-
I think you should "attack" this issue in two steps.
1: Get pfSense up and running with 2 client lan interfaces (VPN & Gaming)
1.a:
Make a VPN lan interface that sends everything out of the NordVPN connection
1.b:
Make a Gaming lan interface that sends everything out of the WAN connection.Now your basic VPN vs Gaming ip connectivity should be in place.
2: Get your lancache(s) working , and adjust the DNS to point at those.
I don't think you can solve this issue with just one lancache , as you want the lancache to use different DNS , depending on them being VPN or Gaming.I think you should install 2 lancaches, one for each Client lan (VPN & Gaming).
That might require 2 lancache machines or VM's , due to the requirement that the lancache should "exclusively" own port 80,443 & 53.
That requirement is unsolvable if they run on the same "machine".
Now you can point all VPN clients DNS to the VPN lancache machine on the VPN lan , and the Gaming clients DNS to the Gaming lancache machine on the Gaming lan.Could you skip the Windows Update cache and use the built-in WUDO on Win10 clients ?
That might save you a lancache on the VPN segment , that said ...
It seems like a new lancache would run ok , on an older machine lying around.It seems from here:
https://4sysops.com/archives/windows-update-delivery-optimization-wudo-in-windows-10/
That WUDO is enabled on all Win10 Clients.WUDO should enable Win10 machines to get updates from an already updated Win10 machine on the same "site".
/Bingo
-
@bingo600 said in is it possible to run multi DNS Resolver via IP Range?:
I don't think you can solve this issue with just one lancache
That.
pfSense, or the DNS service in it, cannot see the client IP queries come from, it sees only LANcache IP. That means it will do the same thing for all queries.
If you have twp LANcache servers you can setup pfSense to send queries via different upstream DNS servers. Or just configure that on the LANcache boxes directly.
You could also do this if one group of hosts doesn't go via the LANcache but there is no way to separate them if both do.
Steve