IPv6 and ICMP
-
Hello,
I have been configuring IPv6 on my Comcast residential account and often read that it relies on ICMP. I never allowed ICMP requests on IPv4. I did not want pfSense to acknowledge my private ip's existence and make myself a target for further penentration attemps.
An IPv6 test site returned that I was filtering ICMPv6 requests and again, it depends on ICMP to function correctly. I searched around and stumbled on this posting by cmb and @jimp years ago, that pfSense passes the necessary ICMP traffic for v6 to function. I do not have any WAN rules allowing it. Just thought I would post about this to learn more about how pfSense is passing ICMPv6.
Coming from IPv6, it is a really strange feeling when an IPv6 enabled test site can return the IP address of a machine on your LAN. I know I am supposed to consider NAT as evil, but it is hard not to feel it provided protection to my LAN hosts.
Edit: Grammar error
-
ICMP6 is used for a lot of things and is essential. For example, router discovery, neighbour discovery, duplicate address detection and more. However, it also has some security features such as packets for the local LAN only will not make it through a router. This is done by using a hop limit of 255. If a packet that requires this, such as solicited node multicast does not have that value, it will be discarded, as that value would not appear in a packet that passed through a router. That value also prevents it from leaving the local network, as a router would decrement it to 0 and discard the packet. Also, the IPv6 address space is so sparsely populated that it makes it difficult for an attacker to find anything to attack. Another thing is "privacy addresses" are normally used. These are used for outgoing connections and you get a new one every day, but they expire after 7 days. So, even if someone gets one of those addresses, it won't last very long.
You may think NAT provides protection, but that's a false sense of security and it does nothing that a properly configured firewall can do.
-
@jknott said in IPv6 and ICMP:
Also, the IPv6 address space is so sparsely populated that it makes it difficult for an attacker to find anything to attack.
Thanks for the reply. I suppose this could be considered security through probability :). I did notice the public ip my PC used for the internet is the temporary one.
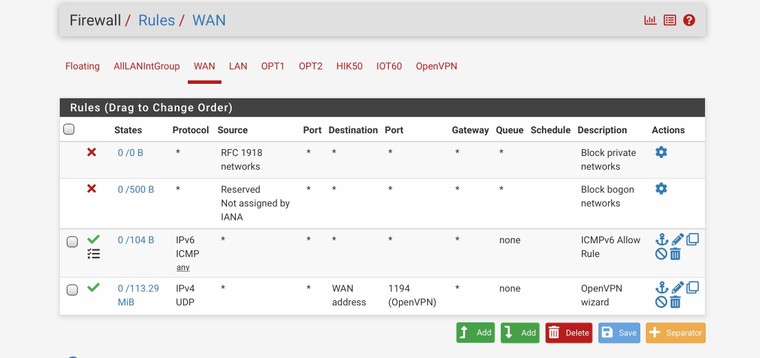
Should I be considering IPv6 ICMP rules on WAN? I temporarily allowed all for ICMP for WAN, and the test site passed. The post I found from @cmb mentioned ICMP packets necessary for proper function are automatically passed, yet the test site mentioned I was filtered until I added a pass rule.
-
You might want to allow ping. Most of the ICMP6 stuff is used on the local LAN and on the WAN side, pfsense is the "client".
As for sparse addresses, the standard LAN size is a /64, which has as many addresses as the entire IPv4 address space squared. In that huge space, you might have a few dozen working addresses at any time, most of which are temporary. Bottom line, you're not much of a target.
Did that test site list which ICMP6 it was testing?