Cannot PING pfSense from internal and vice versa
-
I volunteer in a local community networking refresh project. I have replaced all internal networking devices with Cisco Switch/Wireless Lan Controller/Access Points, all internal works fine. The pfSense is between my internal and Comcast Modem. This pfSense device is the only one I'll keep from previous equipment, running on a Lanner Electronics FW-7535H, pfSense version 2.3.4_!, for some reason I have not being able to upgrade from GUI for a while, it always told me my version was "up to date".
After I changed a few interfaces/vlans setting and tried to hook up from my Cisco 3750 to LAN port of pfSense. I cannot ping anything from Cisco to pfSense, I tried to ping from pfSense back to inside, I cannot ping either.
However, even though I have changed most VLANs and Interfaces on pfSense, I took the old switch(supposed to retire) back and hook on original port. It just works fine.
This is my Cisco 3750 uplink port config snippets:
interface GigabitEthernet1/0/48 description trunkportUpStream switchport trunk encapsulation dot1q switchport mode trunk ! ip default-gateway 10.30.54.1 ip route 0.0.0.0 0.0.0.0 10.30.54.110.30.54.1 is IP of LAN (vlan 1 on em1) from pfSense. I have config VLAN 1 IP on Cisco with 10.30.54.254.
I have checked all pfSense rules for each VLAN are allowed only.
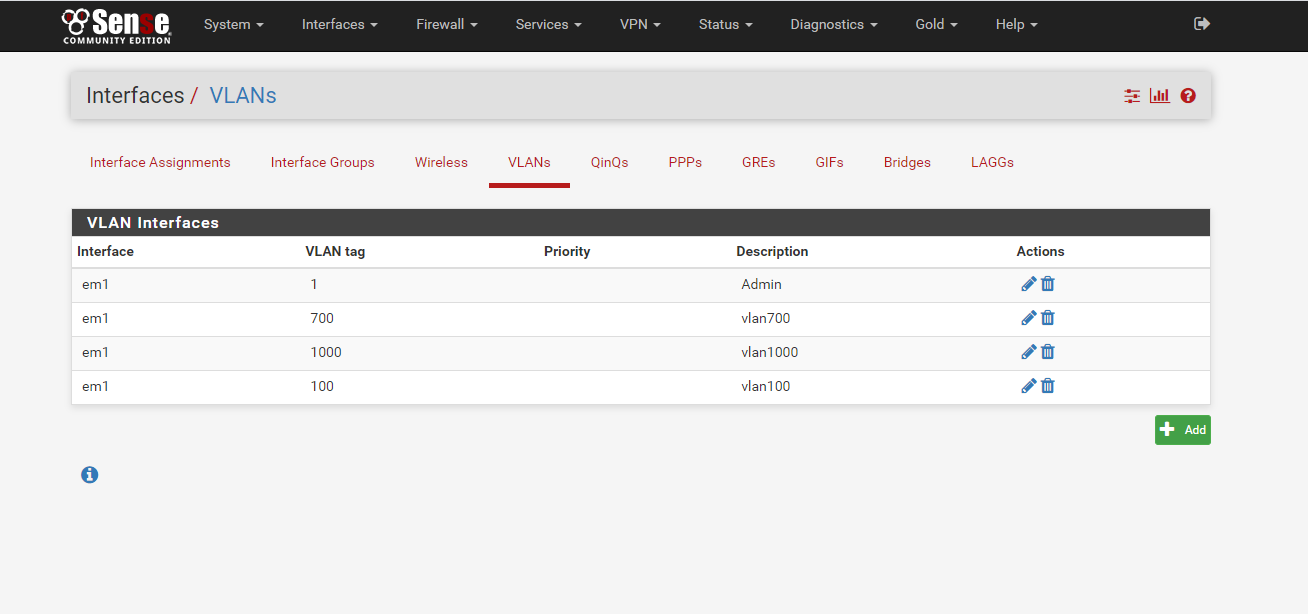
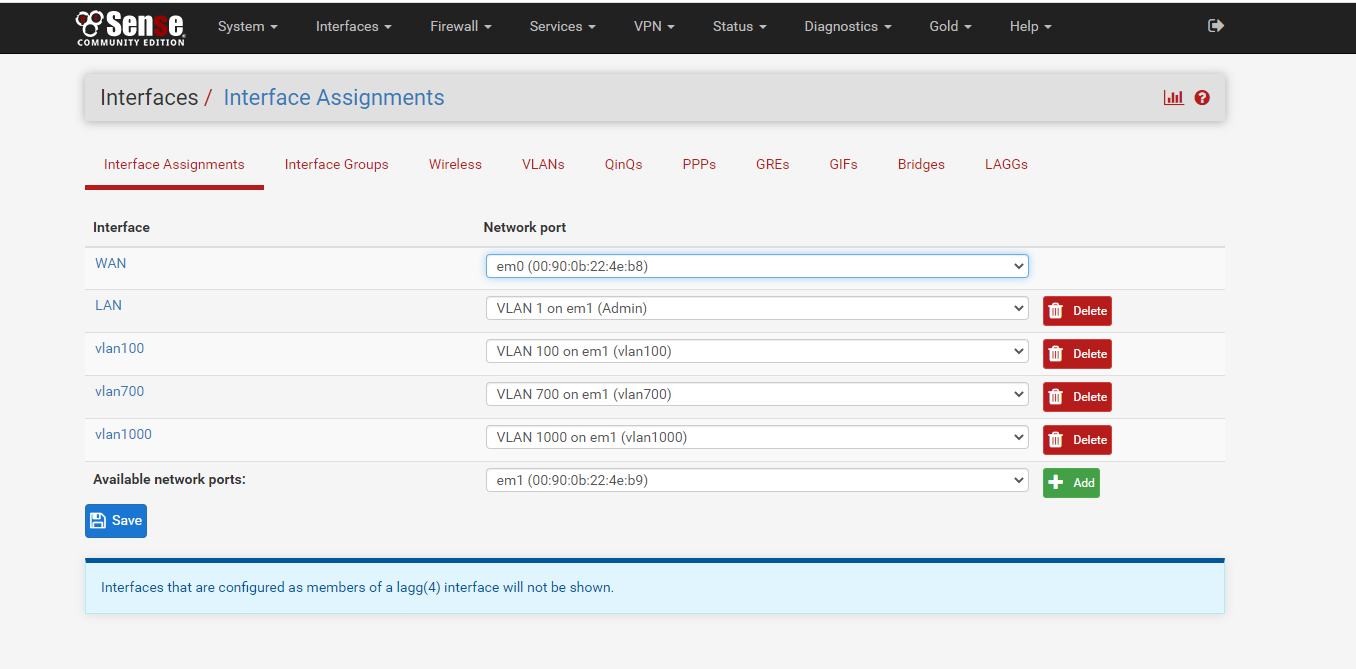
-
This is config that rep=lated, my 3750 switch is not IPBased, it allows to config IP address on VLAN port, but not on physical port, it can do static routing but not dynamic routing.
interface Loopback0
ip address 1.1.1.1 255.255.255.255interface Vlan1
description defaultvlan
ip address 10.30.54.254 255.255.255.0
ip helper-address 10.30.54.254
!
interface Vlan100
description WIRED
ip address 10.30.52.254 255.255.255.0
ip helper-address 1.1.1.1
!
interface Vlan700
description WirelessAccessPoints
ip address 10.30.58.254 255.255.254.0
ip helper-address 10.30.58.254
!
interface Vlan1000
description WirelessClients
ip address 10.30.60.254 255.255.254.0And my show version on Cisco:
LANA1#sh ver
Cisco IOS Software, C3750E Software (C3750E-UNIVERSALK9-M), Version 15.2(4)E10, RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2020 by Cisco Systems, Inc.
Compiled Tue 31-Mar-20 13:22 by prod_rel_team
License Level: lanbase
License Type: Permanent
Next reload license Level: lanbase.... ....
Switch Ports Model SW Version SW Image
- 1 54 WS-C3750X-48 15.2(4)E10 C3750E-UNIVERSALK9-M
-
You should upgrade, 2.3.4p1 is ancient! That's a 64bit capable box so there's no reason not to.
If you're running 32bit currently 2.3.5p2 is the most recent version you could upgrade to and that's also ancient at this point. Install 2.5.2 clean and restore your config if you have to.You should avoid using VLAN1 if at all possible:
https://docs.netgate.com/pfsense/en/latest/vlan/security.html#using-the-default-vlan1It should work though. The fact you are seeing nothing implies you are not sending VLAN tagged traffic to em1. That looks like a layer 3 switch with subnets defined. I expect it to be routing between those if so with pfSense not doing so.
What is the old switch? Is that just configured with VLANs? Layer2?Steve
-
@stephenw10 Thanks you Steve! The old switch is a L2 Linksys.
My problem was kind of solved for now. I might purchase a "Protectli Vault 4 Port, Firewall Micro Appliance/Mini PC - Intel Quad Core (Celeron J3160), AES-NI, Barebone" as new hardware and download a fresh pfSense copy to build a new firewall. My hardware might be too old to get upgraded.For networking issues, I have to remove all vlan from pfsense, and connect it to an access port of Cisco 3750(this 3750 is actually a lanbased license, so not a real L3 switch, it only supports IP address to be assigned to SVI, instead of physical ports).
then I have a default route from 3750 switch to the LAN port of pfsense.After I guild my new pfsense, I should change the design, make the Cisco a L2 switch and trunking to pfSense. let pfSense to do L3 routing, traffic control etc...
-
Yes, that sounds like what's happening. Of course with the switch routing between the VLANs pfSense never sees it and cannot filter it. It's significantly different to the previous network setup.
That Lanner is Atom D410 or D510. Not the fastest but either can run pfSense 2.5.2.
Steve