Deaf DHCP server on a VLAN
-
I have a VLAN setup in pfsense with it's own interface with DHCP running. It was working fine when I set it up a few weeks ago, but now doesn't. I've tried connecting with my laptop and listening with wireshark and I can see the DHCP requests and spanning tree messages from the switches, but there is no ACK. I must have screwed something up in my pfsense config.
Any suggestions for what I might have done? The firewall for that interface permits all.
pfsense 2.5.1
-
@zotan said in Deaf DHCP server on a VLAN:
The firewall for that interface permits all.
No matter the rules on the interface.. Once you enable dhcp server on an interface hidden rules are enabled that allow dhcp to work.
Did you sniff on pfsense via packet capture on the vlan interface via the diagnostic menu? If pfsense never sees the discover - then no it can not hand an offer for dhcp..
-
@johnpoz I'm just seeing ARP requests in packet capture
14:31:36.518886 ARP, Request who-has 192.168.30.90 tell 192.168.30.1, length 28I've realised that this is probably due to recent change in vlans. We have two internal networks at my office and to simplify cabling I setup vlans on the switches, so we now have nested vlans, which we didn't have before as this pfsense vlan will be encapsulated in the switch vlan. So this is probably a problem with the switch config rather than pfsense.
-
@zotan said in Deaf DHCP server on a VLAN:
have nested vlans, which we didn't have before
How exactly are you doing that? Q-in-Q I would assume?
https://docs.netgate.com/pfsense/en/latest/interfaces/qinq.htmlI would assume from that arp that 192.168.30.1 is pfsense? He is arping for that .90 address - and take it he never got an answer.. So yeah you have disconnect in pfsense actually talking to this vlan that your using for 192.168.30
Without the details of exactly what your doing, not sure why you would need to nest or tag inside a tag for a office? Is this some campus network with limitations on how the different parts of the campus are connected. If this is some single office building - I am confused at why you would want/need to run nested/stacked vlans?
-
@johnpoz We have two buildings connected by a point to point link. Each building has its own interface on the firewall, but to reduce cabling I have vlans in the switches in building A to get to the link on the roof. It's not obvious if Ubiquiti support this or how.
So I'm going to go for plan B and just create the vlan at building B and not manage it with pfsense.
Thanks.
-
Unifi doesn't support qinq from my understanding, and quick google shows people asking for it like 4 some years ago.. But have not seen anything that it has been added..
Not sure about the rest of your network - but the whole point of qinq is passing vlan into to another site where the connections between site does not have the ability to trunk the vlans across.
So still if unifi is your p2p - not sure why you can't just pass the tags over that link?
https://help.ui.com/hc/en-us/articles/204952204#2
This section demonstrates how to pass management traffic as "untagged" and leave VLAN traffic "tagged", or more simply, pass traffic transparently through the airMAX radio. -
@johnpoz I'm not a Unifi expert but it looks like their switches do support qinq. All of the negative google hits I found on the subject were for their edge routers, not the switches. The Ubiquiti UI and the docs aren't great, but I now have a port profile setup that looks very much like qinq. Mysteriously the system has started working today, even though I haven't changed anything, the port profiles have been set for a while. The only thing that happened today was a hard power cycle of the wireless link between the buildings. So it looks like the wireless link was dropping the tagged traffic. I'll leave it be for a while to see if anymore gremlins present themselves.
-
@zotan said in Deaf DHCP server on a VLAN:
but I now have a port profile setup that looks very much like qinq
Lets see this please.
-
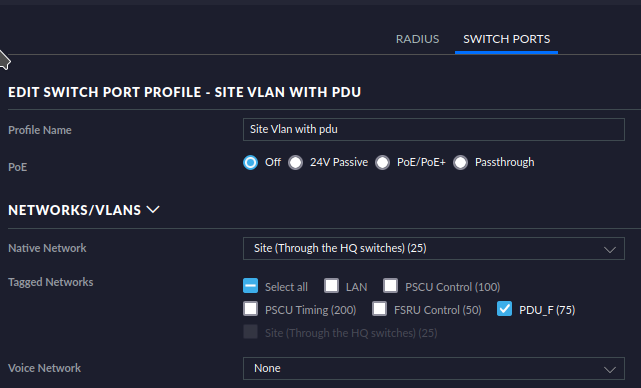
-
That is just allowing native untagged 25, and tagged 75... If you are hiding other vlans inside that 75 via qinq - not sure how unifi switch are going to see those or unpack them.. What is packing them into what amounts to the tunnel? vlan 75?
So what other vlan ID are you sending inside that 75? And what device is unpacking them?
Is that traffic then being sent to something that actually understands qinq?
Say you had pfsense -- switch -- wifi bridge -- switch -- pfsense
Then sure if pfsense send traffic to the switch with vlan 75 as the outside tag, and that is sent through the bridge over 75. And then the other pfsense gets that vlan 75 traffic, and understand its suppose to look inside there for the other tags.. That would work - as long as you do not strip the out 75 tag.
-
Ah, it looks like I have misunderstood this. I had thought setting native network to 25 would mean that all traffic on that port would get tagged or stripped with 25, a behaviour I understand as access. So if any traffic was already tagged it would then become qinq. Am I right to think that the switch is clever enough to split untagged and tagged and operated as access on the untagged and trunk on the tagged? So 25 and 75 appear as distinct vlans rather than nested?
-
@zotan said in Deaf DHCP server on a VLAN:
So 25 and 75 appear as distinct vlans rather than nested?
Yeah any switch does that - any switch that does vlans understands tagged vs untagged. You can always have 1 untagged vlan (native). If you want..