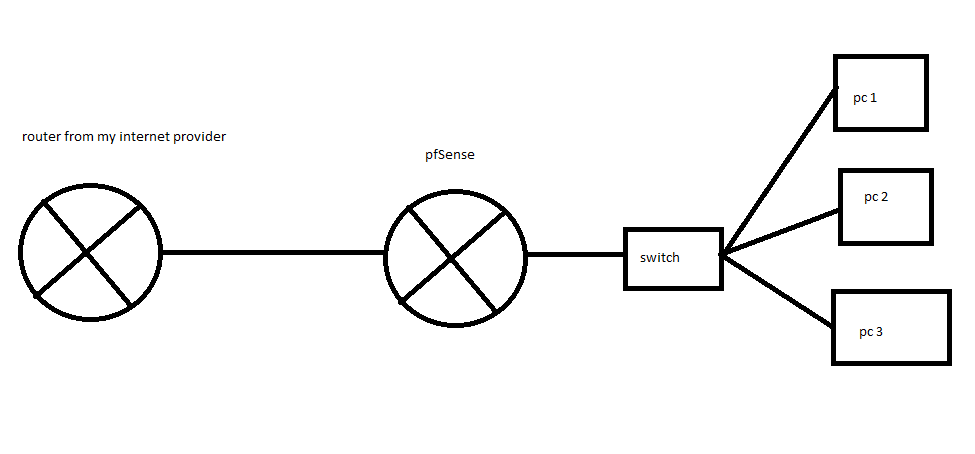
Get public ip for pcs
-
@s_serra no its not fine - I am not actually getting an answer to my ping - even though you show the reply going out the wan - I am not getting the reply.
-
@johnpoz
where is this blocking?do you want access to my pfsense to check? (I sent the info in pm)
I maybe did something wrong in pfsense -
Check the MAC addresses on those ping packets. Is it actually going to the right place?
-
@stephenw10 I don't know how to do this hahaha. Im noob
-
In the Diag > Packet Capture screen set the 'Level of detail' to Full.
Then click 'View Capture' to update what's shown.
You can then see the MACs and make sure packets are actually going between the devices you think they are.For example:
00:29:12.837882 00:e0:ed:86:a6:8c > 00:08:a2:0c:c9:91, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 51234, offset 0, flags [none], proto ICMP (1), length 29) 172.21.16.207 > 172.21.16.1: ICMP echo request, id 55661, seq 258, length 9 00:29:12.838102 00:08:a2:0c:c9:91 > 00:e0:ed:86:a6:8c, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 54674, offset 0, flags [none], proto ICMP (1), length 29) 172.21.16.1 > 172.21.16.207: ICMP echo reply, id 55661, seq 258, length 9 -
23:37:21.295167 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 154: (tos 0x10, ttl 62, id 24451, offset 0, flags [DF], proto TCP (6), length 140) 176.79.25.173.55677 > 176.79.20.129.443: Flags [P.], cksum 0x20c7 (correct), seq 516543103:516543191, ack 775950643, win 6763, options [nop,nop,TS val 2340705962 ecr 3038722538], length 88 23:37:21.295223 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52, bad cksum 0 (->abf7)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x8ef3 (incorrect -> 0x07f4), seq 1, ack 88, win 514, options [nop,nop,TS val 3038722655 ecr 2340705962], length 0 23:37:21.297282 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 155: (tos 0x10, ttl 62, id 24452, offset 0, flags [DF], proto TCP (6), length 141) 176.79.25.173.55677 > 176.79.20.129.443: Flags [P.], cksum 0xa9ed (correct), seq 88:177, ack 1, win 6763, options [nop,nop,TS val 2340705963 ecr 3038722538], length 89 23:37:21.297304 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52, bad cksum 0 (->abf7)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x8ef3 (incorrect -> 0x0798), seq 1, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 0 23:37:21.297338 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xd74c), seq 1:1449, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297355 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x7dea), seq 1449:2897, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297366 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x9c60), seq 2897:4345, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297375 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xef52), seq 4345:5793, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297386 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xc407), seq 5793:7241, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297401 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xf3b3), seq 7241:8689, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297410 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xecaa), seq 8689:10137, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297420 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x92b7), seq 10137:11585, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297429 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x919e), seq 11585:13033, ack 177, win 514, options [nop,nop,TS val 3038722657 ecr 2340705963], length 1448 23:37:21.297582 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 160: (tos 0x10, ttl 62, id 24453, offset 0, flags [DF], proto TCP (6), length 146) 176.79.25.173.55677 > 176.79.20.129.443: Flags [P.], cksum 0xfdfc (correct), seq 177:271, ack 1, win 6763, options [nop,nop,TS val 2340705964 ecr 3038722538], length 94 23:37:21.297605 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 135: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 121, bad cksum 0 (->abb2)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x8f38 (incorrect -> 0xe1f2), seq 13033:13102, ack 271, win 514, options [nop,nop,TS val 3038722657 ecr 2340705964], length 69 23:37:21.297682 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 140: (tos 0x10, ttl 62, id 24454, offset 0, flags [DF], proto TCP (6), length 126) 176.79.25.173.55677 > 176.79.20.129.443: Flags [P.], cksum 0xa3b2 (correct), seq 271:345, ack 1, win 6763, options [nop,nop,TS val 2340705964 ecr 3038722655], length 74 23:37:21.297701 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52, bad cksum 0 (->abf7)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x8ef3 (incorrect -> 0xd3c1), seq 13102, ack 345, win 514, options [nop,nop,TS val 3038722657 ecr 2340705964], length 0 23:37:21.305489 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24455, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xe8d7 (correct), seq 345, ack 1449, win 6763, options [nop,nop,TS val 2340705970 ecr 3038722657], length 0 23:37:21.305519 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x1848), seq 13102:14550, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.305531 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xd516), seq 14550:15998, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.305634 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24456, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xe32f (correct), seq 345, ack 2897, win 6763, options [nop,nop,TS val 2340705970 ecr 3038722657], length 0 23:37:21.305659 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x1740), seq 15998:17446, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.305670 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x411e), seq 17446:18894, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.305883 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24457, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xdd87 (correct), seq 345, ack 4345, win 6763, options [nop,nop,TS val 2340705970 ecr 3038722657], length 0 23:37:21.305909 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xcb1c), seq 18894:20342, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.305921 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x968f), seq 20342:21790, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.305926 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24458, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xd7df (correct), seq 345, ack 5793, win 6763, options [nop,nop,TS val 2340705970 ecr 3038722657], length 0 23:37:21.305949 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xc1b3), seq 21790:23238, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.305960 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x8ff9), seq 23238:24686, ack 345, win 514, options [nop,nop,TS val 3038722666 ecr 2340705970], length 1448 23:37:21.308497 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 321: (tos 0x0, ttl 128, id 34921, offset 0, flags [DF], proto TCP (6), length 307) 176.79.28.4.53037 > 84.17.62.9.443: Flags [P.], cksum 0x11b4 (correct), seq 2263739073:2263739340, ack 2840037557, win 1022, length 267 23:37:21.310607 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24459, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xcc8a (correct), seq 345, ack 8689, win 6763, options [nop,nop,TS val 2340705975 ecr 3038722657], length 0 23:37:21.310633 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0x1f3a), seq 24686:26134, ack 345, win 514, options [nop,nop,TS val 3038722671 ecr 2340705975], length 1448 23:37:21.310644 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 1514: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 1500, bad cksum 0 (->a64f)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [.], cksum 0x949b (incorrect -> 0xfd51), seq 26134:27582, ack 345, win 514, options [nop,nop,TS val 3038722671 ecr 2340705975], length 1448 23:37:21.310654 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 337: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 323, bad cksum 0 (->aae8)!) 176.79.20.129.443 > 176.79.25.173.55677: Flags [P.], cksum 0x9002 (incorrect -> 0x1d6c), seq 27582:27853, ack 345, win 514, options [nop,nop,TS val 3038722671 ecr 2340705975], length 271 23:37:21.310658 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24460, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xc13a (correct), seq 345, ack 11585, win 6763, options [nop,nop,TS val 2340705975 ecr 3038722657], length 0 23:37:21.310985 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24461, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xbb4d (correct), seq 345, ack 13102, win 6763, options [nop,nop,TS val 2340705975 ecr 3038722657], length 0 23:37:21.315711 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24462, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xafed (correct), seq 345, ack 15998, win 6763, options [nop,nop,TS val 2340705982 ecr 3038722666], length 0 23:37:21.315730 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24463, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0xa49d (correct), seq 345, ack 18894, win 6763, options [nop,nop,TS val 2340705982 ecr 3038722666], length 0 23:37:21.317816 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24464, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0x994b (correct), seq 345, ack 21790, win 6763, options [nop,nop,TS val 2340705984 ecr 3038722666], length 0 23:37:21.318946 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24465, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0x8dfa (correct), seq 345, ack 24686, win 6763, options [nop,nop,TS val 2340705985 ecr 3038722666], length 0 23:37:21.321426 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24466, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0x82a2 (correct), seq 345, ack 27582, win 6763, options [nop,nop,TS val 2340705988 ecr 3038722671], length 0 23:37:21.322671 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 66: (tos 0x10, ttl 62, id 24467, offset 0, flags [DF], proto TCP (6), length 52) 176.79.25.173.55677 > 176.79.20.129.443: Flags [.], cksum 0x8192 (correct), seq 345, ack 27853, win 6763, options [nop,nop,TS val 2340705989 ecr 3038722671], length 0 23:37:21.324251 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 59, id 16056, offset 0, flags [DF], proto TCP (6), length 40) 84.17.62.9.443 > 176.79.28.4.53037: Flags [.], cksum 0xb646 (correct), seq 1, ack 267, win 9600, length 0 23:37:21.347205 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 90: (tos 0xb8, ttl 64, id 34918, offset 0, flags [none], proto UDP (17), length 76, bad cksum 0 (->c725)!) 176.79.20.129.123 > 193.136.164.4.123: [bad udp cksum 0x2aa7 -> 0x2847!] NTPv4, length 48 Client, Leap indicator: (0), Stratum 3 (secondary reference), poll 8 (256s), precision -22 Root Delay: 0.008255, Root dispersion: 0.009216, Reference-ID: 193.136.164.4 Reference Timestamp: 3840737706.338833359 (2021/09/15 23:35:06) Originator Timestamp: 3840737706.335471153 (2021/09/15 23:35:06) Receive Timestamp: 3840737706.338833359 (2021/09/15 23:35:06) Transmit Timestamp: 3840737841.347154491 (2021/09/15 23:37:21) Originator - Receive Timestamp: +0.003362206 Originator - Transmit Timestamp: +135.011683338 23:37:21.354704 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 90: (tos 0x0, ttl 52, id 31621, offset 0, flags [DF], proto UDP (17), length 76) 193.136.164.4.123 > 176.79.20.129.123: [udp sum ok] NTPv4, length 48 Server, Leap indicator: (0), Stratum 2 (secondary reference), poll 8 (256s), precision -29 Root Delay: 0.000823, Root dispersion: 0.000000, Reference-ID: 56.99.239.27 Reference Timestamp: 3840732743.990608215 (2021/09/15 22:12:23) Originator Timestamp: 3840737841.347154491 (2021/09/15 23:37:21) Receive Timestamp: 3840737841.351331233 (2021/09/15 23:37:21) Transmit Timestamp: 3840737841.351333141 (2021/09/15 23:37:21) Originator - Receive Timestamp: +0.004176742 Originator - Transmit Timestamp: +0.004178649 23:37:21.496136 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 25166, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->8f71)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3602, length 9 23:37:21.497000 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 25166, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3602, length 9 23:37:21.878114 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 150: (tos 0x0, ttl 114, id 29143, offset 0, flags [none], proto UDP (17), length 136) 109.95.46.1.27062 > 176.79.28.4.6881: [udp sum ok] UDP, length 108 23:37:21.878450 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 354: (tos 0x0, ttl 128, id 8018, offset 0, flags [none], proto UDP (17), length 340, bad cksum 0 (->b293)!) 176.79.28.4.6881 > 109.95.46.1.27062: [udp sum ok] UDP, length 312 23:37:22.028383 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 45925, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->3e5a)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3603, length 9 23:37:22.029281 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 45925, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3603, length 9 23:37:22.560644 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 27759, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->8550)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3604, length 9 23:37:22.561560 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 27759, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3604, length 9 23:37:23.091141 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 2348, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->e893)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3605, length 9 23:37:23.092070 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 2348, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3605, length 9 23:37:23.210903 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 139: (tos 0x0, ttl 42, id 9415, offset 0, flags [DF], proto UDP (17), length 125) 67.220.57.5.1175 > 176.79.28.4.6881: [udp sum ok] UDP, length 97 23:37:23.211138 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 353: (tos 0x0, ttl 128, id 38521, offset 0, flags [none], proto UDP (17), length 339, bad cksum 0 (->59ec)!) 176.79.28.4.6881 > 67.220.57.5.1175: [udp sum ok] UDP, length 311 23:37:23.238495 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 143: (tos 0x0, ttl 45, id 0, offset 0, flags [DF], proto UDP (17), length 129) 144.139.56.188.6881 > 176.79.28.4.6881: [udp sum ok] UDP, length 101 23:37:23.238704 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 338: (tos 0x0, ttl 128, id 37954, offset 0, flags [none], proto UDP (17), length 324, bad cksum 0 (->fcc)!) 176.79.28.4.6881 > 144.139.56.188.6881: [udp sum ok] UDP, length 296 23:37:23.297889 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 145: (tos 0x0, ttl 42, id 48643, offset 0, flags [none], proto UDP (17), length 131) 24.10.2.243.21942 > 176.79.28.4.6881: [udp sum ok] UDP, length 103 23:37:23.298079 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 341: (tos 0x0, ttl 128, id 17677, offset 0, flags [none], proto UDP (17), length 327, bad cksum 0 (->d49)!) 176.79.28.4.6881 > 24.10.2.243.21942: [udp sum ok] UDP, length 299 23:37:23.616130 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 58093, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->ed2)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3606, length 9 23:37:23.617098 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 58093, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3606, length 9 23:37:23.756271 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 273: (tos 0x0, ttl 59, id 41154, offset 0, flags [DF], proto TCP (6), length 259) 162.159.135.234.443 > 176.79.28.4.63874: Flags [P.], cksum 0xe106 (correct), seq 3521997435:3521997654, ack 478704296, win 72, length 219 23:37:23.796814 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 128, id 57743, offset 0, flags [DF], proto TCP (6), length 40) 176.79.28.4.63874 > 162.159.135.234.443: Flags [.], cksum 0xed43 (correct), seq 1, ack 219, win 1025, length 0 23:37:23.989424 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 139: (tos 0x0, ttl 55, id 20059, offset 0, flags [DF], proto UDP (17), length 125) 5.189.187.90.6954 > 176.79.28.4.6881: [udp sum ok] UDP, length 97 23:37:23.989707 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 353: (tos 0x0, ttl 128, id 8035, offset 0, flags [none], proto UDP (17), length 339, bad cksum 0 (->8ccc)!) 176.79.28.4.6881 > 5.189.187.90.6954: [udp sum ok] UDP, length 311 23:37:24.127310 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 247, id 25057, offset 0, flags [none], proto TCP (6), length 40) 79.124.62.98.8080 > 176.79.20.129.9121: Flags [S], cksum 0x2f61 (correct), seq 2413844161, win 1024, length 0 23:37:24.146133 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 48232, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->3557)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3607, length 9 23:37:24.147082 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 48232, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3607, length 9 23:37:24.328114 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 270: (tos 0x0, ttl 123, id 6969, offset 0, flags [none], proto UDP (17), length 256) 155.133.246.35.27025 > 176.79.28.4.65075: [udp sum ok] UDP, length 228 23:37:24.428229 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 270: (tos 0x0, ttl 123, id 6970, offset 0, flags [none], proto UDP (17), length 256) 155.133.246.35.27025 > 176.79.28.4.65075: [udp sum ok] UDP, length 228 23:37:24.673462 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 291, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->f09c)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3608, length 9 23:37:24.674268 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 291, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3608, length 9 23:37:24.683235 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 95: (tos 0x0, ttl 128, id 34922, offset 0, flags [DF], proto TCP (6), length 81) 176.79.28.4.53037 > 84.17.62.9.443: Flags [P.], cksum 0x6bfa (correct), seq 267:308, ack 1, win 1022, length 41 23:37:24.694321 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 128, id 24643, offset 0, flags [none], proto UDP (17), length 64) 176.79.28.4.65075 > 155.133.246.35.27025: [udp sum ok] UDP, length 36 23:37:24.698934 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 59, id 16057, offset 0, flags [DF], proto TCP (6), length 40) 84.17.62.9.443 > 176.79.28.4.53037: Flags [.], cksum 0xb61d (correct), seq 1, ack 308, win 9600, length 0 23:37:24.726050 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 95: (tos 0x0, ttl 128, id 34923, offset 0, flags [DF], proto TCP (6), length 81) 176.79.28.4.53037 > 84.17.62.9.443: Flags [P.], cksum 0x96aa (correct), seq 308:349, ack 1, win 1022, length 41 23:37:24.741728 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 59, id 16058, offset 0, flags [DF], proto TCP (6), length 40) 84.17.62.9.443 > 176.79.28.4.53037: Flags [.], cksum 0xb5f4 (correct), seq 1, ack 349, win 9600, length 0 23:37:24.777729 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 171: (tos 0x0, ttl 59, id 41155, offset 0, flags [DF], proto TCP (6), length 157) 162.159.135.234.443 > 176.79.28.4.63874: Flags [P.], cksum 0x4b7a (correct), seq 219:336, ack 1, win 72, length 117 23:37:24.818329 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 128, id 57744, offset 0, flags [DF], proto TCP (6), length 40) 176.79.28.4.63874 > 162.159.135.234.443: Flags [.], cksum 0xecce (correct), seq 1, ack 336, win 1025, length 0 23:37:25.043048 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 126: (tos 0x0, ttl 128, id 24644, offset 0, flags [none], proto UDP (17), length 112) 176.79.28.4.65075 > 155.133.246.35.27025: [udp sum ok] UDP, length 84 23:37:25.108970 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 246, id 19566, offset 0, flags [none], proto TCP (6), length 40) 79.124.62.74.8080 > 176.79.20.129.3477: Flags [S], cksum 0x5fd3 (correct), seq 1993954682, win 1024, length 0 23:37:25.202132 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 11663, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->c430)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3609, length 9 23:37:25.203117 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 11663, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3609, length 9 23:37:25.247383 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 258: (tos 0x0, ttl 59, id 41156, offset 0, flags [DF], proto TCP (6), length 244) 162.159.135.234.443 > 176.79.28.4.63874: Flags [P.], cksum 0x7810 (correct), seq 336:540, ack 1, win 72, length 204 23:37:25.287102 00:d8:61:4e:46:10 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 128, id 57745, offset 0, flags [DF], proto TCP (6), length 40) 176.79.28.4.63874 > 162.159.135.234.443: Flags [.], cksum 0xec03 (correct), seq 1, ack 540, win 1024, length 0 23:37:25.732152 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 43: (tos 0x0, ttl 64, id 60238, offset 0, flags [none], proto ICMP (1), length 29, bad cksum 0 (->671)!) 176.79.20.129 > 176.79.20.1: ICMP echo request, id 34431, seq 3610, length 9 23:37:25.733086 00:03:fa:00:00:01 > 00:e2:69:43:3d:a8, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 60238, offset 0, flags [none], proto ICMP (1), length 29) 176.79.20.1 > 176.79.20.129: ICMP echo reply, id 34431, seq 3610, length 9 23:37:25.757968 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 146: (tos 0x0, ttl 128, id 17678, offset 0, flags [none], proto UDP (17), length 132, bad cksum 0 (->e0b)!) 176.79.28.4.6881 > 24.10.2.243.21942: [udp sum ok] UDP, length 104 23:37:26.049981 00:03:fa:00:00:01 > 00:d8:61:4e:46:10, ethertype IPv4 (0x0800), length 145: (tos 0x0, ttl 113, id 7318, offset 0, flags [none], proto UDP (17), length 131) 79.132.81.171.53428 > 176.79.28.4.6881: [udp sum ok] UDP, length 103 23:37:26.050212 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 341: (tos 0x0, ttl 128, id 64799, offset 0, flags [none], proto UDP (17), length 327, bad cksum 0 (->cf03)!) 176.79.28.4.6881 > 79.132.81.171.53428: [udp sum ok] UDP, length 299 -
There is no traffic to or from .208 there. Did the server IP change?
Really we want to see a capture of something failing when it tries to connect to the server. And only that, so filter by the external IP you're connecting from to remove all the the traffic.
Steve
-
79.124.62.98.8080 > 176.79.22.208.9555: Flags [S], cksum 0xdf92 (correct), seq 1968946451, win 1024, length 0 00:04:17.625248 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40, bad cksum 0 (->e5d2)!) 176.79.22.208.9555 > 79.124.62.98.8080: Flags [R.], cksum 0xe37f (correct), seq 0, ack 1968946452, win 0, length 0 00:04:22.741602 08:00:27:ed:96:55 > 00:03:fa:00:00:01, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 176.79.22.1 tell 176.79.22.208, length 46 00:04:22.742483 00:03:fa:00:00:01 > 08:00:27:ed:96:55, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Reply 176.79.22.1 is-at 00:03:fa:00:00:01, length 46 00:04:26.657923 00:03:fa:00:00:01 > 08:00:27:ed:96:55, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 247, id 41561, offset 0, flags [none], proto TCP (6), length 40) 79.124.62.98.8080 > 176.79.22.208.41109: Flags [S], cksum 0xf784 (correct), seq 2334004252, win 1024, length 0 00:04:26.658141 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40, bad cksum 0 (->e5d2)!) 176.79.22.208.41109 > 79.124.62.98.8080: Flags [R.], cksum 0xfb71 (correct), seq 0, ack 2334004253, win 0, length 0 00:04:30.270828 00:03:fa:00:00:01 > 08:00:27:ed:96:55, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 247, id 16175, offset 0, flags [none], proto TCP (6), length 40) 79.124.62.74.8080 > 176.79.22.208.2227: Flags [S], cksum 0x9731 (correct), seq 1983652172, win 1024, length 0 00:04:30.271106 00:e2:69:43:3d:a8 > 00:03:fa:00:00:01, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40, bad cksum 0 (->e5ea)!) 176.79.22.208.2227 > 79.124.62.74.8080: Flags [R.], cksum 0x9b1e (correct), seq 0, ack 1983652173, win 0, length 0 -
@s_serra said in Get public ip for pcs:
176.79.22.208.9555 > 79.124.62.98.8080: Flags [R.],
Well that is a RST.. .208 telling him to F off..
that traffic looks OFF.. Why would source traffic come from 8080 trying to do a syn to random ports?
-
Where exactly were you sniffing. I logged into your pfsense. And trying to ping your 22.208 address from MY ip.. I saw no traffic sniffing going to your wan for the 22.208 address.
-
@johnpoz I'm sorry but I went to sleep and turned off the computer. It's online now. When you can, you can test.
-
@johnpoz said in Get public ip for pcs:
Why would source traffic come from 8080 trying to do a syn to random ports?
I don't know hahaha
I have no control over this ip: 79.124.62.98
-
This post is deleted! -
Ok, well this was bizarre!
The root of the issue here was that the default 'reply-to' setting on the WAN firewall rule (because it's dhcp with a gateway) was somehow causing pf to send reply traffic using it's own MAC address. Which the ISP was likely legitimately dropping.
Disabling 'reply-to' allowed the traffic to pass without pf interfering.
Quite how that's possible is something we're looking at now.
If the bridge interface had the dhcp address and gateway on it and neither WAN or LAN have an address you would not not this though. That is the expected way to setup something like this.
Steve
-
@stephenw10 said in Get public ip for pcs:
Disabling 'reply-to' allowed the traffic to pass without pf interfering.
So your saying he is working now - because I am not able to ping that IP currently. Or you duplicated this in lab?
-
It is (was) working as expected for him but I think he disconnected the target and, hopefully, set some more restrictive rules.
-
@stephenw10 ah - ok, yeah he had sent me the login and that is no longer working. So glad its fixed and yeah hope set some more restrictive rules ;)
-
yes it was working I now turned off the server for testing and put stricter firewall rules. Thanks a lot for the help. I was never going to get there alone. Hahahaha
-
For future reference - could of spotted this problem right away by looking on the sniff when reply traffic went out the wan. Validating the mac address on the outgoing traffic.