Port 80 not forwarding
-
hey yall, I've been working to try and get my Nginx Proxy Manager working for a while now and I'm truly stuck.
I'm trying to port forward port 80 to port 8080 and 443 to 4443,
I have my settings properly configured and I attempted to go through the Port Forward Troubleshooting but everything that I could understand was correct.
Something weird must be blocking port 80 cause when I do a port check test it shows not open but port 443 does show open. IF someone could work with me and help me figure this mystery out that would be extremely awesome. -
@mr-traxson said in Port 80 not forwarding:
Something weird must be blocking port 80
Its quite possible for isp to block this... Simple test go to can you see me . org - do a port test of 80 while your sniffing on your wan for port 80.. Do you see this traffic hit your wan?
example..
Even though I don't have 80 forwarded to anything - can still see the traffic hit my wan.
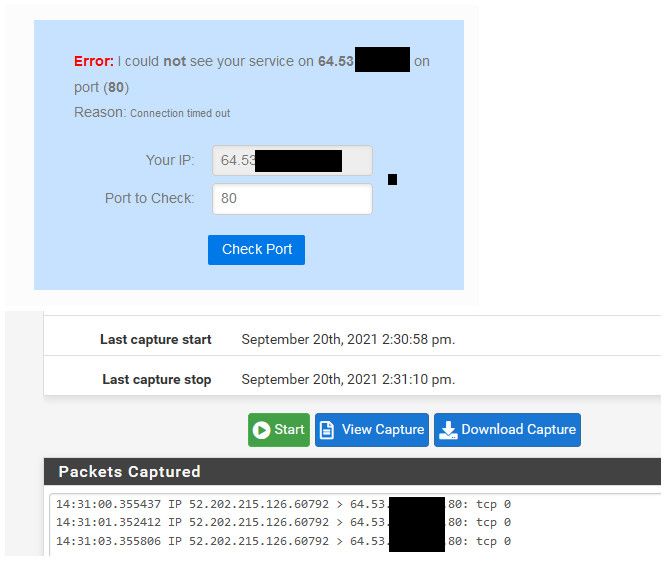
-
ive spoken with my ISP today actually and they confirmed that they do not block port 80
-
@mr-traxson said in Port 80 not forwarding:
ive spoken with my ISP today actually and they confirmed that they do not block port 80
Until you actually see the traffic hit pfsense wan - your isp can say whatever they want to say. It takes all of 10 seconds to validate.. You could validate its actually getting to pfsense wan IP in less time than it took you to dial the phone to call your isp ;)
Validation that pfsense is actually seeing the traffic you want it to forward, is always step one in troubleshooting an issue.
-
@johnpoz I'm sorry to hop into this thread, but I'm trying to accomplish the exact same thing, and am having the same trouble, except that I can't get either 80 or 443 to open.
I would like to do that test you mentioned, but I can't find the screen where you are watching the packet capture. I can get to the Firewall logs, but that doesn't seem to be what you were showing. -
@elmojo packet captures are done under the diagnostic menu, packet captures
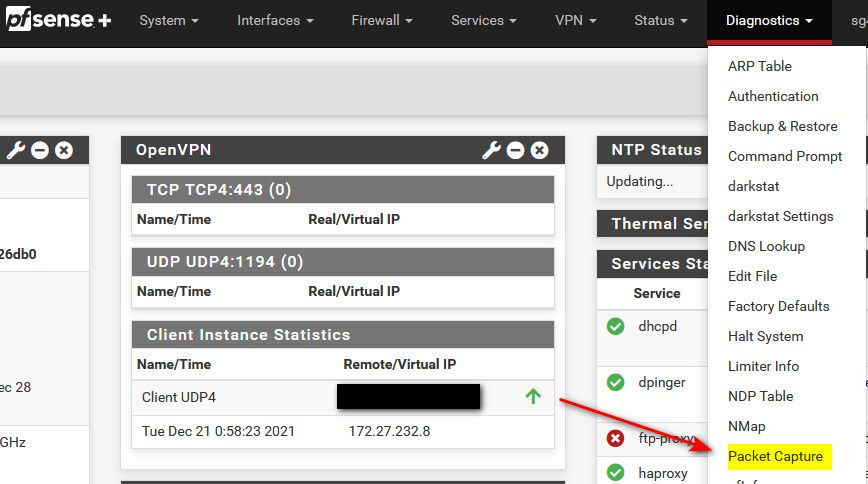
Make sure you pick the right interface, and the other stuff your looking for only if possible. Like port 443 or 80, when your doing that specific test.. And too say your wan IP.. Or the packet capture could grab all the traffic and get quite large very quickly to look through. And it default to only grabbing 100 packets.
So you might want/need to adjust that if there is going to be a lot of traffic your grabbing.
-
@johnpoz Got it, thanks!
One sec, let's see what happens...Well, that didn't go as I'd hoped.
Did I set it up right?
The result was "no capture file to display"Those ports are the ones I'm trying to forward. I only checked 80 during the sniff.
-
@elmojo yeah if you went to say "can you see me . org", and it shows that same public IP you put in there. And your not seeing it on your wan interface... You sure that 174 IP you put in there is your wan (you might want to hide that?) from your post.
I would just try port 80 if that is what your testing.. when you do multiple ports I think you need to use ; vs , -- but can you see me can only send 1 port at a time.. So best just to put in the 1 port your going to be testing.
But yeah if your not seeing the traffic hit your wan, pretty hard to forward it.. You sure your not going through say a vpn to get to can you see me - if so it would be sending the traffic to your vpn IP.. VPNs don't normally allow for inbound traffic, some do - but it manually has to be setup, and they sure and the hell wouldn't allow the standard 80 and 443 ports ;)
-
@johnpoz Good call, I forgot my IP was showing. lol
Yeah, that's definitely my public IP. I have a widget on my desktop that shows it all the time.
I tried again with just port 80 being sniffed, and I DO see it hitting my WAN IP, so yay?
What do I do now? I have the port(s) forwarded in pfsense, but they don't seem to be working.
At least I can't get any of them to flag as open using (can you see me) or (you get signal).
Any ideas?
I can post my NAT rules if it would help. -
@elmojo lets see your port forward setup and your wan rules. And do you have any rules in floating tab?
If your seeing 80 hit your wan, and you forwarded it correctly, the next check is to do the same packet capture, this time on your lan side interface your using to send the traffic to where you want it to go.. Do you see it?
If you do - then pfsense is doing its job, if you don't then something wrong with your port forwards.
Common mistake is forgetting the local host firewalls, for example windows machine might allow something from its own local network, but something from some other network - ie like the internet it would block. So you need to make sure the host firewall (if running) on where your forwarding allows the traffic.
Other issues is device your forwarding to is actually using pfsense as its gateway.. But the lan side sniff is way to validate your actually sending the traffic to where you want to send it.
-
@johnpoz Okay, let me see if I can follow all that... lol
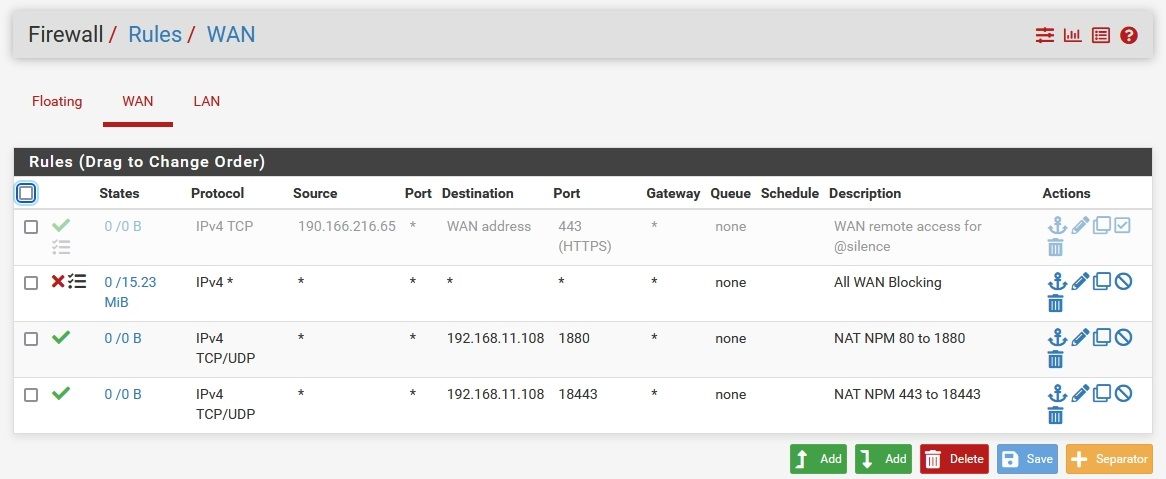
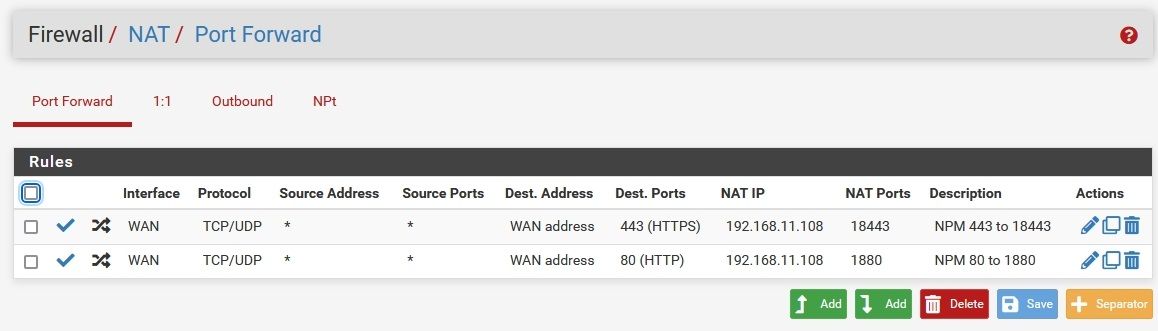
Here's my forward Rules and WAN rules. Nothing in Floating.
For the LAN capture, do I sniff the port I forwarded to (eg 1880) or the original port (80)?
For host firewall, I'm running all this in containers on an unRAID server, so there shouldn't be any other firewalls in place, to my knowledge. -
Okay, this is odd...
I did the capture, and tried both 80 and 1880, and got...nothing. A blank output.
How is that possible? Shouldn't it be either output or as before "no capture file to display"?
Something just occurred to me... If a port is forwarded to a specific internal IP (my server), then how will I check that port from another IP (my desktop)? It will always fail, right?
Maybe it's working, and I'm just not checking it from the right place? -
@elmojo said in Port 80 not forwarding:
Maybe it's working, and I'm just not checking it from the right place?
you need to check it from and external source!! for example "can you see me . org" take out the spaces in that name.
No you can not hit a port on your wan from a box internally and be forwarded back in.. That would be a nat reflection or loopback forward.. You would need to enable and setup nat reflection for those to work.
do I sniff the port I forwarded to (eg 1880) or the original port (80)?
If your redirecting from port 80 on your wan to 1880 on your lan, you would sniff on the 1880 port.
-
@johnpoz Ok, so I was doing it right then. I wasn't suggesting that I sniff the port from my local IP, I was just wondering if since the port forward is specific to a single IP on my LAN, if it would still show as open when I run the test on that site.
In that case, it's definitely not working. I've tried testing ports 80, 1880, 443, and 18443. None of them flag as open using either of the sites I've tried.
What's really weird is that if I restrict the sniff to only my WAN IP, and only port 18443, then run the capture for only the long enough for the port test to run (maybe 10 secs?), I get a long list of packets, both to and from my WAN IP, none of which are 18443. Some of them are port 443, but lots of them are some other random port, like 8812, or 52570. Any idea what's up with that?
I can post the output, but my IP is all through there and it would be a nightmare to obscure.------EDIT-----
OK, scratch that. If I sniff them one at a time, it looks a bit more reasonable. Checking port 80 or 1880, I get only a few captured packets, all incoming, all on the expected ports.
However, on port 443 I get all the crazy output as described above.
On port 18443, I get pretty much the same output as 443, but even more of it. I see hits on 443, but also lots of other random ports. None of them are 18443. How is that possible? -
@elmojo if your sniffing on 443 and your wan IP, you will see traffic in both directions where 443 is either source or destination, so you went to some website, that would be from your public IP and port 443 is in there as well.. So yeah you can see some other traffic.
Here, I will forward 80 external to 1880 internal with nothing listening on that port.. But it will show you how to validate pfsense is working..
First thing to check is that 80 is inbound from outside, the can you see me site.
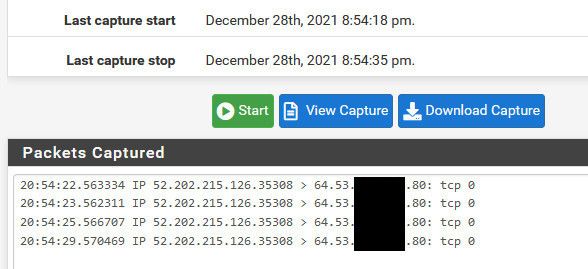
I limit the traffic to my IP by using the known source IP, 52.202.215.126 in my case with can you see me.
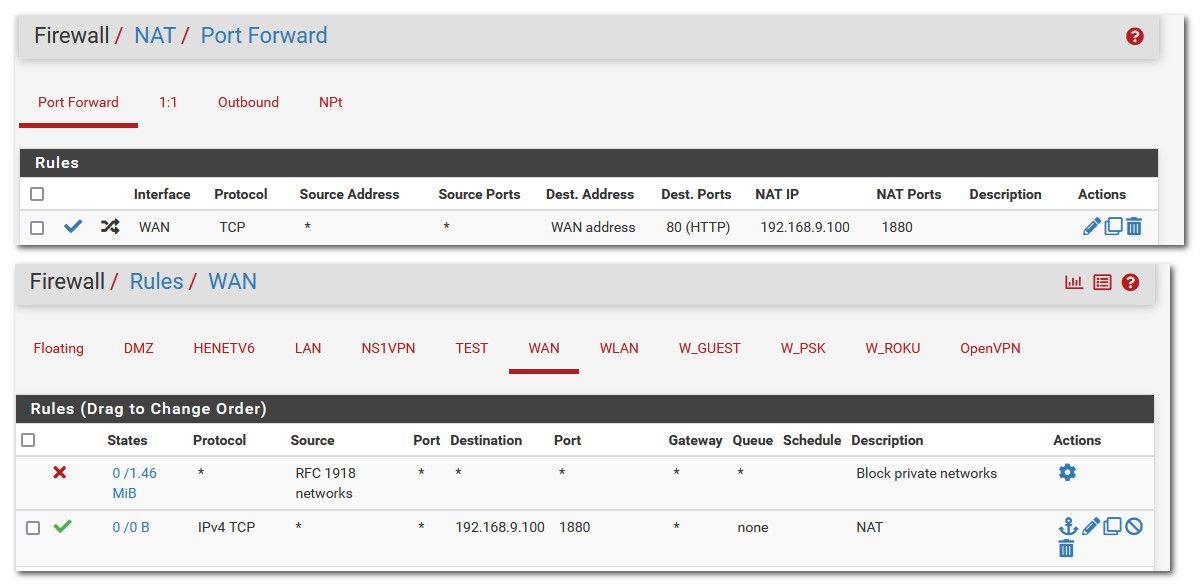
Now I setup my port forward rule, and you can see the firewall rule it created.
Now I sniff on my lan, for port 1880, and then run the test from can you see me again to port 80.
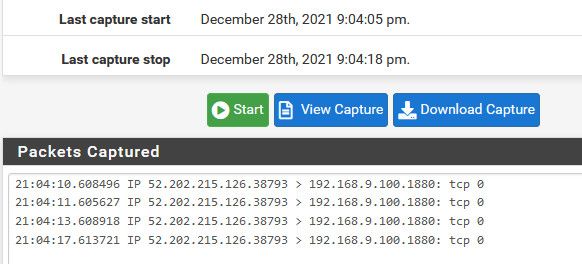
its that simple.
Why would you think you would see port 80 traffic on the lan, if your sending to 1880?
You don't need anything running anywhere to test if port forwards work on pfsense - what you need is an IP to send to, because if pfsense can not arp for that IP, then it can not forward to it..
How do you think any port forward would work with this rule
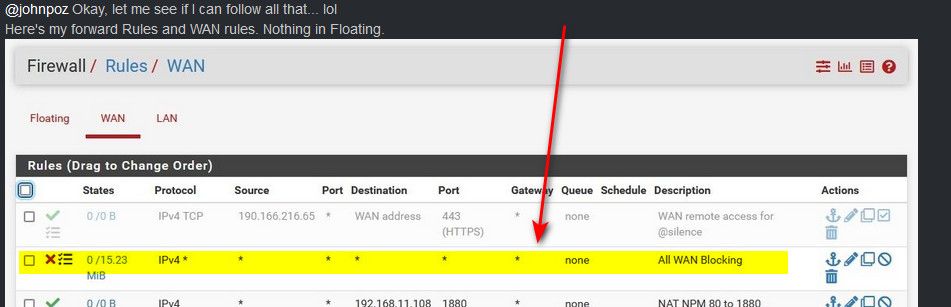
Rules are evaluated top down, first rule to trigger wins. You need to move your firewall rules for your ports above that block rule, or no they are never going to work because your firewall rule is blocking all inbound unsolicited traffic before it can get to the rule that allows your port forward. Should of spotted that right away :) hehehe Not sure how I missed it to be honest, maybe I thought it was just the block rfc1918 rule at first glance - DOH! But yeah that rule there is stopping any port forwards from ever working.
-
@johnpoz So mine is set up exactly as you show.
The "All WAN block" was set up by one of the mods here, so I didn't question it. I know very little about this stuff, I'm learning as I go, so I have to trust those with more experience than me. :)Let me go back and check everything and try the port checks and captures again...
Thanks for the excellent, very clear instructions, by the way. -
@elmojo you need to remove that rule - while you can sniff and see traffic on the wan with that rule, none of your port forwards would ever work with that rule on top like that.. You need to move your port forward rules above that.
If I had to "guess" to why such a rule would be placed, is you turned off logging of the default rule, and wanted to log your wan inbound traffic. It shows that its being logged with that little symbol there next to the red X.
Nothing wrong with having that rule there for logging blocked traffic, but you need to move stuff you want to allow above it.
With that rule in place - you should of seen block entries in your firewall log for when you tried to access port 80 or 443 from can you see me.
-
@johnpoz It was part of a massive troubleshooting effort to figure out why certain sites were being blocked for no reason. We finally got it sorted out, but I couldn't begin to tell you all the stuff they had me change.
I've moved that rule to the bottom of the stack.
Both ports 80 and 443 now test as open (yay!) but they are captured as 80 and 443, not 1880 and 18443. Per your example, shouldn't I be seeing the "forwarded" ports on the capture?
Just trying to learn the ropes here...---EDIT---
Oh wait, it's late and I'm an idiot. I didn't sniff the LAN. One sec.... -
@elmojo if your forwarding port 80 to 1880 then yes your sniff on your LAN would show 1880, on your WAN it would still be port 80.
For completeness - here is my wan rules, I have sim log rules at the bottom of my stack for tcp (syn only) that is the little gear you see on that rule. And then UDP ports that are of interest to me to see in my log.
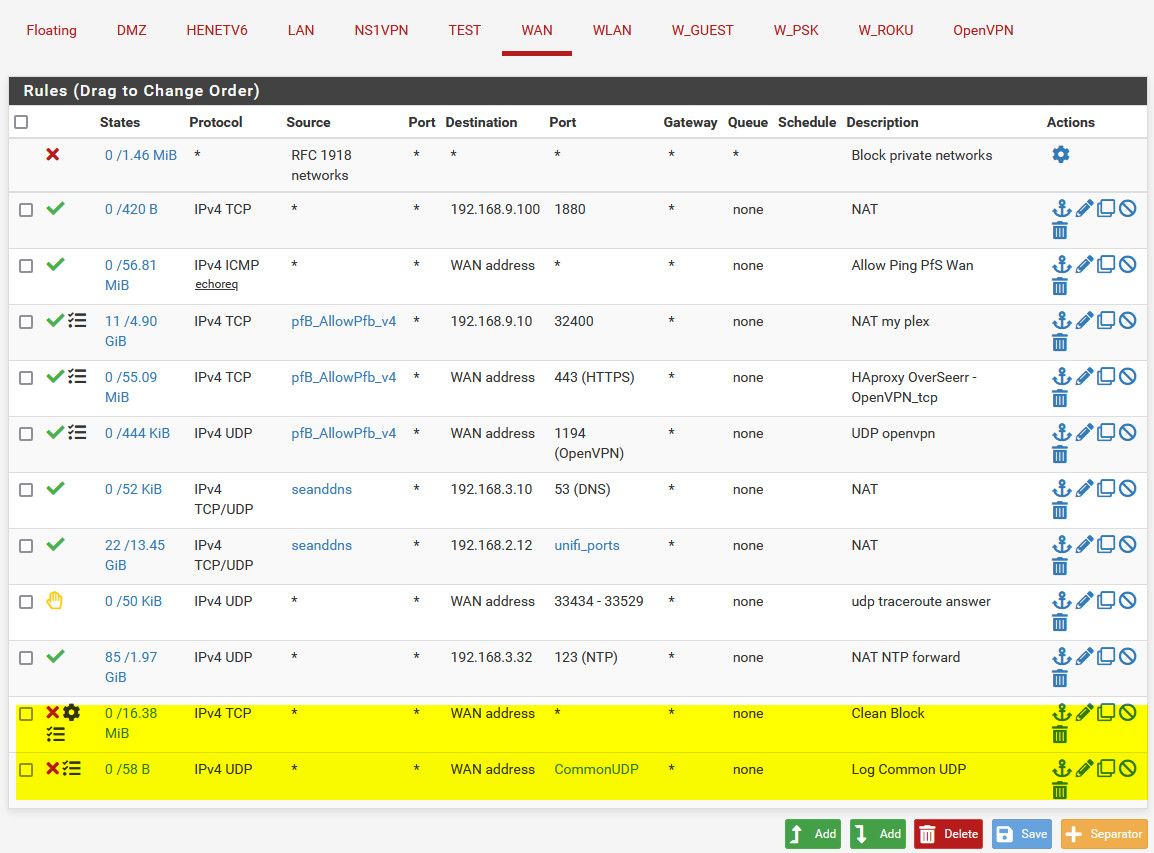
Notice the order of the rules, the Reject rule is there so traceroutes answer from the outside.
I moved the 1880 rule to the top just to make it easier to take the pic, it really could be anywhere in the stack as long as its above where I block all.
-
@johnpoz Cool, thanks for sharing that!
I'm getting there.
Still fuzzy on how to cap the packets on the LAN, I can't seem to get it to work.
When I set up the capture, I choose LAN, then what IP? Still external IP or the internal IP that the ports are forwarded to?
Then port 80, then start....
I've tried with both internal and external IP. Neither one gives any packet output.
I know I'm doing something simple wrong.