IPSEC speed issue - 2 Netgate Fws 7100 and 5100
-
Hello All,
Im configuring for the first time 2 Netgate fws for IPSEC. A 7100 in a customer office, and a 5100 in a remote office. According to specs on Netgates site, using AES-GCM-128 w/QAT, I should be able to get 500ish Mbps across the tunnel. Ive verified switch speed tests that non-vpn traffic cant exceed 800m in both locations, however with the tunnel established, I only seem to be able to get maybe 85m. Im not aiming for the full 500m, but id like to realistically do 200-300. I verified the hardware encryption is enabled on both sides, but I still dont seem to see any improvement. Any pointers at what im doing wrong? Ive been strictly using the GUI, so I dont know if theres any special CLI config I need to deal with.
Thank you.
-
Guess Im the only one to have this issue?
-
 J jimp locked this topic on
J jimp locked this topic on
-
 J jimp unlocked this topic on
J jimp unlocked this topic on
-
There shouldn't be any special CLI config but a few things to note:
- Make sure both ends have the QAT encryption module chosen under System > Advanced, Misc tab. Though if you are using AES-GCM then using AES-NI on both is good as well.
- Post your whole tunnel config for P1 and P2. Make sure you have only AES-GCM selected in P2 with no hash selected.
- Make sure the packets you are pushing do not get fragmented. This may also mean enabling MSS clamping for the VPN.
- Check how you are testing, always test through the firewall (e.g. LAN-to-LAN) and never test directly to either firewall endpoint, especially when dealing with encrypted traffic.
- Ensure your testing methodology is comparable to the traffic you want to push. For example if you are wanting to test large file transfers, use large packets and not small frames during a test, and vice versa. A test with many small packets will have a high PPS rate and low total throughput while a test with large packets will have high throughput and lower PPS. IMIX tests will be in between, but closer to large packets.
There is some more general advice on https://docs.netgate.com/pfsense/en/latest/vpn/performance.html
-
@jimp
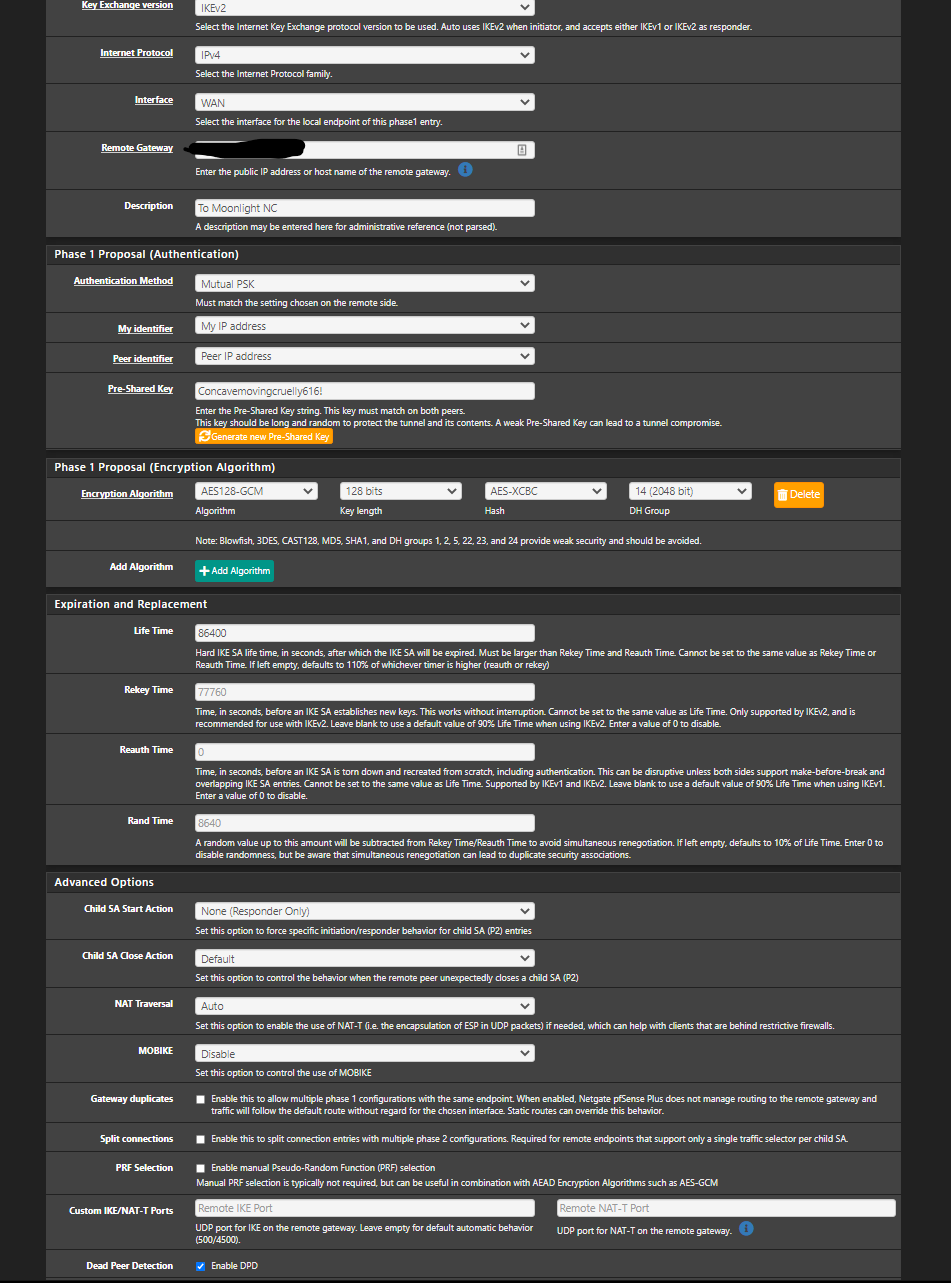
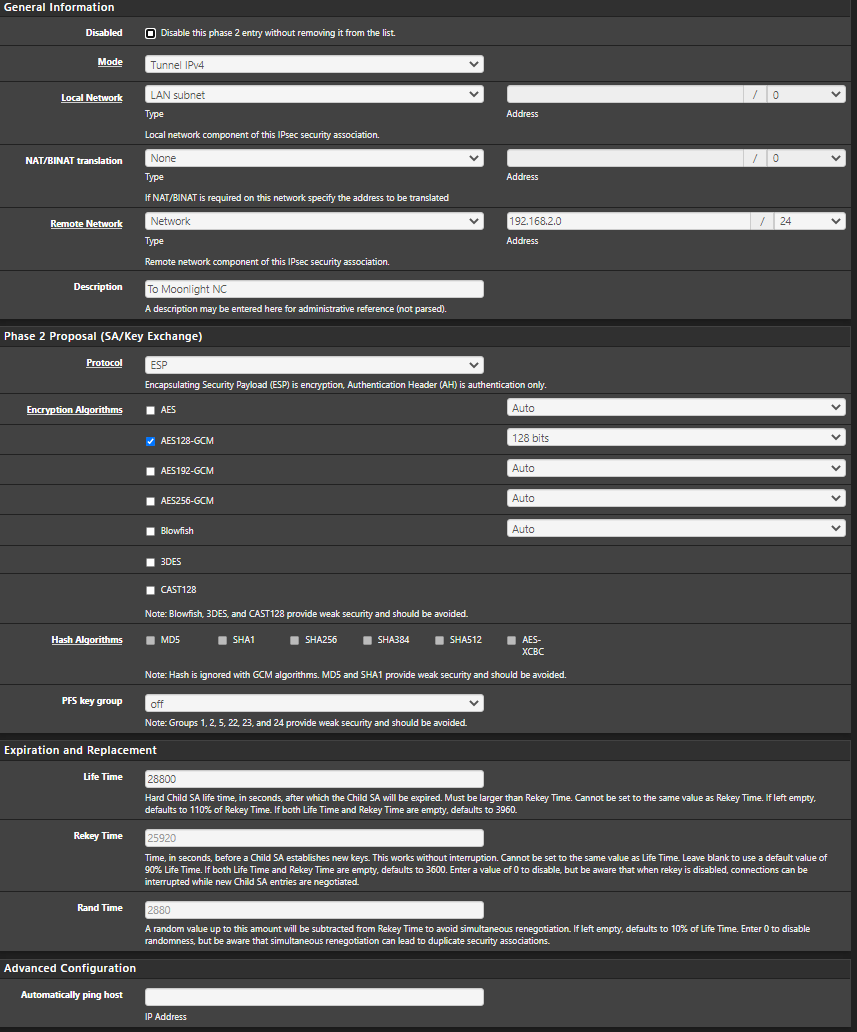
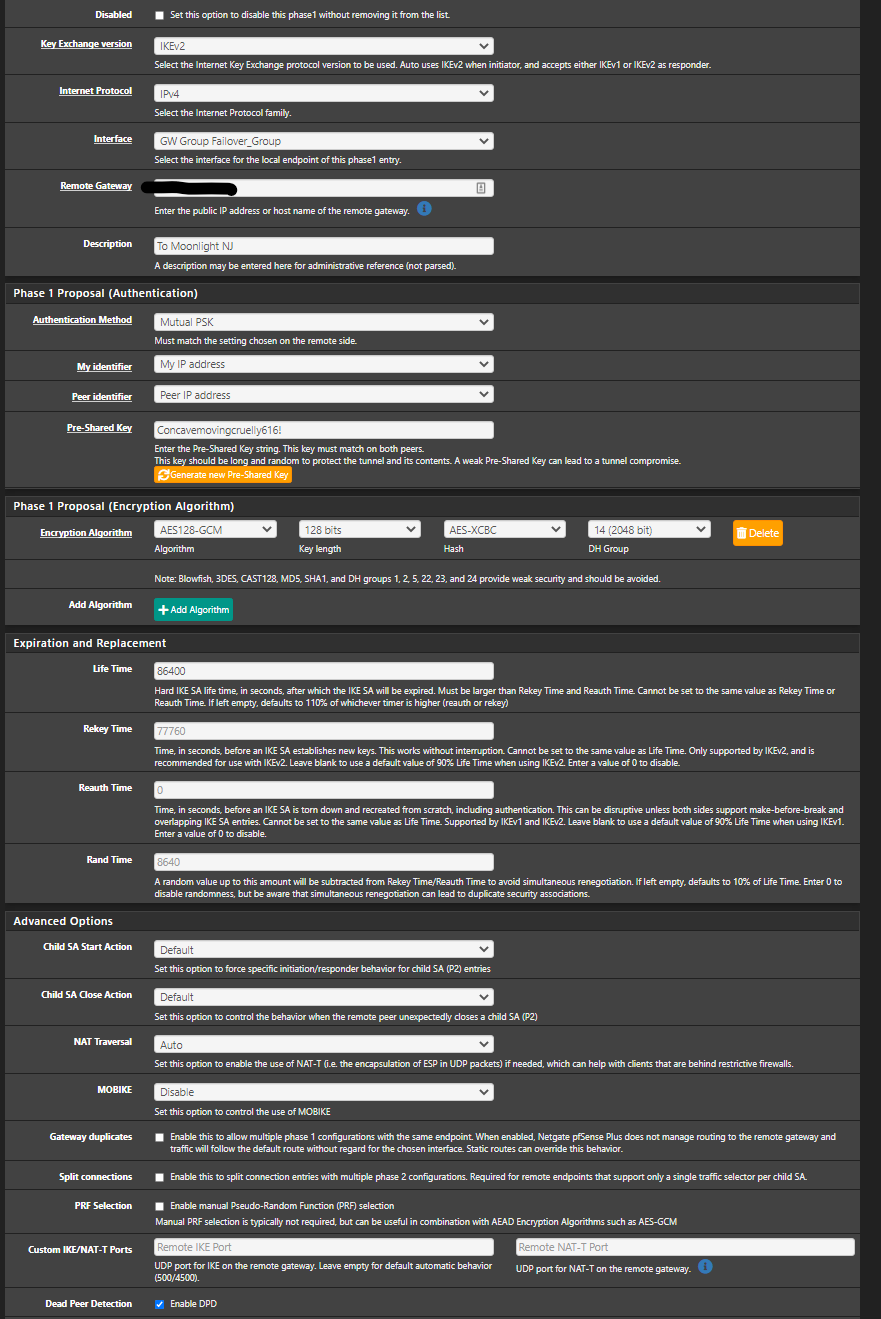
Alright, Incoming images.Office Side:
P1
P2
Remote Side:
P1
P2
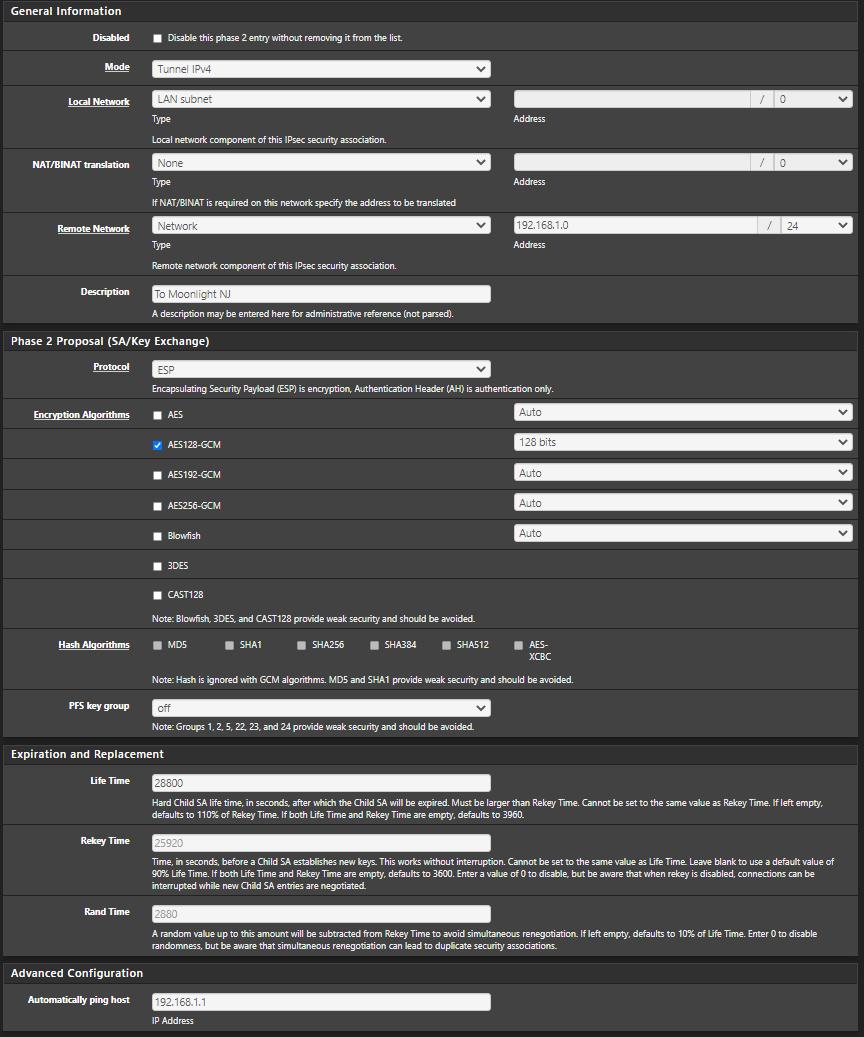
I also reviewed the link you sent. And it looks like ive got those settings set as well.
Thank you.
-
You'll want to change that PSK immediately, probably should have redacted that or omitted it from the screenshots.
-
Otherwise the tunnel config looks OK, so I'd focus on the other parts surrounding it -- nudging packets to be smaller via MSS, maybe try forcing NAT-T in case your ISP in one or both sides (or in between) is artificially limiting ESP traffic rates.
-
@jimp
Yip, Changing that now. Still asleep. -
Were you able to see any improvement here?
That's between New York and New Jersey? What latency do you see across the tunnel?
I would certainly expect to see more than 85Mbps provided the WAN connections at each end allow it.
Steve