pfsense is online - no internet to clients
-
Hi
ISP router on 192.168.1.1/24 gives pfsens box adress 192.168.1.114.
Pfsense box deliver DHCP 192.168.0.1/24 to clients(ISP router dont have bridge mode.)
Here is my setup:
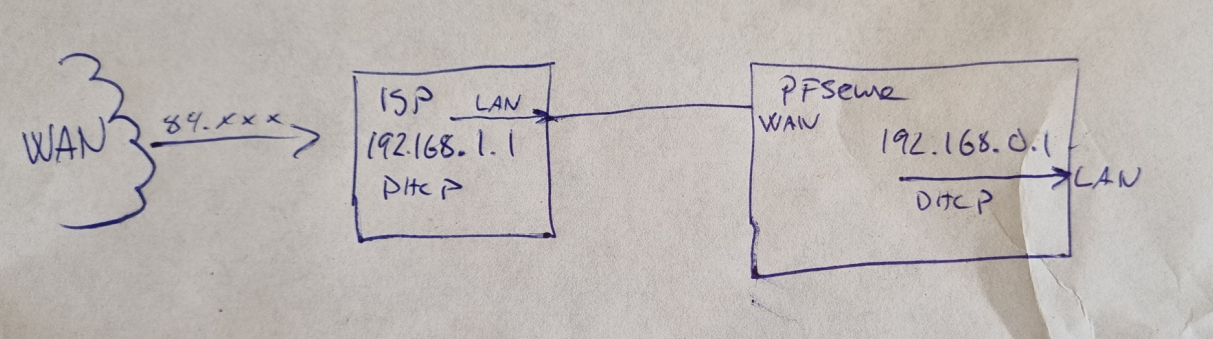
in pfsense i see this:
A ping from pfsense to cnn.com= 100% packet loss.
Any ideas?
Thanks up fromt!
-
@modesty said in pfsense is online - no internet to clients:
Any ideas?
Your pfSense WAN needs to receive packets from the RFC 1918 addresses range (ISP router lan port 192.1.1) which is blocked it you check that option
Goto Interface -> WAN -> un-check "Block private networks and loopback addresses"Btw you have set up a double NAT. Do you need the ISP router, or can you put it in bridged mode?
-
-
-
@modesty said in pfsense is online - no internet to clients:
I had blocked private networks in WAN.
Thanks!That is default, but that is only blocks source port inbound traffic. Had you created your own rule in say outbound direction via floating?
The rfc1918 block on wan that is there out of the box only blocks unsolicited inbound traffic from a rfc1918 source. That would not stop you from using the internet in a double nat setup like you show.
-
@johnpoz said in pfsense is online - no internet to clients:
The rfc1918 block on wan that is there out of the box only blocks unsolicited inbound traffic from a rfc1918 source. That would not stop you from using the internet in a double nat setup like you show.
John is not wrong here (never thought he was, but had to check for myself), so I did a pfctl -sr on one of my devices just to see what the rules are.
And of course they look like this:
block drop in log quick on igb0 inet from 10.0.0.0/8 to any label "Block private networks from WAN block 10/8"
block drop in log quick on igb0 inet from 127.0.0.0/8 to any label "Block private networks from WAN block 127/8"
block drop in log quick on igb0 inet from 172.16.0.0/12 to any label "Block private networks from WAN block 172.16/12"
block drop in log quick on igb0 inet from 192.168.0.0/16 to any label "Block private networks from WAN block 192.168/16"So they all have a direction component of the rules.
Assuming you need to do DHCP to the router, the normal rules allow that, they keep state, so responses should be fine.
The pass rules for DHCP are above the blocks, also have a "quick" so that should be working.Unless there is something else going on.
It would also be an easy test if you wanted to.
-
@mer hehe - if they blocked rfc1918 any traffic on the wan out of the box. They would have shitton of users complaining pfsense didn't work.
I bet there is a huge percentage of pfsense users that are double natting..
-
@johnpoz No doubt. I did at one point simply because I was lazy and didn't trust comcast to do the right thing if I swapped out a wrt54g. In my case, it actually saved me because my sg2440 fell victim to the red led of death, so moved one cable, rebooted wifes stuff and minimal downtime.
(that sg2440 was fixed under RMA and has been working fine, but I've got a 5100 on order just in case).I always liked seeing the rules as applied (pf user before pfSense), that command helps me figure out exactly what is going on, you can mentally walk a packet flow.