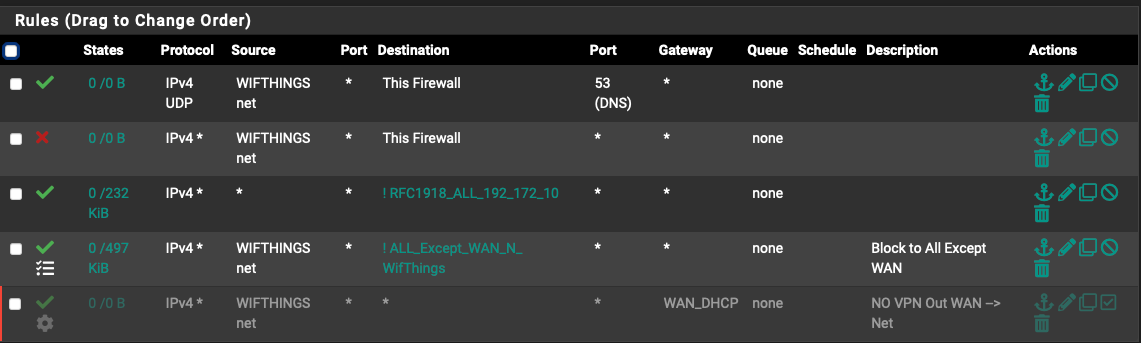
Help please: Why are these rules isolating IoT not working?
-
This post is deleted! -
@rennit I would have to do some testing. As I mentioned I do not log default, and I don't have that unchecked because I do use some IPv6.
Not sure where the rule for blocking ipv6 goes in the stack - might before interface rules. If that is the case you might have to use floating rules to not log it.. When get a chance will do some testing and let you know.
Keep in mind - that unless you have rules to allow IPv6 - that being checked ipv6 still wouldn't work since default is deny.. So ipv6 could never work unless you actually have rules that allow it.. So if that block rule is causing log spam - you could check it and then just don't allow IPv6, this way for sure any rules you put in interface to not log IPv6 would work.
-
Appreciate that, but do not want you to go out of your way more than you already do. Is there a way to not log with that box unchecked?
@johnpoz From note below regarding edit: Okay, when you say do not allow, do you mean not have any explicit Pass rules or create active block rules? Or how does one actively make sure that IPv6 is not allowed universally? Just not clear on where or what to do for that last suggestion, but it sounds like what I want to do.
-
@rennit see my edit to post above..
-
@rennit said in Help please: Why are these rules isolating IoT not working?:
Okay, when you say do not allow
The default rule is always deny.. They are just not shown in the gui list of rules. If you do not have a rule on an interface or floating tab that "allows" something - then it will be denied. No need for a specific deny rule - unless you want to log it, or not log it or reject vs just drop.. Or depending on what your wanting to allow calls for specific block in the rule order. Say for example you want to only allow icmp to some specific vlan or dest, or only from specific host to internet.. You would need a specific deny between that rule and the default any any rule at the bottom of the rule list.
If you do not have an allow rule on lan for example that allows for IPv6 - then even if client has IPv6 address.. He isn't getting off his own network through pfsense using it.. So its really not a requirement to uncheck that box to specifically create block rules for ipv6.
-
Got it. Perfect sense. I am going to check that box then verify I have nothing that allows IPv6 on any interface.
Once that is complete, is there any place I could look or diagnostic to run to both learn, and verify that IPv6 traffic is being ignored or is it more of a 'trust the software'? There is a ton of that IPv6 noise...
Does this also work for WAN, should I place that rule? Then when needed make it just IPv6...
WAN Interface
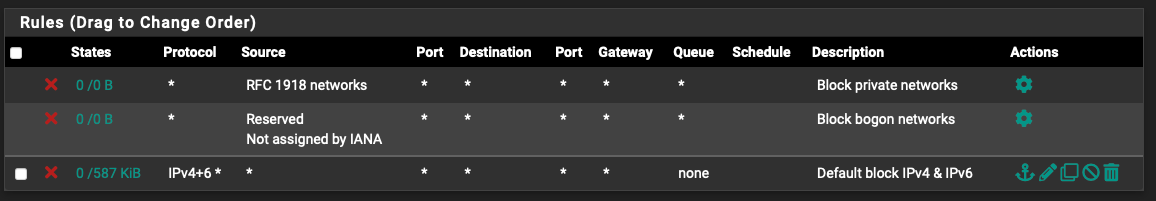
-
@rennit the default deny is EVERY interface on pfsense - so yeah even wan..
Those rules are defaulted there, in case you create allow rules or port forward that create wan rules.. Because you would want to block them from your allow rules.
There is no point to that rule you added - unless you don't want to log stuff hitting your wan.
-
Okay. Thank you! So I am back to check the box and verify nothing set to pass/allow.
Appreciate you taking the time on the explanations.
-
@rennit said in Help please: Why are these rules isolating IoT not working?:
Appreciate you taking the time on the explanations.
NP - I like to help people, and nothing better than when the light bulb clicks.. And such discussions are normally helpful for others as well.
-
Absolutely. I am really getting all you are teaching me and extrapolating to figure other things out as well.
Agreed. I'm trying to take the approach of doing this to help future readers as well. I especially relate after searching a lot of forum posts and other research sources. Seems the thread is being viewed a bit for being so new, that's also why kept some of this discussion here. An issue in some of my research has been lack of continuity with bits and fragments of solutions scattered in may posts and blogs etc.
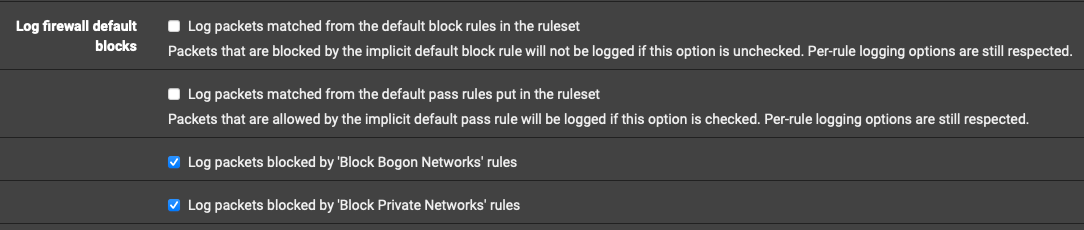
@johnpoz edit: On that note... With this being the box we are referring to:

Saying all blocked unless checked, meaning when checked traffic not blocked, BUT the traffic will not actually egress or ingress without a specific pass rule allowing it. Is that correct?
-
Very thankful for this discussion. Provided a much greater understanding of many things and overall.
For those reading: As to this specific issue, one that I saw many posts about, but this solution I have not seen:
Just found this under logs-->firewall-->settings. I tested it and worked for the noise. Just don't know if will be losing any other and important logging with it. Looking at default block rules I do not think so, but not sure.