pfSense 2.4.2 - State reset to wrong interface
-
Hey there,
First of all I don't know exactly where should I ask but I did my own search and can't find anything. It's been a while I'm having this issue but I have now to find a solution quickly.
Anyways, I have roughly 30 pfSense on sites with Aruba controller's and a main office with pfSense and Master Aruba controller.
Each time there is a power outage from a site and the pfSense needs to reboot, it then creates a wrong state to the Aruba.There are 2 states from Diagnostic > States :
Source = Aruba Controller IP ( on site ) on port #4500
Destination = Master Aruba controller IP ( at main office ) on port #4500
Protocol = udp
Interface = Must be through OVPNC3 ( not WAN ).The other one is the same instead it goes through LAN for the interface and this one always works.
The issue there is that when the on site pfSense reboot, it creates both states again but rather using the interface OVPNC3, it creates a state on WAN, therefore the state between both Aruba site controller and Aruba Master @main office are not working at all.
To fix the problem I've to kill the WAN state and then it automatically connects through the correct one which is OVPC3.
I first thought it was an issue with Aruba using the 6.4 version, but I recently upgrade all my Aruba's to 8.6 and the problem is still occurring.
Do you guys have any solution for that matter ? or maybe a hint that I could look into ?
Thank you very much!
-
You are using IPSec over OpenVPN? Fun! But should work fine.
You should upgrade, 2.4.2 is ancient relatively!
I assume the destination IP is a private address at the main office?
That is happening because the on site controller is trying to open the tunnel before the OpenVPN has come up and hence before there is a route to it in place.I would add an floating outbound reject rule on the WAN for that IP to prevent it opening a state there.
Steve
-
@stephenw10 Thanks a lot for your reply.
I was planning on upgrading soon nevertheless it's been since couple of pfSense version I'm having this same exact issue.
Indeed the destination IP is the Aruba master controller private IP at the main office.
Would you mind elaborate on the meaning of "adding a floating outbound reject rule on the wan" ? I'm sorry I'm not familiar with it ?
Cheers,
-
Only floating rules can be added outbound so you need to add it there.
Set it as reject so client sees that immediately. Though here it's UDP so that doesn't matter.
Set it as quick (another floating only option) so other rules are not matched.So something like:
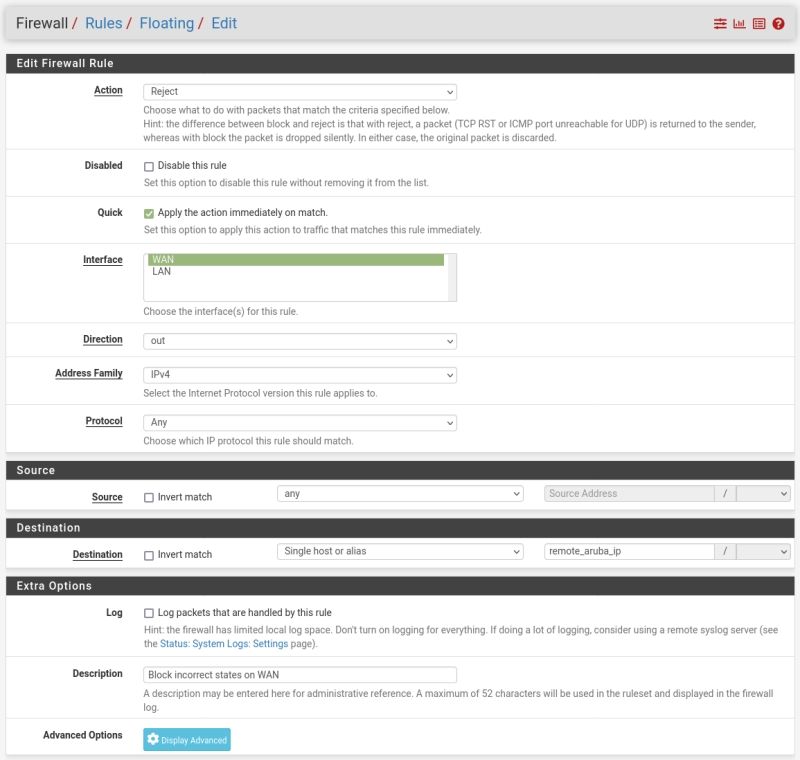
You could set it for UDP 4500 only but there's no reason any traffic for that IP should leave the WAN directly.
Steve
-
@stephenw10 I did some reading on floating rules, I wasn't aware of that feature.
That's great, thank you very much!