Routing internal networks out the wan
-
I am currently in the process of upgrading a working EdgeRouter(but old) with the NG-1100. however, I am not able to get the internal subnets routing out to the WAN. This is all working on the EdgeRouter by simply adding static routes on the LAN side ie
192.168.3.0/24 192.168.1.3 which is what I will keep using until I can figure out how to fix/learn the configuration of the netgate.I will admit this is my first experience with pfSense/netgate so I don't know if something else needs to be started/stopped/configured Any help will be greatly apricated. The below is a simple diagram of my setup.
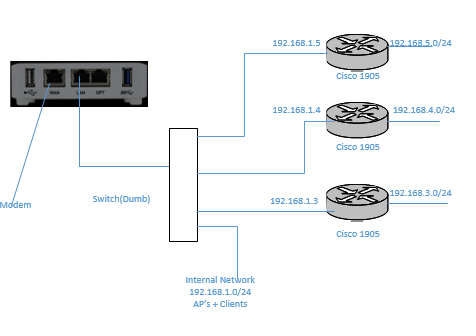
-
@jarhead5925 The Cisco units are all providing NAT to the networks behind them? The pfSense shouldn't even know about those networks, or need to. They should essentially be like any other LAN device going out. Can those networks ping the LAN IP of the pfSense?
-
@steveits The Cisco Routers are not providing NAT, the only NAT would be between the WAN port and the LAN of the NG. They are only providing a route to the NG 192.168.1.1 from the perspective subnet. If pfSence does not need to know about those networks how would the ng1100 know to hand off that traffic to the respective router?? No, the netgate does not answer the echo request sent to it from the other networks, a packet sniffer on each of the lines going to the NG does show the routers sending the echo request and the ng is not responding to those requests. Again I just want this to work in the same manner as the EdgeRouters and no double NAT. Should be as simple as adding a static route to the respective network into the NETGATE like in windows "route add 192.168.5.0 mask 255.255.255.0 192.168.1.5" ubuntu "route add -net 192.168.5.0 netmask 255.255.255.0 gw 192.168.1.5" or cisco 'ip route 192.168.5.0 255.255.255.0 192.168.1.5" also the same on the edgerouter, attached is the static route on the NG but it is not working "I DO KNOW the ip address does not match my original diagram as I am using a spare router for this setup until it can work, then I can reconfigure to replace the edgerouter.
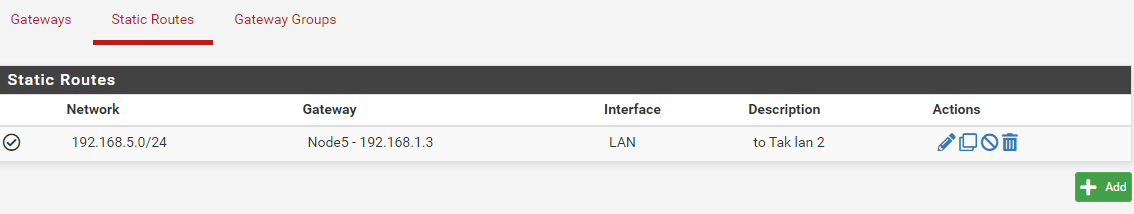
-
@jarhead5925 so on pfsense lan did you allow for those downstream networks - default would be any any with lan net as source. 192.168.5 is not your lan net.. So you would have to adjust your rule on lan to allow for those downstream networks.
And seems you also have hosts on 192.168.1 (lan) this is going to be asymmetrical problems. You should connect your downstream networks via a transit network (no hosts on it)..
Unless your clients on lan and downstream network devices never talk to each other..
When you create the route to the downstream network, pfsense should auto add those networks to your outbound nat (unless you changed that from auto).. But you would have to adjust your lan rules to allow for any downstream networks using lan as the transit connection.
-
@johnpoz "When you create the route to the downstream network, pfsense should auto add those networks to your outbound nat "
here are the auto-created rules
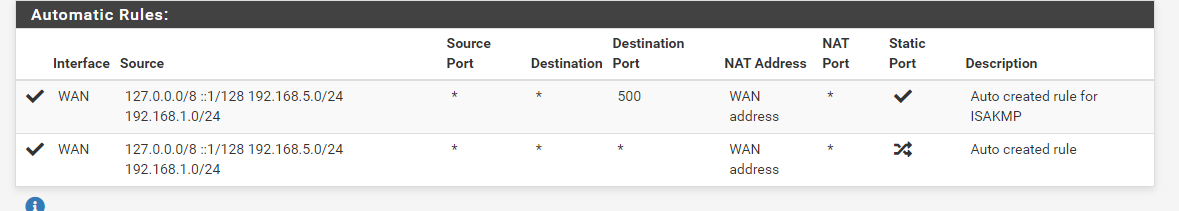
I do not currently have
'But you would have to adjust your lan rules to allow for any downstream networks using lan as the transit connection.'
Are these the rules that need to be adjusted?
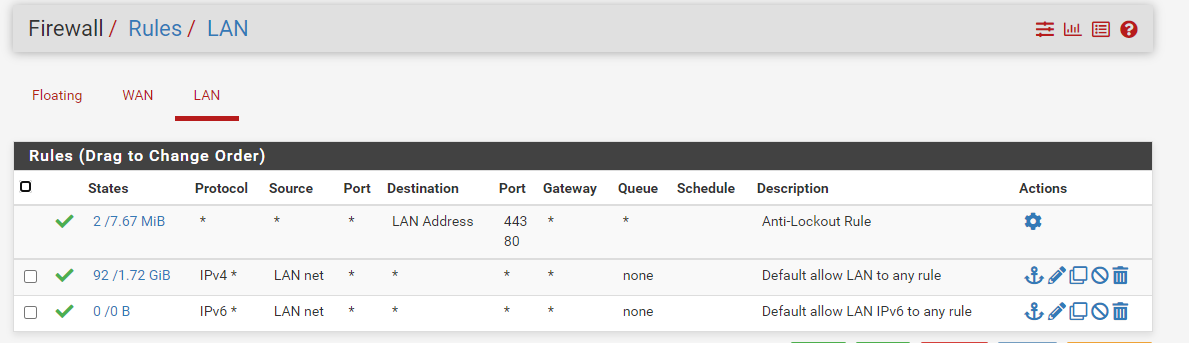
-
@jarhead5925 said in Routing internal networks out the wan:
Are these the rules that need to be adjusted?
Yes.. So your lan is 192.168.1/24 - and your lan rules say "lan net" as source.. So if something from 192.168.5 comes in via lan - it wouldn't be allowed.
Adjust your lan rules to allow the networks your downstream network will be on, you can either adjust the any any rule to allow via cidr that includes your lan and all downstream networks, say 192.168/16 or create new rules that account for your downstream networks. A /21 would work for example this would be 192.168.0.1 to 192.168.7.254, if the highest downstream network is .5 as you have shown.
You could for example create an alias that includes all your lan and the downstream networks 192.168.3/24, 192.168.4/24, etc.. and use that as source on your allow rule.. There are many ways to skin this cat. But currently your lan rules do not allow your downstream networks - so no its not going to work.
You could just add rules for all your downstream networks 192.168.5/24, etc.
But again I want to point out - since it seems like you have clients on your lan - you show that AP, etc. If devices from lan and downstream networks want to talk to each other your going to run into asymmetrical traffic.. Which is going to be very problematic..
Routers should be connected via transit network (no hosts on it) so you never have asymmetrical flow. Or you need to host route on all the devices that live on the transit network, or you need to nat on the downstream routers. If lan devices and downstream devices will not ever need to talk to each other - then its ok.. But if they do your going to have problems with how your network is shown.
Another option would be to get rid of that dumb switch and use vlan capable switch and then put all these networks on their own network/vlan on pfsense.. This would prevent asymmetrical traffic flow, and give you the ability easy firewall between your networks at pfsense.
-
I believe the correct fix for this is to understand that the Netgate device is a POS. And to just upgrade the existing EdgeRouter that has been performing as configured for 3 years WITHOUT an issue.
-
@jarhead5925 what?
So your edge router that most likely just allowed all networks which is why it would worked.. Ok yeah pfsense is a pos because it requires their users to actually understand how firewall works, and correctly configure.
Your more than welcome to use whatever you want other than netgate/pfsense - have fun!
This sure isn't rocket since.. The lan rule default to only "lan net" as source - so no shit you would have to allow for non "lan net" networks if you want to use those..
-
@johnpoz Thank you for your reply it really does speak volumes on how customer service should work and should be highlighted as a shining example of what Netgate has to offer!!!!
-
Well that escalated quickly!
You just need a firewall rule to pass the traffic from 192.168.5.0/24 since that is not in the LAN subnet. pfSense only default firewall rule is for the LAN subnet. Anything else you wish to pass requires rules adding.
Did that not work when you added it?Steve